Yoram Orzach - Network Protocols for Security Professionals: Probe and identify network-based vulnerabilities and safeguard against network protocol breaches
Here you can read online Yoram Orzach - Network Protocols for Security Professionals: Probe and identify network-based vulnerabilities and safeguard against network protocol breaches full text of the book (entire story) in english for free. Download pdf and epub, get meaning, cover and reviews about this ebook. year: 2022, publisher: Packt Publishing - ebooks Account, genre: Home and family. Description of the work, (preface) as well as reviews are available. Best literature library LitArk.com created for fans of good reading and offers a wide selection of genres:
Romance novel
Science fiction
Adventure
Detective
Science
History
Home and family
Prose
Art
Politics
Computer
Non-fiction
Religion
Business
Children
Humor
Choose a favorite category and find really read worthwhile books. Enjoy immersion in the world of imagination, feel the emotions of the characters or learn something new for yourself, make an fascinating discovery.
- Book:Network Protocols for Security Professionals: Probe and identify network-based vulnerabilities and safeguard against network protocol breaches
- Author:
- Publisher:Packt Publishing - ebooks Account
- Genre:
- Year:2022
- Rating:5 / 5
- Favourites:Add to favourites
- Your mark:
Network Protocols for Security Professionals: Probe and identify network-based vulnerabilities and safeguard against network protocol breaches: summary, description and annotation
We offer to read an annotation, description, summary or preface (depends on what the author of the book "Network Protocols for Security Professionals: Probe and identify network-based vulnerabilities and safeguard against network protocol breaches" wrote himself). If you haven't found the necessary information about the book — write in the comments, we will try to find it.
Discover network-based attacks and learn to defend your organizations network and network devices
Key Features- Exploit vulnerabilities and use custom modules and scripts to crack authentication protocols
- Safeguard against web, mail, database, DNS, voice, video, and collaboration server attacks
- Monitor and protect against brute-force attacks by implementing defense mechanisms
Network security plays an important role in securing IT infrastructures against attacks. The increased demand for computer systems, and the ever-evolving internet, has allowed people to find vulnerabilities and infiltrate into organizations through their network. Network Protocol Security will help you safeguard your organizations network and networking devices.
This book is a comprehensive guide that begins with the basics, gradually increases in complexity, and later takes you through advanced concepts. You will start by understanding the structure of data network protocols and devices as well as breaches. In addition to this, youll become familiar with attacking tools and scripts that take advantage of these breaches. After covering the basics, you will learn attacks that target networks and network devices. Next, you will perform eavesdropping, learn data analysis, and use behavior analysis for network forensics. Toward the concluding chapters, you will understand network protocols and how to use methods and tools you learned in the previous parts to attack and protect these protocols.
By the end of this network security book, you will have learned network protocol security and security counter-measures to protect network protocols.
What you will learn- Understand security breaches, weaknesses, and protection techniques
- Attack and defend wired as well as wireless networks
- Discover how to attack and defend LAN, IP, and TCP/UDP-based vulnerabilities
- Focus on encryption, authorization, and authentication principles
- Gain insights into implementing security protocols the right way
- Use tools and scripts to perform attacks on network devices
- Wield Python, PyShark, and other scripting tools for packet analysis
- Identify attacks on web servers to secure web and email services
This book is for red team and blue team pentesters, security professionals, or bug hunters. Anyone involved in network protocol management and security will also benefit from this book. Basic experience in network security will be an added advantage.
Table of Contents- Data Networks Structure and Weakness Points
- Network Protocols Structure and Operation
- Security Protocols and Their Implementation
- Using Network Security Tools, Scripts and Codes
- Finding Protocol Vulnerabilities
- Discovering Network-Based Attacks and Tools
- Attacking on Network Devices
- Network Traffic Analysis and Eavesdropping
- Using Behavior Analysis and Anomaly Detection
- Discovering LANs, IP, and TCP/UDP-Based Attacks
- Implementing Wireless Networks Security
- Attacking Routing Protocols
- DNS Security
- Securing Web and Email Services
- Enterprise Applications Security - Databases and Filesystems
- IP Telephony and Collaboration Services Security
Yoram Orzach: author's other books
Who wrote Network Protocols for Security Professionals: Probe and identify network-based vulnerabilities and safeguard against network protocol breaches? Find out the surname, the name of the author of the book and a list of all author's works by series.









