1. Introduction
As computational technology advances, more and more systems in daily life are controlled or supported by algorithms and computers. The most representative evolution includes the fly-by-wire and the drive-by-wire of aircraft and automotive systems which are no longer pure mechanical systems. This kind of systems combining computations and physical behaviors are called cyber-physical systems, where cyber represents the computational part, and physical represents the physical behavior. Besides aircraft and automotive systems, other common cyber-physical systems include medical devices, smart grids, and robotics. Many of them are safety-critical systems, and a fault may cause serious consequences or even endanger users in extreme circumstances.
Besides regular system faults, cyber-security attacks are even more critical as they can also trigger different kinds of systems faults, and attackers are malicious to find out security holes of systems. They may access secret information, control system behavior, or paralyze systems. Different types of cyber-attacks have been identified in automotive systems [6, 13, 2527, 39], aircraft systems [5, 46], global positioning systems [8, 58], medical devices [10, 29], and smart grids [24, 30]. These attacks become even more threatening as systems are becoming more connected with the surrounding environment, infrastructures, and other systems as these connections provide breeding grounds and access points for cyber-attacks.
Security mechanisms can be designed to protect against cyber-attacks and meet security requirements, such as integrity, authenticity, confidentiality, or availability. However, there are many challenges of applying security mechanisms to cyber-physical systems, such as open environments (e.g., wireless communication), limited resources (e.g., network bandwidth, computational resource, and power), strict timing requirements, and large number of devices [10, 23, 24, 27, 46].
Fig. 1.1
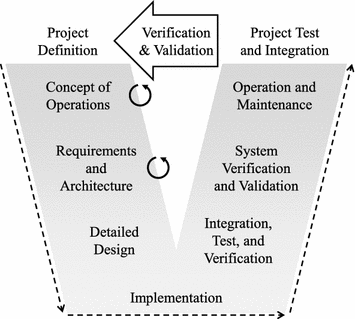
The system development process [35]
These challenges above make it very difficult and sometimes impossible to add security mechanisms after initial design stages without violating other system constraints. The system development process is usually described as the V-model shown in Fig. [35]. If security is not considered before detailed design or implementation, the challenges above are very difficult to be resolved. For example, remaining network bandwidth or computational resource is not enough for security mechanisms, or timing requirements are too tight to add security mechanisms. It is therefore important to develop a systematic approach to address security at early design stages together with all other design constraints.
In this book, a general security-aware design methodology is first introduced to address security together with other design constraints at the design stages for cyber-physical systems. The methodology is based on Platform-Based Design [47], where a functional model and an architectural platform are initially captured separately and then brought together through a mapping process. During mapping, the functional model is implemented on the architectural platform, and constraints and objectives are satisfied and optimized, respectively. The methodology is different from the traditional mapping process because it not only maps functional models to architectural platforms but also explores security mechanism selection and architecture selection.
Then, the book focuses on the security issues for automotive systems as they represent many of the common challenges in cyber-physical systems, such as resource constraints and timing requirements. The Controller Area Network (CAN) protocol, which is a very representative asynchronous protocol and currently the most used in-vehicle communication protocol, is first studied, and a security mechanism is proposed for the CAN protocol. Based on the security mechanisms, security is addressed during the mapping from functional models to architectural platforms, and security and safety constraints are considered in an integrated formulation. With a flexible key distribution scheme, the security-aware mapping problem is formulated as a Mixed Integer Linear Programming (MILP) problem.
Besides the CAN protocol, a Time Division Multiple Access (TDMA) based protocol for in-vehicle communication is also considered, which is a very representative synchronous protocol and an abstraction of many existing protocols such as the FlexRay [7], the Time-Triggered Protocol [45], and the Time-Triggered Ethernet [44]. This kind of protocols is increasingly adopted in various safety-critical systems for more predictable timing behavior. The time-delayed release of keys [2, 37, 38, 55] is applied as the security mechanism, and an algorithm that combines a simulated annealing approach with a set of efficient optimization heuristics is developed to solve the security-aware mapping problem.
The methodology is then applied to Vehicle-to-Vehicle (V2V) communications with the Dedicated Short-Range Communication (DSRC) technology. A security-aware optimization problem with consideration of both security and safety requirements is formulated, and it considers the overhead of different settings of the Elliptic Curve Digital Signature Algorithm (ECDSA). The key decision variables are the sending rates and the authentication rates of Basic Safety Messages (BSMs) which carry important information for safety applications and thus need security protections, and their sending rates and authentication rates play dominant roles in system performance and security, respectively [1, 23, 28]. The security-aware optimization problem is solved by an efficient algorithm.
Following the studies of asynchronous and synchronous protocols, other general security-aware design problems are also presented in this book. The first type is based on Finite State Machines (FSMs), and a synthesis problem is formulated to model a system with limited resources. The second type is based on graphs where message duplication and network partitioning are addressed for security.
The rest of the book is organized as follows. Chapter concludes the book and points out some future directions.
2. Security Threats in Cyber-Physical Systems