Alan Radley - The Science Of Cybersecurity
Here you can read online Alan Radley - The Science Of Cybersecurity full text of the book (entire story) in english for free. Download pdf and epub, get meaning, cover and reviews about this ebook. year: 2017, genre: Romance novel. Description of the work, (preface) as well as reviews are available. Best literature library LitArk.com created for fans of good reading and offers a wide selection of genres:
Romance novel
Science fiction
Adventure
Detective
Science
History
Home and family
Prose
Art
Politics
Computer
Non-fiction
Religion
Business
Children
Humor
Choose a favorite category and find really read worthwhile books. Enjoy immersion in the world of imagination, feel the emotions of the characters or learn something new for yourself, make an fascinating discovery.
- Book:The Science Of Cybersecurity
- Author:
- Genre:
- Year:2017
- Rating:4 / 5
- Favourites:Add to favourites
- Your mark:
- 80
- 1
- 2
- 3
- 4
- 5
The Science Of Cybersecurity: summary, description and annotation
We offer to read an annotation, description, summary or preface (depends on what the author of the book "The Science Of Cybersecurity" wrote himself). If you haven't found the necessary information about the book — write in the comments, we will try to find it.
The Science Of Cybersecurity — read online for free the complete book (whole text) full work
Below is the text of the book, divided by pages. System saving the place of the last page read, allows you to conveniently read the book "The Science Of Cybersecurity" online for free, without having to search again every time where you left off. Put a bookmark, and you can go to the page where you finished reading at any time.
Font size:
Interval:
Bookmark:


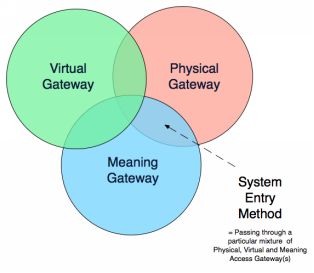







CHAPTER I
Introduction
THE SUBJECT at hand is the secure transfer of meaning between individual human beings using networked computers. Our goal is to characterise a point-to-point communication system for replicatin g information pattern s encapsulated as discrete units of dat a (e.g. messages/files/folders ) between remote computer nodes; whilst protecting the social integrity (privacy) of said patterns in place and time. A second goal of this book is to establish a safe procedure for point-to-point information transfer and by means of logically consistent definitions, axioms, analysis and exposition.
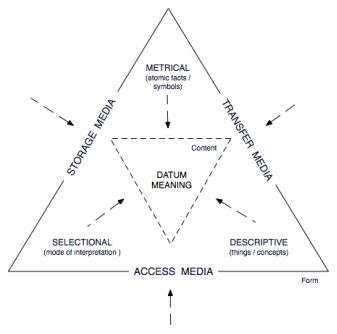
The British physicist Professor Donald MacKay (1922-1987) once said that the informational content of a message/representation consists of three components ; metrical , descriptiv e, an d selectiona l [1 ]. Accordingly, in terms of the point-to-point transfer of information units (datums) between two humans or the one-to-one replication of meaning from a sender to receiver we can differentiate between the information pattern that is sent (i.e the atomic, symbolic and/o r metrica l data being replicated the digital 0s and 1s etc), and th e descriptiv e an d selectiona l capacity of the receiving system/human.
In other words, the receiver engages in a process of interpretation by utilising his or her beholders shar e [2].
Hence the meaning of a message is crucially dependent on the specific way(s) in which the receiver decodes and interprets the message. Ergo meaningful, effective and efficient communication between two parties depends upon a certain degree of synchronisation and agreement in terms of factors such a s language, experience, truth, history , plu s mod e an d contex t of the communication process itself.
Whereby it is important to realise that the entire subject matter of (communications ) cybersecurit y depends upon and is (entirely) developed from the axiomatic statements and principles presented in the previous three paragraphs.
In sum, this book is a characterisation of said axioms.
