Vijay Bollapragada - IPSec VPN Design
Here you can read online Vijay Bollapragada - IPSec VPN Design full text of the book (entire story) in english for free. Download pdf and epub, get meaning, cover and reviews about this ebook. year: 2005, publisher: Cisco Press, genre: Home and family. Description of the work, (preface) as well as reviews are available. Best literature library LitArk.com created for fans of good reading and offers a wide selection of genres:
Romance novel
Science fiction
Adventure
Detective
Science
History
Home and family
Prose
Art
Politics
Computer
Non-fiction
Religion
Business
Children
Humor
Choose a favorite category and find really read worthwhile books. Enjoy immersion in the world of imagination, feel the emotions of the characters or learn something new for yourself, make an fascinating discovery.
- Book:IPSec VPN Design
- Author:
- Publisher:Cisco Press
- Genre:
- Year:2005
- Rating:3 / 5
- Favourites:Add to favourites
- Your mark:
IPSec VPN Design: summary, description and annotation
We offer to read an annotation, description, summary or preface (depends on what the author of the book "IPSec VPN Design" wrote himself). If you haven't found the necessary information about the book — write in the comments, we will try to find it.
The definitive design and deployment guide for secure virtual private networks
- Learn about IPSec protocols and Cisco IOS IPSec packet processing
- Understand the differences between IPSec tunnel mode and transport mode
- Evaluate the IPSec features that improve VPN scalability and fault tolerance, such as dead peer detection and control plane keepalives
- Overcome the challenges of working with NAT and PMTUD
- Explore IPSec remote-access features, including extended authentication, mode-configuration, and digital certificates
- Examine the pros and cons of various IPSec connection models such as native IPSec, GRE, and remote access
- Apply fault tolerance methods to IPSec VPN designs
- Employ mechanisms to alleviate the configuration complexity of a large- scale IPSec VPN, including Tunnel End-Point Discovery (TED) and Dynamic Multipoint VPNs (DMVPN)
- Add services to IPSec VPNs, including voice and multicast
- Understand how network-based VPNs operate and how to integrate IPSec VPNs with MPLS VPNs
Among the many functions that networking technologies permit is the ability for organizations to easily and securely communicate with branch offices, mobile users, telecommuters, and business partners. Such connectivity is now vital to maintaining a competitive level of business productivity. Although several technologies exist that can enable interconnectivity among business sites, Internet-based virtual private networks (VPNs) have evolved as the most effective means to link corporate network resources to remote employees, offices, and mobile workers. VPNs provide productivity enhancements, efficient and convenient remote access to network resources, site-to-site connectivity, a high level of security, and tremendous cost savings.
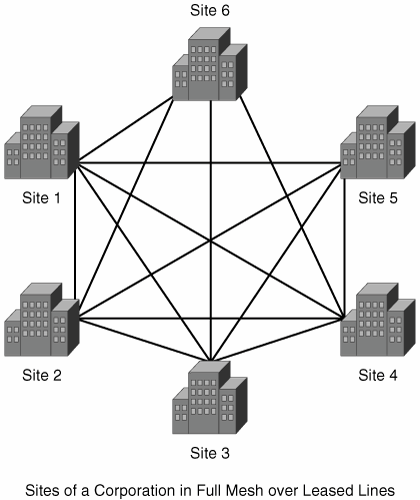
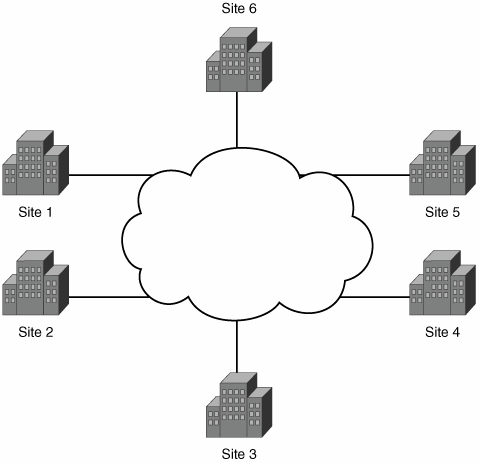
IPSec VPN Design is the first book to present a detailed examination of the design aspects of IPSec protocols that enable secure VPN communication. Divided into three parts, the book provides a solid understanding of design and architectural issues of large-scale, secure VPN solutions. Part I includes a comprehensive introduction to the general architecture of IPSec, including its protocols and Cisco IOS IPSec implementation details. Part II examines IPSec VPN design principles covering hub-and-spoke, full-mesh, and fault-tolerant designs. This part of the book also covers dynamic configuration models used to simplify IPSec VPN designs. Part III addresses design issues in adding services to an IPSec VPN such as voice and multicast. This part of the book also shows you how to effectively integrate IPSec VPNs with MPLS VPNs.
IPSec VPN Design provides you with the field-tested design and configuration advice to help you deploy an effective and secure VPN solution in any environment.
This security book is part of the Cisco Press Networking Technology Series. Security titles from Cisco Press help networking professionals secure critical data and resources, prevent and mitigate network attacks, and build end-to-end self-defending networks.
Vijay Bollapragada: author's other books
Who wrote IPSec VPN Design? Find out the surname, the name of the author of the book and a list of all author's works by series.