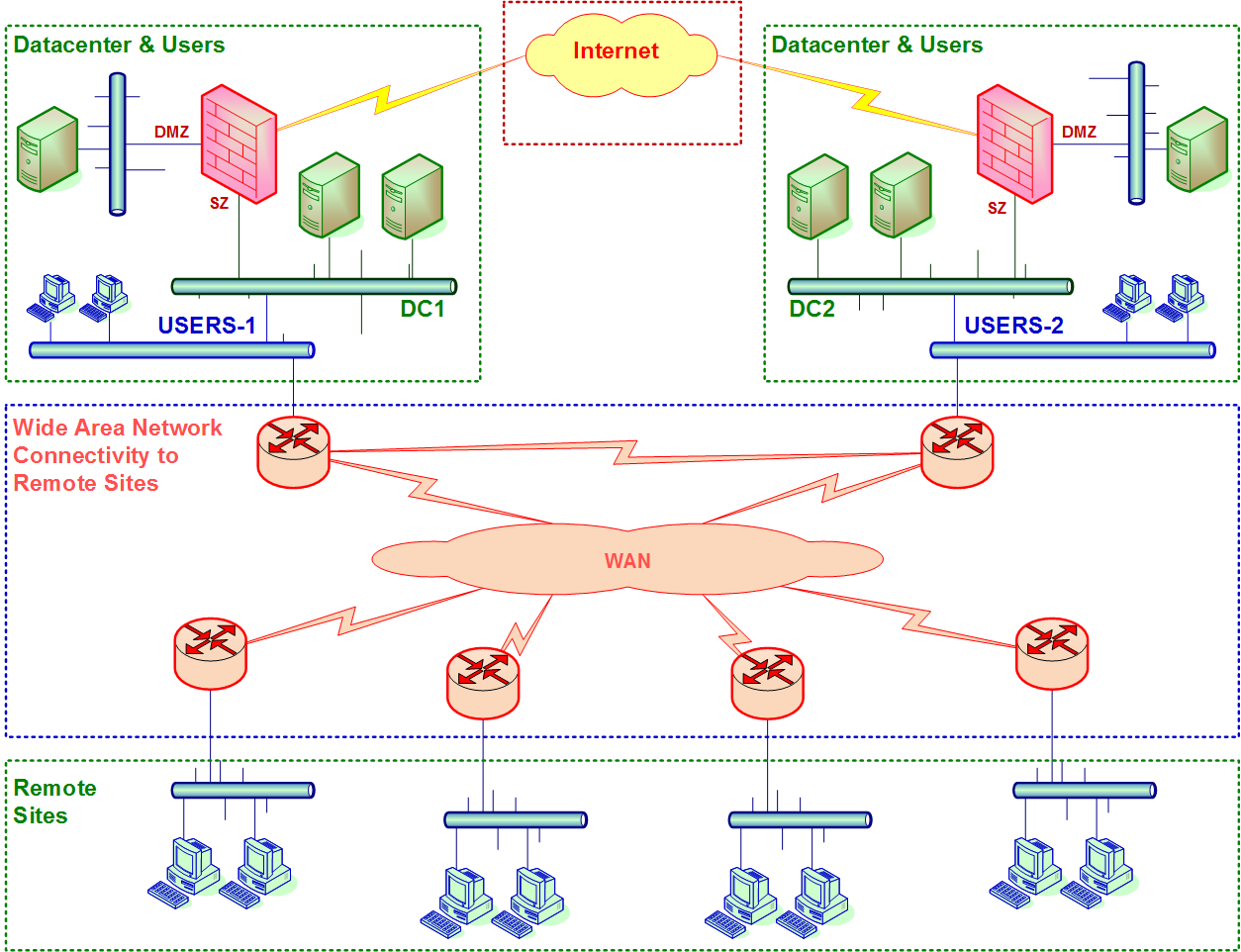 Figure 1.1 Typical enterprise network
Figure 1.1 Typical enterprise network