Tari Schreider - Building an Effective Cybersecurity Program
Here you can read online Tari Schreider - Building an Effective Cybersecurity Program full text of the book (entire story) in english for free. Download pdf and epub, get meaning, cover and reviews about this ebook. year: 2019, publisher: Rothstein Publishing, genre: Romance novel. Description of the work, (preface) as well as reviews are available. Best literature library LitArk.com created for fans of good reading and offers a wide selection of genres:
Romance novel
Science fiction
Adventure
Detective
Science
History
Home and family
Prose
Art
Politics
Computer
Non-fiction
Religion
Business
Children
Humor
Choose a favorite category and find really read worthwhile books. Enjoy immersion in the world of imagination, feel the emotions of the characters or learn something new for yourself, make an fascinating discovery.
- Book:Building an Effective Cybersecurity Program
- Author:
- Publisher:Rothstein Publishing
- Genre:
- Year:2019
- Rating:4 / 5
- Favourites:Add to favourites
- Your mark:
- 80
- 1
- 2
- 3
- 4
- 5
Building an Effective Cybersecurity Program: summary, description and annotation
We offer to read an annotation, description, summary or preface (depends on what the author of the book "Building an Effective Cybersecurity Program" wrote himself). If you haven't found the necessary information about the book — write in the comments, we will try to find it.
Building an Effective Cybersecurity Program — read online for free the complete book (whole text) full work
Below is the text of the book, divided by pages. System saving the place of the last page read, allows you to conveniently read the book "Building an Effective Cybersecurity Program" online for free, without having to search again every time where you left off. Put a bookmark, and you can go to the page where you finished reading at any time.
Font size:
Interval:
Bookmark:

Chapter 2
Now that you are designing your cybersecurity program like an architect, it is time for you to think about how you will administer your program or, in other word s, apply some governance. It makes no sense to create a great program and then let it go to seed. Governance ensures your program performs as intended. So, what is governance? If you ask ten people, you will get ten different answers. Dictionary definitions will only leave you puzzled. Simply put, governance is managing your program ethically and responsibly according to a set of principles and policies. Think in terms of doing the right things for the right reasons to allow the right things to happen.
Since the acronym GRC (governance, risk, and compliance) popped up in early 2000, a great deal of confusion on what constitutes governance ensued. GRC is only a vendor acronym serving as nothing more than a marketing umbrella for three separate functions or products. The use of the acronym allows anyone with a standard or solution aligning to any one of the letters of GRC to claim the governance moniker. In my experience, I have found that few true governance models, standards, or frameworks exist. In this chapter, I will focus on the G of GRC and decipher what governance is and is not as well as provide you with overviews of what I believe are credible frameworks or models to serve as your cybersecurity program governance foundation. I cover the R in Chapter 4 and the C in Chapter 5. My goal in this chapter is for you to learn what governance really is, what authoritative governance reference materials to rely on, and how to apply the right measure of oversight to your cybersecurity program.
This chapter will help you to:
- Understand what should be included in your governance foundation.
- Define an effective cybersecurity governance foundation.
- Familiarize yourself with the top governance frameworks and models.
- Recognize ways to automate your governance program.
The outcome of this chapter is that you will have established your foundation of governance for your cybersecurity program. Governance is essential to directing users, clients and service providers to behave in a manner that ensures the protection and privacy of information. Governance also ensure the cybersecurity program is professionally managed.
Figure 2.0 shows a reference architecture of how the cybersecurity program would look when you follow the direction provided within this chapter as well as the design checklist at the end of the chapter. The reference architecture is an abstraction view of your governance program. Your governance foundation, like all aspects of your program, will grow stronger as you add layers of maturity. All the components of the governance foundation exist within the governance playbook. In the reference architecture, components in gray are outcome-based or, in other words, they yield some form of program deliverable.
