Nicholas Brown - Nmap7: From Beginner to Pro
Here you can read online Nicholas Brown - Nmap7: From Beginner to Pro full text of the book (entire story) in english for free. Download pdf and epub, get meaning, cover and reviews about this ebook. year: 2019, genre: Computer. Description of the work, (preface) as well as reviews are available. Best literature library LitArk.com created for fans of good reading and offers a wide selection of genres:
Romance novel
Science fiction
Adventure
Detective
Science
History
Home and family
Prose
Art
Politics
Computer
Non-fiction
Religion
Business
Children
Humor
Choose a favorite category and find really read worthwhile books. Enjoy immersion in the world of imagination, feel the emotions of the characters or learn something new for yourself, make an fascinating discovery.

- Book:Nmap7: From Beginner to Pro
- Author:
- Genre:
- Year:2019
- Rating:4 / 5
- Favourites:Add to favourites
- Your mark:
- 80
- 1
- 2
- 3
- 4
- 5
Nmap7: From Beginner to Pro: summary, description and annotation
We offer to read an annotation, description, summary or preface (depends on what the author of the book "Nmap7: From Beginner to Pro" wrote himself). If you haven't found the necessary information about the book — write in the comments, we will try to find it.
Nmap7: From Beginner to Pro — read online for free the complete book (whole text) full work
Below is the text of the book, divided by pages. System saving the place of the last page read, allows you to conveniently read the book "Nmap7: From Beginner to Pro" online for free, without having to search again every time where you left off. Put a bookmark, and you can go to the page where you finished reading at any time.
Font size:
Interval:
Bookmark:
Nmap 7
From Beginner to Pro
Nicholas Brown
COPYRIGHT
Sold by: Amazon Digital Services LLC
Publisher: Independently published
ISBN: 9781798727195
All characters and information in this publication, other than those clearly in the public domain, are fictitious and any resemblance to real persons, living or dead, is purely coincidental.
Copyright 2019 Nicholas Brown
Table of contents
Computer networks have become popular. Every organization has a computer network. This network is used for communications between the organizations internal users as well as for communications between the organizations internal users and those external to the organization. This means that the organization data is at risk. Any loopholes within the network can be identified by malicious users and exploited. This will disadvantage the organization greatly. This is why network administrators should scan such networks to identify any security loopholes within them and take the necessary action before it is late. Nmap is a great tool for network scanning. It can help one identify any security vulnerabilities associated with networks and hosts. This Book guides you on how to use Nmap. Enjoy reading!
Nmap (Network Mapper) is a free network discovery tool available in the market. It has become a popular tool for network administrators who need to map out their networks and run extensive network discoveries. With Nmap, a network administrator can be used to scan for live hosts in a network as well as open ports and operating systems.
Nmap is centered on a command line similar to the one provided by Windows but it also a graphical user interface for the most experienced users. To use Nmap, the user enters commands and runs scripts through a text-driven interface. The users can navigate through routers, firewalls, IP filters as well as other systems. Nmap was first designed and developed for enterprise-scale networks and it is capable of scanning thousands of interconnected devices.
Some of the common uses of Nmap include port scanning, OS detection, version detection and ping sweeps. Nmap uses IP packets to identify the hosts available in a network as well as the services and operating system running on them. Nmap can be used in various operating systems include Free BSD, Gentoo and Linux. The tool also has an extensive user support.
Nmap is available on the https://Nmap.org/download.html directory. One should download the right version based on the operating system they are using. The installation steps for Nmap are also different for the different operating systems. For the case of Windows, you have to download the .exe file with the Nmap tool then double click it so as to begin executing it. You will first be asked to agree to the licensing terms:
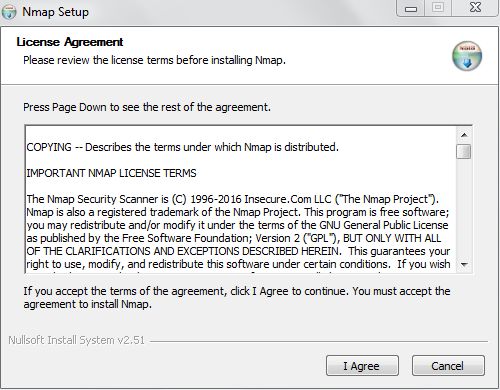
Next, you will be asked to choose the features which should be installed. It is good for you to leave it at the default setting then you click on Next:
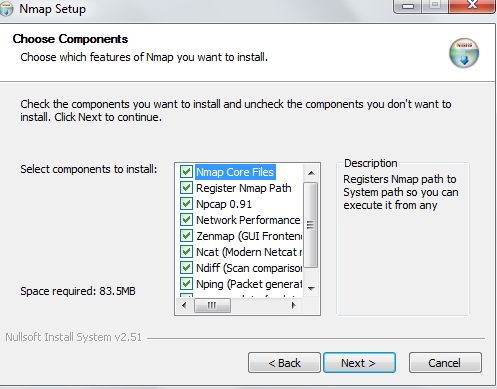
In the next window, choose the directory in which you want to install the Nmap then
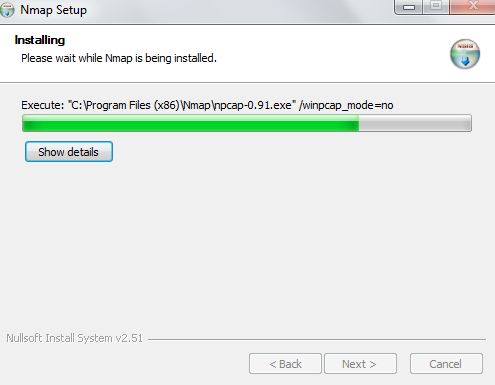
Click Install. The installation process will begin right away.
