David Coffin [David Coffin] - Expert Oracle and Java Security: Programming Secure Oracle Database Applications with Java
Here you can read online David Coffin [David Coffin] - Expert Oracle and Java Security: Programming Secure Oracle Database Applications with Java full text of the book (entire story) in english for free. Download pdf and epub, get meaning, cover and reviews about this ebook. year: 2011, publisher: Apress, genre: Computer. Description of the work, (preface) as well as reviews are available. Best literature library LitArk.com created for fans of good reading and offers a wide selection of genres:
Romance novel
Science fiction
Adventure
Detective
Science
History
Home and family
Prose
Art
Politics
Computer
Non-fiction
Religion
Business
Children
Humor
Choose a favorite category and find really read worthwhile books. Enjoy immersion in the world of imagination, feel the emotions of the characters or learn something new for yourself, make an fascinating discovery.
- Book:Expert Oracle and Java Security: Programming Secure Oracle Database Applications with Java
- Author:
- Publisher:Apress
- Genre:
- Year:2011
- Rating:4 / 5
- Favourites:Add to favourites
- Your mark:
Expert Oracle and Java Security: Programming Secure Oracle Database Applications with Java: summary, description and annotation
We offer to read an annotation, description, summary or preface (depends on what the author of the book "Expert Oracle and Java Security: Programming Secure Oracle Database Applications with Java" wrote himself). If you haven't found the necessary information about the book — write in the comments, we will try to find it.
Expert Oracle and Java Security: Programming Secure Oracle Database Applications with Java provides resources that every Java and Oracle database application programmer needs to ensure that they have guarded the security of the data and identities entrusted to them. Youll learn to consider potential vulnerabilities, and to apply best practices in secure Java and PL/SQL coding. Author David Coffin shows how to develop code to encrypt data in transit and at rest, to accomplish single sign-on with Oracle proxy connections, to generate and distribute two-factor authentication tokens from the Oracle server using pagers, cell phones (SMS), and e-mail, and to securely store and distribute Oracle application passwords.
Early chapters lay the foundation for effective security in an Oracle/Java environment. Each of the later chapters brings example code to a point where it may be applied as-is to address application security issues. Templates for applications are also provided to help you bring colleagues up to the same secure application standards. If you are less familiar with either Java or Oracle PL/SQL, you will not be left behind; all the concepts in this book are introduced as to a novice and addressed as to an expert.
Helps you protect against data loss, identity theft, SQL injection, and address spoofing
