The Story of My Hackers and I
By Beatrice Lin Walsh
The purpose for this book is to bring awareness of Internet fraud. Everything written here is true. Should anything proved to be wrong, it should be judged because I had no knowledge of its true nature by fact for I would never have intended to place false accusation of anyone or any organization.
Best regards
Beatrice
Content
A Missing Cake Order
FIFA14 And Its In-app Purchase
found out my home hp pc had a keylogger
trying to understand my computer day and nightgoogle account activities and key loggers
Apple id and the lost controls on my iphones and ipad
Storms hit the roof when it is already leaking--even my mobile phones were compromised
Current status: tips to keep distance from keyloggers
one month later
the truth
seeking help all the way to the top
secrets of mobile phones
landline can be hacked, too
bubbles of the world
e-signatories
A Missing Cake Order
The whole hacking incident started on the eve of my birthday. That afternoon I ordered online a cake from Belgique for myself, a heart-shaped chocolate cake. 
I paid through a credit card and I received a confirmation on screen saying I had completed the payment. But I never received a confirmation letter in my mailbox. I was puzzled. I thought I should wait till the next morning. After that, soon my life was turned upside down. I couldnt care less I heard nothing about the cake again until June 17th when I recovered the very email address that I used to log in for the cake shop.
On June 17, 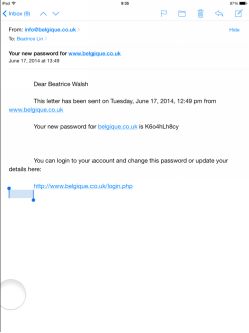 I saw the message fromBelgique,
I saw the message fromBelgique,
It made me laugh. For crying out loud, my hackers wouldnt let go of anything even a birthday cake.
I dialed the number to speak to Belgique. It was my secret hope there might be a chance to eat a cake after all. The gentleman working atBelgique was very kind. He couldn't find any orders at first. All data had been erased from my account--no contact number, no delivery address, only the names. He kindly went through credit card bills. And he discovered two orders on that day. The first one was 28.50 which matched with the price of my heart-shaped cake; the second one was 19.50. Unfortunately, or maybe fortunately, neither order went through.
This was only the tip of the iceberg to start unveil how hackers impersonated me. First, theyobtained my email address, then keylogged into my home computer PC ,and finally control my mobile telephonesim number.
FIFA14 And Its In-app Purchase 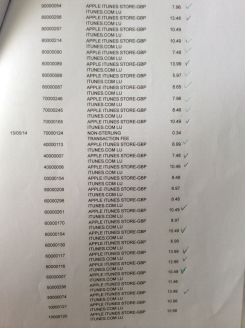
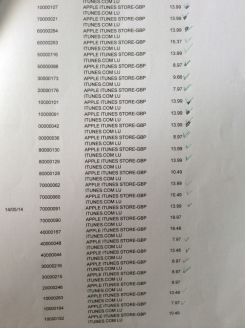
It was my birthday next day. That evening I remembered the cake so I thought I might take a look at my bank account. Words could not express my shock when I saw the statements.
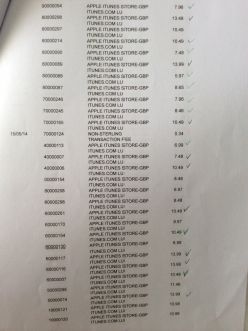
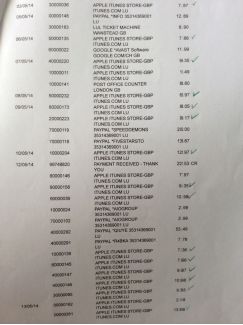
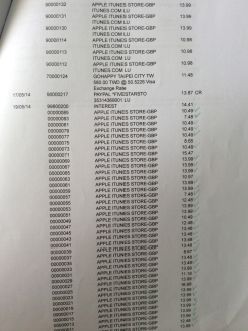
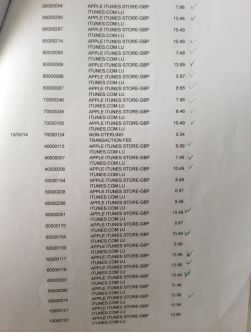
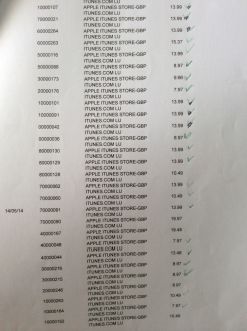
These are not the end of the bills for that month. There were a lot more already been authorized but had not hit the invoices.
