STREET CRYPTOGRAPHY
A Quick and Dirty Way to Maintain Your Secret Conspiracy
By Christopher Forrest
Copyright 2012 Christopher Forrest
Smashwords Edition
Smashwords Edition, License Notes
This ebook is licensed for your personal enjoymentonly. This ebook may not be re-sold or given away to other people.If you would like to share this book with another person, pleasepurchase an additional copy for each recipient. If youre readingthis book and did not purchase it, or it was not purchased for youruse only, then please return to Smashwords.com and purchase yourown copy. Thank you for respecting the hard work of thisauthor.
Permission is also granted for the owner ofthis purchased or gifted copy to print one(1) copy of this ebookfor one's personal use. For further permissions, please contact theauthor.
Table of Contents
Appendix C:Checkerboard Variations
INTRODUCTION
Ok, you have a conspiracy going. You have secret goals andoperations going out in all directions. At first, you met face toface with all members of your group, and that worked. Things havechanged. You now need a way to secretly deliver a message tosomeone you won't meet on a regular basis. Congratulations, youpicked up the right book.
Before I show you a good way to put togetheryour cipher, I'm going to bore you with the details of why youdon't want to use certain other ciphers.
PART I
SUBSTITUTION CIPHERS
Chapter 1
The Caesar Cipher
Thisis, historically, the oldest cipher known to modern man. Its agealone should tell you that it has been beaten, to death,repeatedly. You can even check the New York Times puzzle section tosee examples given to be cracked as a game. Long story short, DON'TUSE IT.
Now that I've gotten that out of the way, howabout we take a look at what the Caesar Cipher actually is?
Julius Caesar was a renowned general, and heneeded to get secrets across to his captains and lieutenants. To dothis, he used this cool little cipher to thwart interception of hisorders, battle plans, and general information by the enemy.
How It Works
He took the Latin alphabet and would shift each letter by apredetermined number. The man in the field would have this numbermemorized so he could both read the message from his beloved leaderand send messages back, without worrying about interception. Thetranslation of such can be shown by Figure 1-1: CaesarCipher.
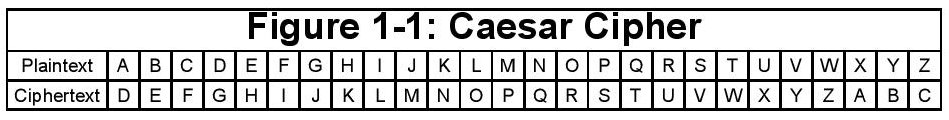
If he wanted to encode the message, "ATTACKAT DAWN", we'd end up with, using Figure 1-1:
DWWDFN DW GDZQ
When the field commander got that message, hecould create a table for deciphering the message and clearly readthat his commander wanted him to attack at dawn.
Now the field commander has received themessage and wants to send a reply. He remembers the shift of 3, andquickly composes a message back to his leader. The messagereads:
ZH DUH DW WKH JDWH GR BRX ZDQW WKHLU OHDGHU DOLYH RU GHDG
Caesar reads this and is pleased, so hecomposes a message back to his field commander that reads:
WKHLU OHDGHU ZLOO PDNH DQ HAFHOOHQW WURSKB HLWKHU ZDB WDNH KLPDOLYH LI SRVVLEOH EXW EULQJ KLV ERGB LI QRW
After the battle, Caesar crowns his captainwith a crown of grape leaves and gives him acres of farmland andgold. What do you think happened?
Crypto analyzing the Caesar Cipher
Now that you can see how the cipher works, let's discuss why youshouldn't use it.
First, there exist only 25 different keys fora Caesar Cipher, considering that the number memorized is theshift. With that in mind, one can feasibly generate 25 copies ofyour message, each with a different shift, and see which one youused. This would allow an antagonist to know everything you wantedto keep secret from him/her in one tedious afternoon. The onlyreason it worked for Caesar is: most of his enemies wereilliterate, just as most of his soldiers. Were it not for a fewliterate generals that he campaigned against, as well ascompetitive legions owned by other Roman generals, he could verywell have written his orders in plain text and never needed acipher.
What if you decide to scramble the alphabet?It doesn't matter. As a simple substitution cipher, it is prone tofrequency analysis. This means: if the opposing party has aninkling which language you're using, they can use conventions ofthat language against you. They may not decipher the first message,but given enough messages, they will have you, and they likelywon't be nice enough to tell you so before they lay waste to yourplans.
For a detailed introduction to cryptanalysis,I recommend US Army FM 34-40-2, Basic Cryptanalysis.
Chapter 2
The Polybius Square
It issaid the god Hermes brought cryptology to the Greeks. A commonsubstitution cipher known to have been widely used by various Greekcity-states is the Polybius Square or Polybius Cipher.
This cipher, like the Caesar Cipher, is asimple substitution cipher. Unlike the Caesar Cipher, this one usesa grid of numbers to encode the message. An example is given asFigure 2-1.
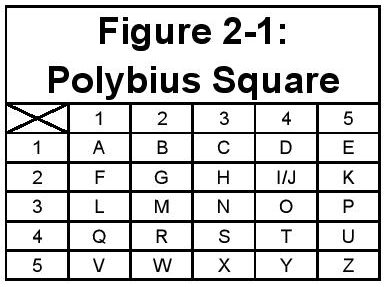
How It Works
If, as before, a general wanted to order one of his captains toattack at dawn, the general would locate the letter on the grid,and then read off the row then column the letter was placed in tofind the two digit code for the letter. The encoded message wouldappear as shown on Figure 2-2.
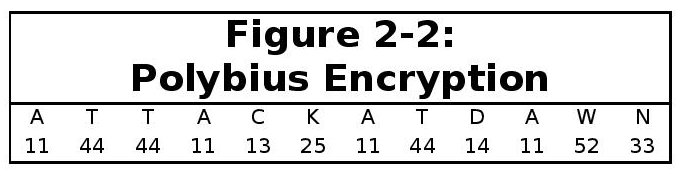
The captain would get this stream of numbers,and would use the square to look up the letters in the message bytaking the first number for each pair as the row number, and thenhe would consider the second number of each pair to be the columnnumber.
Leonidas is rallying his allies againstPersia. He composes a message to his friends in Athens:
13343215311544454321242223445315425315431144442315423234355431111511331443443435232432214234324411252433221131313421224215151315
His allies in Athens read this message andare emboldened, writing this reply:
5215522431313334443433315443443435232432214234324411252433221131313421224215151315521552243131434434352324322142343244112524332211335434212242151513151143232443345233
As we all know, braggadocio has limitedeffectiveness in a suicide mission.
Obviously, this is a vastly simplifiedexample, but you see how this could be expanded and used to securecommunications.
Why You Shouldn't Rely on This
As I said before in reference to the Caesar Cipher, this is asimple substitution cipher. While the jumble of numbers may appearmore secure at first, and, marginally, it is. This will not fool anantagonist for long. The jumble of numbers, each numbered from 1-5,will give this cipher away as some type of grid substitution cipherin minutes. After this fact becomes apparent, a simple frequencyanalysis will give your message away in days at best, hours atworst, even if the antagonist is working by hand. I've seen one ofthese ciphers broken in milliseconds with modern computerhardware.
Chapter 3
Just For Fun
OK, wecovered a few serious classical substitution ciphers in theprevious two chapters, but let us have a little fun. Don't take anyof the ciphers in this chapter seriously, and I'll tell you why,but here's a couple that amuse me from time to time.
Next page