Chapter 1
The Community Cybersecurity Maturity Model (CCSMM)
ABSTRACT
Lessons learned from the community cyber security exercises showed common threads each community needed to focus on in order to improve the communitys cyber security posture. These similarities were grouped into four areas of improvement called dimensions. The dimensions are awareness, information sharing, policies, and planning. The methods in which communities can implement improvement are called implementation mechanisms. These mechanisms are common approaches used every day such as establishing metrics, implementing technologies, creating processes and procedures, and conducting training and assessments.
INTRODUCTION
Threats to communities have been traditionally thought of in terms of natural disasters. There have been a number of U.S. cities that have been severely damaged or completely destroyed by natural disaster. Galveston, Texas was hit by a category 4 hurricane in 1900, destroying nearly 4000 homes, all bridges to the mainland, telegraph lines, most ships in the wharf and even rail lines as far as 6 miles inland (Crezo, 2012). In 1906, San Francisco, California experienced an earthquake followed by fires. The initial tremors destroyed the citys water mains, leaving firefighters with no means of combating the growing blaze, which burned for several days and consumed much of the city (History.com, 2018). The St. Louis Tornado Disaster in 1927, killed 79 people and caused $1.8 billion dollars in damage (adjusted) (Crezo, 2012). More recent disasters that should be noted here are Hurricane Katrina in 2005 that flooded 80% of New Orleans after the levees failed, and Superstorm Sandy affecting New Jersey and New York in 2012. Sandy knocked out subway service in New York City and destroyed multi-million-dollar homes at the Jersey Shore. (Harrington, 2018).
These early natural disasters led to the creation of the Federal Emergency Management Agency (FEMA) in 1979. The Federal Emergency Management Agency coordinates the federal government's role in preparing for, preventing, mitigating the effects of, responding to, and recovering from all domestic disasters, whether natural or man-made, including acts of terror (Fema.gov).
Since FEMAs inception, it has assumed a variety of roles, but it continues to maintain its original mission and over the years has produced many guides to assist communities to prepare for disasters. In 2012, FEMA published a guide called Threat and Hazard Identification and Risk Assessment Guide: Comprehensive Preparedness Guide (CPG) 201, First Edition. In this guide a table of threats and hazards was provided for jurisdictions to identify the risks most likely to impact their community. Identifying the threats will assist the community to focus preparedness efforts and resources. The risks are categorized into three specific areas:
- Natural resulting from acts of nature
- Technological involves accidents or the failures of systems and structures
- Human-caused caused by the intentional actions of an adversary
| Figure 1. |
|---|
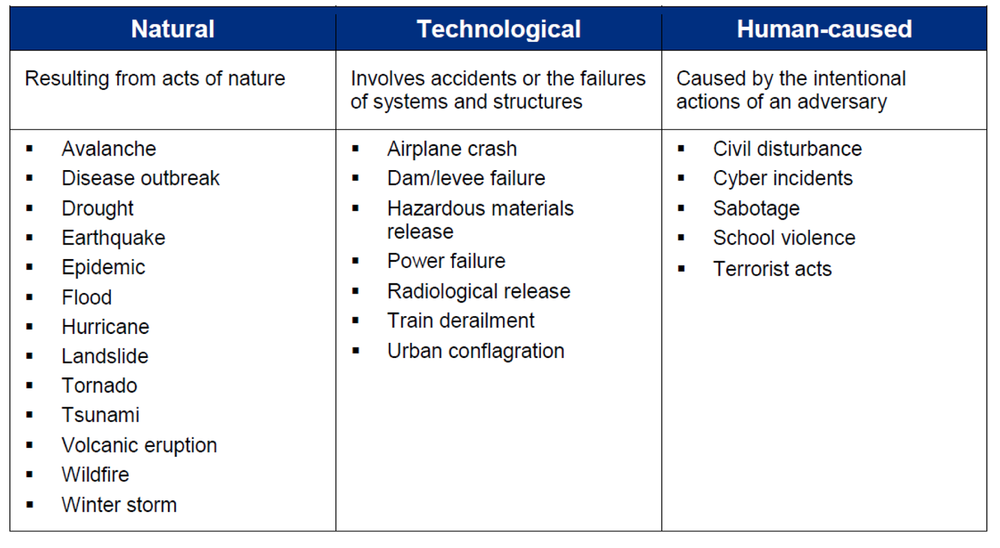 |
Notice in Figure 1, the list of threats has expanded beyond natural disasters. This table represents the recognition that communities potentially face many threats that once were not considered. Cyber incidents are also listed in this table under the human-caused threats. This is significant because it shows the federal government has recognized cyber incidents as a threat a community should prepare for and build capabilities to prevent, protect, mitigate, respond to and recover from.
