About the Author

Badrinarayanan Lakshmiraghavan has more than fourteen years of information technology experience in all phases of the software development life cycle, including technology consulting and advisory roles in multiple technologies. He has been programming on the Microsoft technology stack from the days of Visual Basic 3.0.
Badri currently is a senior technology architect with Global Technology Consulting - Microsoft Center of Excellence of Cognizant (NASDAQ: CTSH), a Fortune 500 company. He speaks three languages: Tamil, English, and C#.
Badris coordinates are 12.9758 N, 80.2205 E on the third rock from the yellow-dwarf star that lies close to the inner rim of the Orion arm of the Milky Way Galaxy.
About the Technical Reviewer
Fabio Claudio Ferracchiati, a prolific writer on cutting-edge technologies, has contributed to more than a dozen books on .NET, C#, Visual Basic, and ASP.NET. He is a .NET Microsoft Certified Solution Developer and lives in Milan, Italy. You can read his blog at Ferracchiati.com .
Acknowledgments
Whether you seek general information on .NET security or specific information on claims-based identity and ASP.NET Web API, you likely will find the answers you need on his blog at http://leastprivilege.com or in one of his posts in a technical forum such as MSDN. No points for guessing who it is: Dominick Baier, the ultimate voice of wisdom when it comes to ASP.NET Web API security! I deeply appreciate Dominick for all his help and guidance, including taking time from his busy schedule to write the foreword for this book.
Just about every book author acknowledges the team assembled by the publisher, and I wont be any different. Clich or not, I must gratefully thank the following individuals who are part of the Apress team (in the same order as they got involved).
- Ewan Buckingham, lead editor, for his patience answering all my relevant and irrelevant questions and helping me all the way from the proposal stage to manuscript completion.
- Mark Powers, coordinating editor, for his helping nature and promptness (I have yet to see an instance where Mark has not replied to my mail two hours from the time I clicked the Send button despite being on the other side of the globe).
- Fabio Claudio Ferracchiati, technical reviewer, for catching the subtle things that I overlooked.
- Teresa Horton, copy editor, for putting up with my writing, notably my problem with the usage of articles.
- The SPi Global production team for diligently incorporating all the changes I asked for.
- Barbara McGuire, developmental editor, for her patience in reading through my jumbles, giving structure and order to the content. Thanks very much, Barbara; you might be last on this list, but definitely not the least!
My thanks also to Arvind TN of Cognizant GTC Microsoft CoE for asking THE question that resulted in this book.
Finally, a huge thank you to my familymy wife Poornima and my sons Anirudh and Aparajithfor their understanding and enormous patience. My special thanks to Anirudh for understanding, without any complaints, that his dad has to sit in front of the computer typing away, unable to watch with him such exciting things as an asteroid hitting the earth and obliterating Triceratops, T-Rex, Stegosaurus, and Alamosaurus.
APPENDIX A

ASP.NET Web API Security Distilled
This appendix is a grand summary of this book, a recap of the various security mechanisms we have seen so far. There is no good or bad mechanism in an absolute sense. The idea of this book is to present all the mechanisms and let you decide based on your needs.
There is no mandate that you must select only one mechanism. You can design your web API to support more than one and give client applications a few options. The ASP.NET Web API pipeline helps us plug in as many handlers as we need to run. Message handlers are great enablers for achieving that goal.
If you decide to choose more than one, carefully consider the possibilities. For example, if you mix basic and digest authentication and decide to use HTTPS only for basic authentication, there is a risk of a malicious man-in-the middle (MITM) removing the WWW-Authenticate: Digest response header and tricking the client into sending the credentials in a basic scheme in clear text.
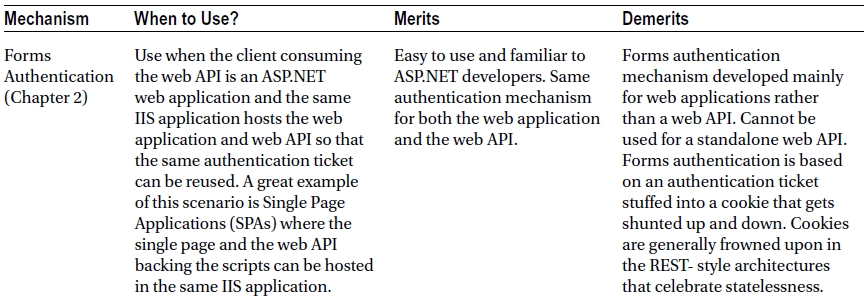