Note that the Nmap for Windows is not as efficient as the Nmap for Linux. Let us demonstrate how the Nmap can be installed and updated on the earlier versions of Kali Linux.
Before performing the update, first ensure that you have all the repositories in place. The following command can help you verify this:
cat /etc/apt/sources.list
The official repositories for Kali Linux 2.0 include the following:
deb http://http.kali.org/kali sana main non-free contrib
deb http://security.kali.org/kali-security sana/updates main contrib non-free
deb-src http://http.kali.org/kali sana main non-free contrib
deb-src http://security.kali.org/kali-security sana/updates main contrib non-free
The repositories for the older versions include the following:
deb http://http.kali.org/kali kali main non-free contrib
deb http://security.kali.org/kali-security kali/updates main contrib non-free
deb-src http://http.kali.org/kali kali main non-free contrib
deb-src http://security.kali.org/kali-security kali/updates main contrib non-free
If you dont have the above, then you can copy them and add them to the file sources.list which can be found in the /etc/apt/ directory. You can then update the package database for the OS by running the following command:
apt-get update
The update will take some minutes which will be determined by the number of updates to be done and the speed of your internet connection. Once the update is completed, you will be ready to install a newer version.
You only have to install the Nmap again. Using apt-get ill update the version you have to the latest version:
apt-get install Nmap
After the installation completes, verify the version that you have by using the V option as shown below:
Nmap V
Now that you have updated the Nmap package, you can go ahead and update the zeNmap package. To do this, launch the terminal then run the following command:
apt-get install zeNmap
During network administration, one of the basic tasks is to identify the hosts that are available or live in a network. With Nmap, we can achieve this by running a ping scan. With a ping scan, one can tell whether an IP address is online or not. It can be used as a host discovery method. Ping scans are used for detection of hosts that are within a network.
If you need to run an ARP (Address Resolution Protocol) scan, execute the following command. Note that after installing Nmap on your system, the terminal of your operating system will be able to recognize the Nmap command.
Nmap -sP 192.168.0.1/24
The command will return all hosts that responded to your ping requests together with the total number of IP addresses. Here is an example output from this command:
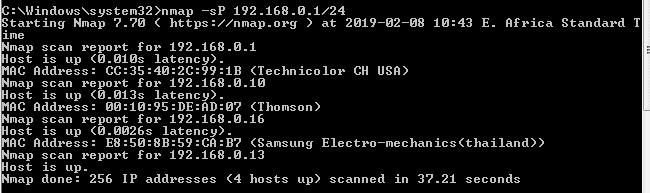
You should note that the search does not send any packets to above listed hosts. However, Nmap runs a reverse-DNS resolution on listed hosts so as to identify their names.
There are different Nmap techniques that you can use for port scanning. Here are the main techniques for this:
- sS TCP SYN scan
- sU UDP scans
- sT TCP connect scan
- sN TCP NULL
- sY SCTP INIT scan
Most new users like solving problems using SYN scans. However, as you become more experience with using Nmap, you will begin to use the other techniques as well. Note that you are only allowed to use a single port scanning method at a time. However, you are allowed to combine an SCTP and TCP scan.
This is a very quick way of scanning your ports on a network using Nmap. If the network is not protected by a firewall, you will be able to scan thousands of ports within a second. It is done as follows:
sS TCP SYN Scan
This type of scan does not complete connections with the network which can draw attention to your activity, which makes it a good technique for privacy. This type of scan works by sending a SYN packet and then waiting for response. If it gets an acknowledgement , this is treated as an open port while no response is treated as a filtered port. Non-listening ports are identified using a reset or RST.
Font size:
Interval:
Bookmark:
Similar books «Nmap7: From Beginner to Pro»
Look at similar books to Nmap7: From Beginner to Pro. We have selected literature similar in name and meaning in the hope of providing readers with more options to find new, interesting, not yet read works.
Discussion, reviews of the book Nmap7: From Beginner to Pro and just readers' own opinions. Leave your comments, write what you think about the work, its meaning or the main characters. Specify what exactly you liked and what you didn't like, and why you think so.