We begin with a simple question what is securit y in-and-of-itself and especially in terms of digital information sharing? In order to be able to formulate an answer we must narrow our field of study and concern ourselves solely with person-to-person (point-to-point) information transfer. We can differentiate this topic from all other information transfer types which involve either a source-point and/or end-point that is not a human being.
Ignored methods includ e machine-to-machin e, machine-to-perso n , an d person-to-machin e techniques.
In other words; we are not concerned with those cases where a compute r initiate s transfer(s) of information between machines, or does so automatically from machine to human or vice-versa.
Communication Of Meaning
A datu m of any idea or thing is a pattern of meanin g , an abbreviated description, definition or set of facts concerning the thing in question; typically prescribing an event, object, feeling, etc.; in token of, as a sign, symbol, or evidence of somethin g [Axiom 1 ] .
Datums are typically expressed within the boundaries of a specific language, medium, media and/or code; and normally each datum has an inherent lifetime whereby it may be created, stored, communicated, replicated, lost and /or destroyed etc. Each datum has a human and/or machin e creator/autho r , plus normally huma n owner(s ) plu s user(s ) (ref. social accessibility (or privacy) status ) [Axiom 2 ] .
Datums come in three kinds [ Axiom 3] :
A private datum is accessible only by a restricted group of peopl e or a particular set of human beings; and is inaccessible to all other persons [Axiom 3.1] .
A secret datum is accessible only by a single human beingtypically the owner and often the author; and is inaccessible to all other persons [ Axiom 3.2] .
An open datum is (potentially) accessible by anyone or by an unrestricted group of people [Axiom 3.3] .
A communication syste m is a system or facility for transferring datum(s)/patterns-of-meaning between persons and equipment. The system usually consists of a collection of individual communication networks, transmission systems, relay stations, tributary stations and terminal equipment capable of interconnection and interoperation so as to form an integrated whole [ Axiom ] .
Prior to the widespread adoption of the Internet information assurance concerned reliable data storage/processing. But today, whilst data backups and storage etc are vital, security is more often associated wit h data communications securit y herein our primary concern.
Accordingly, in the present book we shall explore just one of twelve possible security sub-system types (communication o f private-datum s ): wherein we analyse transfer of private datum-copies existing on a point-to-point communication syste m (whilst superficially considering aspects of data storage and presentation wherever necessary). Other sub-system security measures may be necessary in a real system and in order to protect standard compute r processin g, storag e an d presentatio n operations; and not only for private datums but fo r secre t an d open datum s as well ( see Appendix J ).
Throughout our exposition, we place emphasis on human-to-human communication(s) noting: A) that whilst we recognise that interpersonal communications by means of networked computers inevitably relies on a combination of severa l human-to-machin e an d machine-to-machin e communications etc; these aspects relate largely to low-level system-implementation detailsand in any case said aspects fall down-stream in logical and data-processing termsand therefore any top-level security principles will normally apply throughout all low-level subsystems; and: B) that any full consideration would include aspects of all twelve security sub-system types and would likely see the present book growing to over one thousand pages in length.
We ostensibly exclude from our discussion all systems of public information sharing (i.e . open-datum s ) and social networks whereby the information transfer i s one-to-man y, many-to-on e o r many-to-man y (i. e Facebook / Twitte r ).
Accordingly, SECURITYfor a person-to-person communication systemcan be defined as protection of secrecy , privacy or openness of meaning ; or the safe transfer of single / multiple datum(s) between humans [Axiom 5] .
Next pageFont size:
Interval:
Bookmark:
Similar books «The Science Of Cybersecurity»
Look at similar books to The Science Of Cybersecurity. We have selected literature similar in name and meaning in the hope of providing readers with more options to find new, interesting, not yet read works.
Discussion, reviews of the book The Science Of Cybersecurity and just readers' own opinions. Leave your comments, write what you think about the work, its meaning or the main characters. Specify what exactly you liked and what you didn't like, and why you think so.