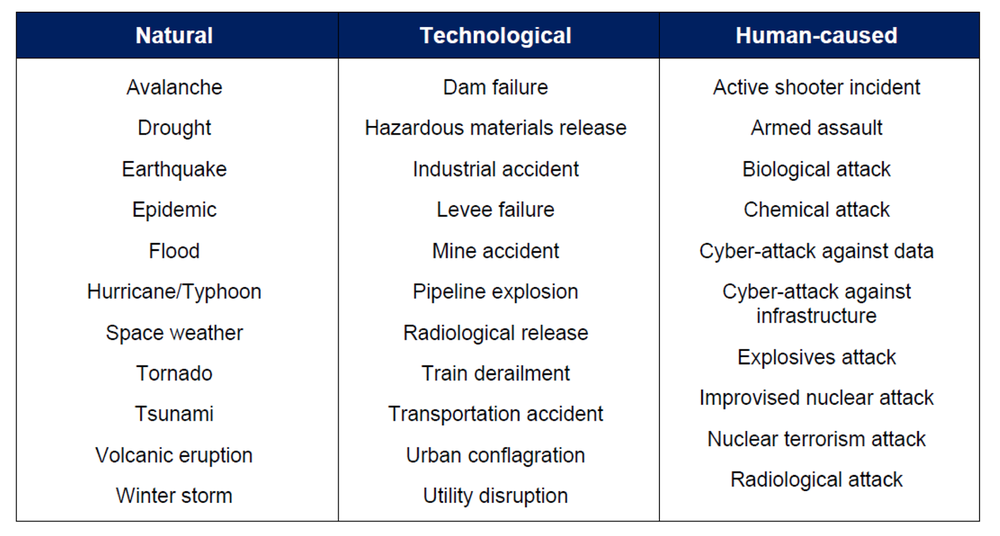
In May of 2018, the 3rd Edition of the Comprehensive Preparedness Guide (CPG) 201 was published, and the list of example threats expanded and changed the cyber references to cyber-attack against data and cyber-attack against infrastructure as seen in Table 2. These examples suggest the recognition of the cyber threat to a community can potentially impact systems that store data and any systems that are used to support the infrastructure.
| Figure 2. |
|---|
 |
Once a community has identified the threats and hazards it faces, preparedness efforts can be planned, processes and procedures can be developed and implemented, and capabilities the community plans to achieve to manage the threats can be put in place. Exercises are then used to test the plans to see how well they work and are also used to assess existing capabilities needed to respond to an incident. There are different types of exercises that can be used to assess the community plans, processes, and capabilities. They are:
- Walkthroughs, Workshops, or Orientation Seminars: Used to provide information regarding the response, continuity, communications plans and roles and responsibilities.
- Tabletop Exercises : Facilitated discussion used to describe roles and response capabilities through scenarios provided.
- Functional Exercises : Used to simulate an emergency situation allowing personnel to perform their duties. This type of exercise tests capabilities of the team, processes and shows the availability of resources needed.
- Full-scale Exercises : Takes place on location using personnel and equipment that would be needed to respond to an incident, and local businesses often participate. This type of exercise is the most realistic (Exercises, n.d.).
Exercises help the community to recognize weaknesses they may have in terms of capability to address an incident, resources that may be needed and availability of that resource and the procedures that may be missing or should be changed before an incident occurs.
This chapter describes the creation of the Community Cyber Security Maturity Model (CCSMM). The model was designed and created as a result of the lessons learned from many community and state cybersecurity tabletop exercises that were conducted from 2002 through 2008. Tabletop exercises were used because this method provides a platform to achieve maximum participation and low-cost execution. The use of tabletop exercises allows the participants to gain an awareness of the cyber threat, its potential impacts on the community, and allows the participants to recognize the gaps the community may have in their preparedness. The intent of the CCSMM is to provide a framework that can be used to develop a cybersecurity program for a community.
BACKGROUND
The Center for Infrastructure Assurance and Security (CIAS), a cybersecurity research center, at the University of Texas at San Antonio (UTSA) was established in 2001. During this time, there was very little, if any, cybersecurity research nor outreach initiatives being conducted at the university. The CIAS was the first center established to address cybersecurity initiatives. Through the CIAS, cybersecurity research was encouraged in the College of Computer Science, College of Business, and the College of Engineering. The first cybersecurity community outreach initiative accomplished by the CIAS was a tabletop exercise known as Darkscreen.
The Darkscreen tabletop exercise was the initial community cybersecurity exercise led by the CIAS. The exercise was the first of its kind, that we know of, and was conducted in San Antonio, Texas in fall of 2002. The exercise scenario focused on fairly simple cybersecurity events. There were no physical attack events as part of this exercise. This is a significant point. The CIAS researchers believed that developing a cybersecurity exercise that excluded physical events would force the participants to focus on how they would handle a cybersecurity event. The idea was that if physical was integrated into an exercise before participants were comfortable with cybersecurity events, they would focus all their attention on the event that was understood, and they knew how to respond to. By developing an exercise that only contained cyber events, the participants would be able to focus their efforts on each cyber incident and have facilitated discussions about what each incident could potentially do to the organization, what response might be appropriate, and when to share information about a cyber incident.