I panicked and I phoned the bank. First Direct was absolutely brilliant. The lady from the credit card department reassured me the bank would reimburse the fraud charges first and then talk to Apple's Fraud Dept. I was quite happy when Iheard it. As usual, anything I thought was educational Iwould try to share the knowledge with my children. Id like them to know how to spot suspicious unauthorized charges.
I called my 11-year-old son and eight-year-old daughter to show them the bill saying how people can steal other's identity and fraud. But to my greatest horror and distress, I heard my son stammering, " Mom, I played the games. It's me who did it. What is going to happen to me? "
My brain shattered in that instance. I couldn't utter a word.
I fell into such a state that I couldn't think anymore.
My son ran to his father. His father came to me and said, " You need to speak to the bank to call it off. You have to withdraw. We'll pay for whatever the cost is but to preserve our sons record. "
I understood the seriousness and the possible impact to my child, so I phoned the bank immediately. I located the lady I spoke to before and apologized to her.
It was the worst night in my life.
I questioned myself, " Why am I so hurt because it was my son? Why wouldn't I feel so distressed if it were my husband or my sister? "
Because I valued the parental bond. Only my son and my daughter are part of me. I grasped upon the relationship almost no different from the attachment to myself ego.
That night I didn't sleep. I sat in front of the computer trying to source out all the invoices. Only till now I can see all the problems clearly: My son thought he played all the games and it was him who spent all the money. The fact was It wasn't done all by himself. All my Apple accounts have been compromised. My son accidentally fell into the trap of FIFA14's in-app purchases when he was constantly cohorted by a gang of online players who happened to be our key-loggers. They were monitoring his mobile phone and his iPad like shadow puppet players. In the rest of the book, I will show evidence and proof to you how hackers can see and hear whatever you say over the phone and what you save in the computer.
found out my home hp pc had a keylogger
My PC had always been changing. There were always new icons of applications popping up on the screen. I used to think they were new softwares installed by my husband. But after my birthday I started to think differently. I became suspicious of every change. I stared at my computer day and night. I believed I was sharing my computer with a group of whose existence I had no knowledge of.
My first clue came from Google report. When I opened an Google email account, I noticed I had a choice to sign up to receive my account activity report at that time. And the following 2 pictures were what I got. My address was not in Bognor Regis.
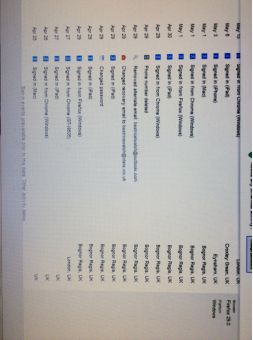
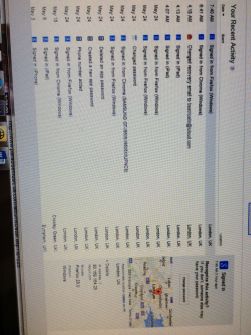 My hackers ar e keyloggers who unlawfully secretly monitor and log all keystrokes of my properties.
My hackers ar e keyloggers who unlawfully secretly monitor and log all keystrokes of my properties.
According to geeks, keyloggers are mostly spread using the following methods:
When you open a file attached to an email;
When a file is launched from an open-access directory on a P2P network
Next page









 I saw the message fromBelgique,
I saw the message fromBelgique,







 My hackers ar e keyloggers who unlawfully secretly monitor and log all keystrokes of my properties.
My hackers ar e keyloggers who unlawfully secretly monitor and log all keystrokes of my properties.