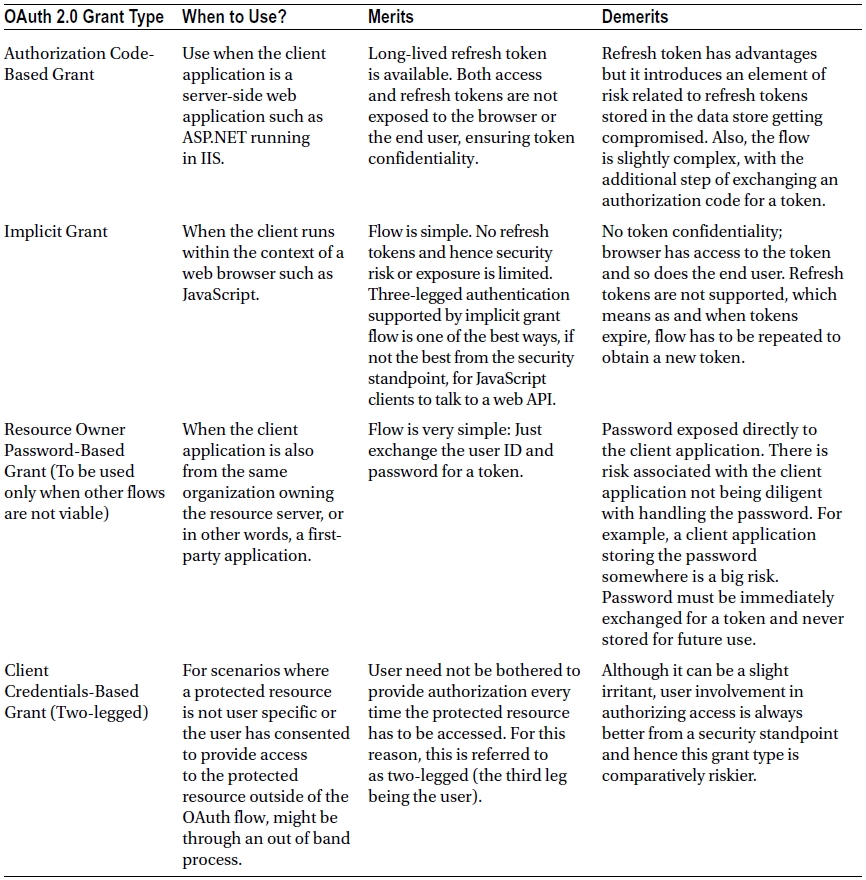
The right approach in securing ASP.NET Web API is choosing the appropriate mechanism for your organizational and application needs, rather than being influenced by others. For example, do not use OAuth 2.0 just because others use it.
A great thing about ASP.NET Web API and the .NET Framework in general, with claims-based identity, is that you can plug in new authentication and authorization methods and yet keep the application resistant to the effects on account of these changes. New message handlers can be plugged in to handle new authentication methods and ultimately, if the web API works based on claims, it just boils down to handlers creating appropriate claims for the identity.
CHAPTER 1

Welcome to ASP.NET Web API
Begin at the beginning, the King said gravely, and go on till you come to the end: then stop.
Lewis Carroll, Alice in Wonderland
If you have chosen to read this book, which is on ASP.NET Web API security, it is highly likely that you are familiar with ASP.NET Web API. In case you are not or simply would like me to begin at the beginning, this introductory chapter along with the next chapter will help you gain a quick understanding of the basics of ASP.NET Web API and help you appreciate the need for the emphasis on security for ASP.NET Web API applications.
ASP.NET Web API Security: If we break this down, we get multiple termsWeb API, ASP.NET Web API, and Security. We start by understanding what a web API is in general before moving on to a primer on RESTful Web API, followed by a review of how the Microsoft ASP.NET Web API framework can help you build web APIs. We complete the chapter with a primer on security that looks at all aspects of security, above and beyond the login screen accepting a username and password, which for many is synonymous with the word security.
What Is a Web API, Anyway?
It all started with the launch of Sputnik in 1957, by the Union of Soviet Socialist Republics (USSR). The United States, under the leadership of then President Eisenhower, started the Advanced Research Projects Agency (ARPA) to advance the United States in the technology race, in the light of the Sputnik launch. One of the ARPA-funded projects was ARPANET, the worlds first operational packet switching network. ARPANET led to the development of protocols that allowed networks to be joined together into a network of networks that evolved into the ubiquitous


