Provides techniques for encryption on network and disk, code obfuscation and wrap, database hardening, single sign-on and two-factor
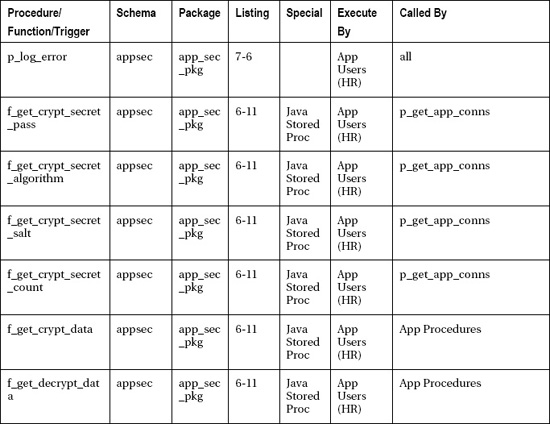
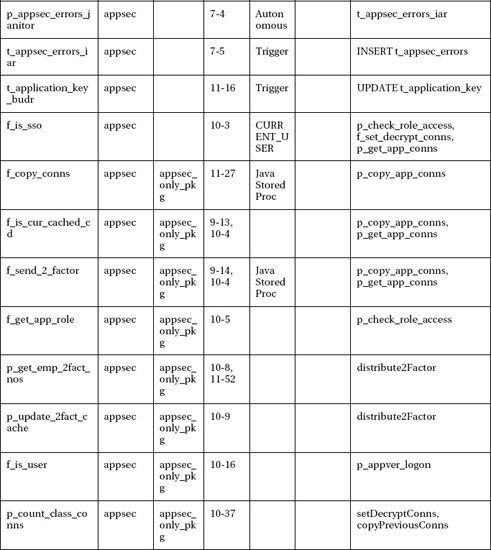
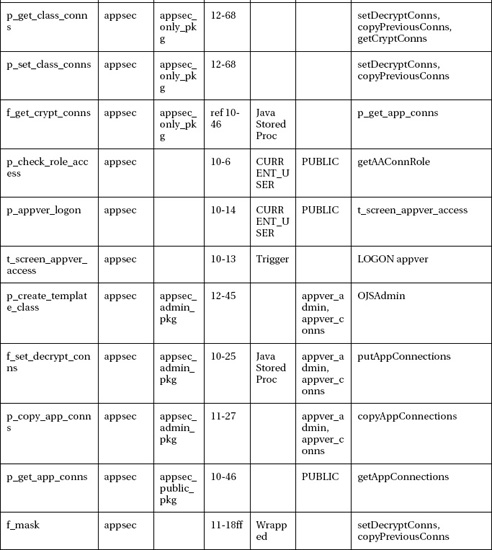
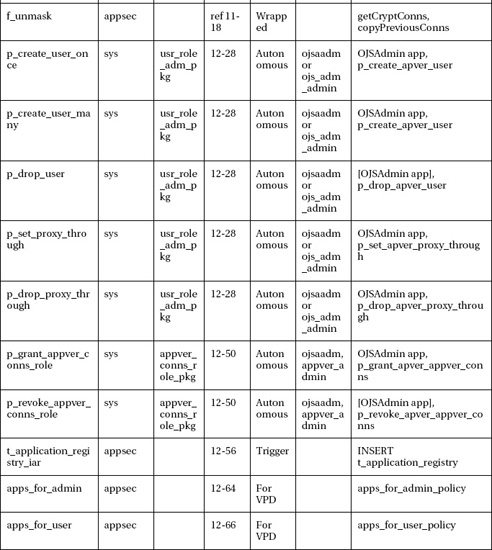
Provides what database administrators need to know about secure password distribution, Java secure programming, Java stored procedures, secure application roles in Oracle, logon triggers, database design, various connection pooling schemes, and much more
What youll learn
Guard against data loss, identity theft, SQL Injection, and to address spoofing
Protect sensitive data through encryption, both on disk and on the wire
Control access to data using secure roles, single sign-on, proxy connections, and two-factor authentication
Protect sensitive source ode through randomization, obfuscation, and wrapping
Thwart attempts at SQL injection and other common attacks
Manage constraints on the visibility of data and the scope of access
Who this book is for
Expert Oracle and Java Security: Programming Secure Oracle Database Applications with Java is for every Java developer who uses an Oracle database. It is also for every Oracle database administrator or PL/SQL programmer who supports Java client and web applications. Whatever role you play in developing and supporting Java and Oracle applications, you need to address computer, application, data, and identity security. This book offers the tools youll need to effectively manage security across all aspects of the applications you support.
David Coffin [David Coffin]: author's other books
Who wrote Expert Oracle and Java Security: Programming Secure Oracle Database Applications with Java? Find out the surname, the name of the author of the book and a list of all author's works by series.

![David Coffin [David Coffin] Expert Oracle and Java Security: Programming Secure Oracle Database Applications with Java](/uploads/posts/book/119377/thumbs/david-coffin-david-coffin-expert-oracle-and.jpg)












 David Coffin has over 30 years' experience in multi-platform network integration and systems programming. He has worked for large government contractors throughout his career. As a perpetual student, he has earned one Master's degree and has started a couple others. As a family man, he has raised eight children. David is a tri-athlete and distance swimmer who competes in the middle of the pack. He is also a classical guitar player, but he's not quitting his day job.
David Coffin has over 30 years' experience in multi-platform network integration and systems programming. He has worked for large government contractors throughout his career. As a perpetual student, he has earned one Master's degree and has started a couple others. As a family man, he has raised eight children. David is a tri-athlete and distance swimmer who competes in the middle of the pack. He is also a classical guitar player, but he's not quitting his day job.