New ENCOR Questions 1
Question 1
An engneer must export the contents of the devces object n JSON format. Whch statement must be use ?
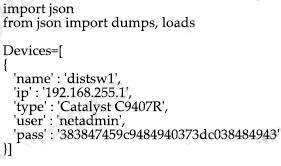
- json.print(Devices)
- json.loads(Devices)
- json.dumps(Devices)
- json.repr(Devices)
Answer: C
Question 2
What s the functon of Csco DNA Center n a Csco SD-Access deployment?
- It is responsible for routing decisions inside the fabric
- It is responsible for the design, management, provisioning, and assurance of the fabric network devices
- It possesses information about all endpoints, nodes, and external networks related to the fabric
- It provides integration and automation for all nonfabric nodes and their fabric counterparts
Answer: B
Question 3
Refer to the exhbt.

An engneer troubleshoots connectvty ssues wth an applcaton. Testng s performed from the server gateway, and traffc wth the DF bt set s dropped along the path after ncreasng packet sze. Removng the DF bt settng at the gateway prevents the packets from beng dropped. What s the cause of ths ssue?
- PMTUD does not work due to ICMP Packet Too Big messages being dropped by an ACL
- The remote router drops the traffic due to high CPU load
- The server should not set the DF bit in any type of traffic that is sent toward the network
- There is a CoPP policy in place protecting the WAN router CPU from this type of traffic
Answer: C
Question 4
Refer to the exhbt.

A network engneer must confgure a password expry mechansm on the gateway router for all local passwords to expre after 60 days. What s requred to complete ths task?
- Add the username admin privilege 15 common-criteria-policy Administrators password 0 Cisco013579! command
- No further action is required. The configuration is complete
- Add the aaa authentication enable default Administrators command
- The password expiry mechanism is on the AAA server and must be configured there
Answer: A
Question 5
Refer to the exhbt.
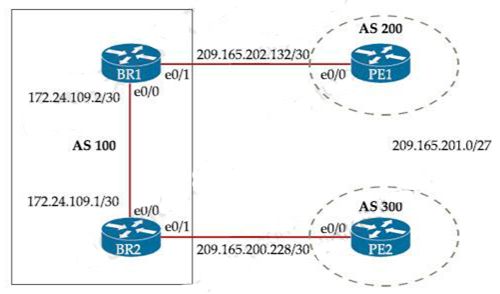


Whch confguraton change wll force BR2 to reach 209.165.201.0/27 va BR1?
- Set the origin to igp on BR2 toward PE2 inbound
- Set the local preference to 150 on PE1 toward BR1 outbound
- Set the weight attribute to 65,535 on BR1 toward PE1
- Set the MED to 1 on PE2 toward BR2 outbound
Answer: D
Question 6
What are two benefts of YANG? (Choose two)
- It collects statistical constraint analysis information
- In enforces the use of specific encoding format for NETCONF
- In enforces configuration semantics
- It enables multiple leaf statements to exist within a leaf list
- It enforces configuration constraints
Answer: B E
Question 7
Refer to the exhbt.
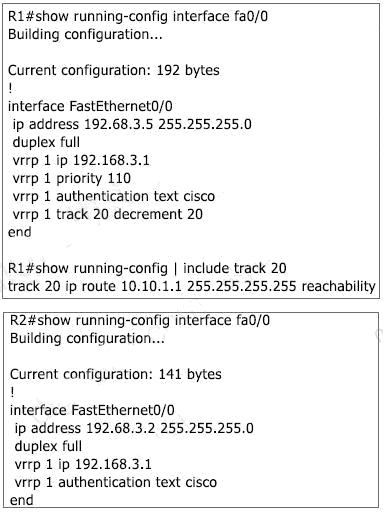
An engneer confgures VRRP and ssues the show commands to verfy operaton. What does the engneer confrm about VRRP group 1 from the output?
- There is no route to 10.10.1.1/32 in R2s routing table
- If R1 reboots, R2 becomes the master virtual router until R2 reboots
- Communication between VRRP members is encrypted using MD5
- R1 is master if 10.10.1.1/32 is in its routing table
Answer: D
Question 8
Refer to the exhbt.
flow record Recorder
match pv4 protocol
match pv4 source address
match pv4 destnaton address
match transport source-port
match transport destnaton-port
!
flow exporter Exporter
destnaton 192.168.100.22
transport udp 2055
!
flow montor Montor
exporter Exporter
record Recorder
!
et-analytcs
p flow-export destnaton 192.168.100.22 2055
!
nterface g1
p flow montor Montor nput
p flow montor Montor output
et-analytcs enable
!
An engneer must add the SNMP nterface table to the NetFlow protocol flow records. Where should the SNMP table opton be added?
- under the interface
- under the flow record
- under the flow monitor
- under the flow exporter
Answer: D
Question 9
Refer to the exhbt.
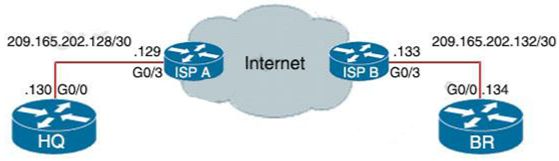
BR(confg)#nterface tunnel1
BR(confg-f)#keepalve 5 3
HQ(confg)#nterface tunnel1
HQ(confg-f)#keepalve 5 3
What s the effect of these commands on the BR and HQ tunnel nterfaces?
- The tunnel line protocol goes down when the keepalive counter reaches 6
- The keepalives are sent every 5 seconds and 3 retries
- The keepalives are sent every 3 seconds and 5 retries.
- The tunnel line protocol goes down when the keepalive counter reaches 5
Answer: B
Question 10
In Csco SD-WAN, whch protocol s used to measure lnk qualty?
- OMP
- BFD
- RSVP
- IPsec
Answer: B
Question 11
What s used to perform QoS packet classfcaton?
- the Options field in the Layer 3 header
- the Type field in the Layer 2 frame
- the Flags field in the Layer 3 header
- the ToS field in the Layer 3 header
Answer: D
Question 12
Refer to the exhbt.
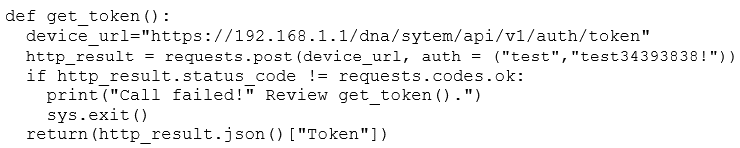
Whch HTTP code must be returned to prevent the scrpt from extng?
Answer: A
Question 13
Whch LISP component s requred for a LISP ste to communcate wth a non-LISP ste?
- ETR
- ITR
- Proxy ETR
- Proxy ITR
Answer: C
Question 14
What s a characterstc of a next-generaton frewall?
- only required at the network perimeter
- required in each layer of the network
- filters traffic using Layer 3 and Layer 4 information only
- provides intrusion prevention
Answer: D
Question 15
Whch technology s used as the bass for the Csco SD-Access data plane?
- IPsec
- LISP
- VXLAN
- 802.1Q
Answer: C
Question 16
HTTP/1.1 204 conten t s returned when cur -l -x DELETE command s ssued. Whch stuaton has occurred?
- The object could not be located at the URI path
- The command succeeded in deleting the object
- The object was located at the URI, but it could not be deleted
- The URI was invalid
Answer: B
Question 17
An engneer must provde wreless converge n a square offce. The engneer has only one AP and beleves that t should be placed t n the mddle of the room. Whch antenna type should the engneer use?