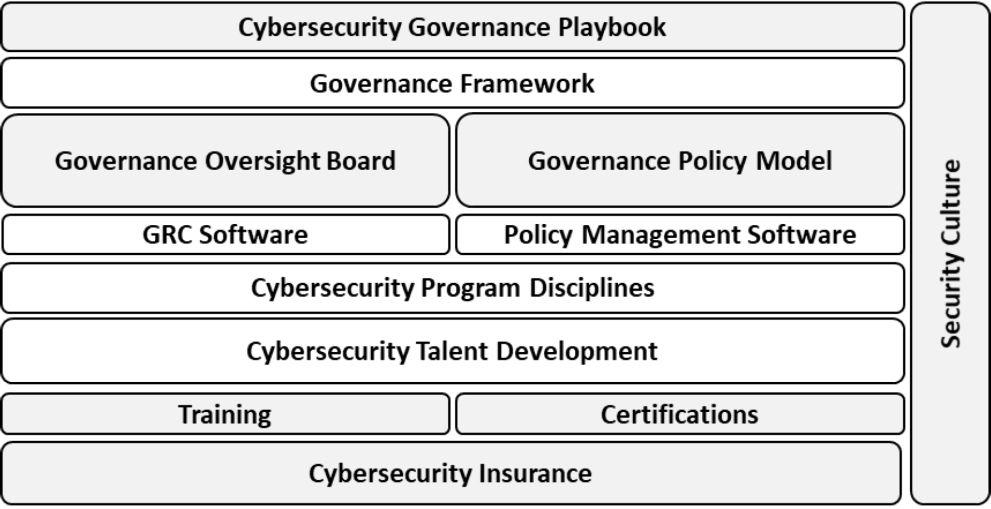
Figure 2.0. Governance Foundation Reference Architecture
Each component and subcomponent of the reference architecture is covered in more detail later in the chapter.
On this, the second stop of your journey you will need to establish a sound governance foundation, which ensures your cybersecurity program is managed responsibly and ethically. To help direct your energies toward the establishment of the governance foundation I have laid out the required outcome-based steps. The other content presented in the chapter is more reference, foundational or background oriented.
- Step 1: Create Governance Playbook - The playbook is where you will house all the components of the governance framework. Your organizations security principles, policies, training plans and insurance policies are stored here.
- Step 2: Appoint Governance Oversight Board - An oversight board, otherwise referred as a steering committee, has the critical job of ensuring your cybersecurity program is operated efficiently. The board validates business alignment, policy enforcement, budget allocation, and many more governance activities.
- Step 3: Create Governance Policy Manual - Identify the necessary policies aligned to their respective target audiences to provide clear direction on the responsibilities of protecting information and assets.
- Step 4: Develop Cybersecurity Talent - The growing shortage of IT talent in general, let alone cybersecurity talent, requires a concerted effort in talent retainment and motivation to reduce turnover. Talent development requires an investment in training and certifications to groom your cybersecurity staff to be the best they can be.
- Step 5: Acquire Cybersecurity Insurance - Understanding which policies provide which coverage is essential to applying a risk transfer or risk treatment. Cyberattack cost can be covered by general liability, data breach or cybersecurity insurance policies.
- Step 6: Establish a Culture of Security - If users, customers and partners dont care about protecting information and assets, even the best cybersecurity program will be hard-pressed to be effective. Investing in security training and user awareness pays off handsomely when people know the right thing to do to prevent a cyberattack or thwart an insider from causing harm to the organization.
When your back is up against the wall with limited resources, these are the mission critical governance activities you should address first:
- Create Your Cybersecurity Policy Manual - Follow the SANS Policy Project to create effective security policies to define the acceptable use of information and assets. Locate cybersecurity policy templates at https://www.sans.org/security-resources/policies.
- Invest in Training and Certifications - Even the most innovative cybersecurity technologies wont work effectively if cybersecurity personnel are not properly trained and certified. Trained personnel can make up for the shortcomings of a cybersecurity program by applying their tradecraft based on leading industry certifications.
- Acquire Cybersecurity Insurance - One of the fastest growing cybersecurity categories is data breach and cybersecurity policies. This type of insurance can serve as an effective stopgap for cybersecurity programs under development. It is important to note however, that just because you have one of these types of insurance policies doesnt mean youre off the hook from properly protecting your information and assets.
The advice from the previous chapter holds true for this chapter: you cannot consider this portion of your program complete by finishing just these three activities. As with the previous chapter, go back through the balance of the material covered in the chapter to finish the buildout of the governance framework.
I once thought it was safe to assume everyone understood what governance was; that, however, turned out to be a rather fanciful notion. It is not that most people cannot cite some definition of governance ; it is they cannot provide practical working examples. Seems odd, right? Try it yourself; in the context of cybersecurity, quickly try to come up with a definition of governance. See what I mean? To some, governance includes all the letters of GRC (governance, risk, and compliance); to others it includes just two of the letters of GRC, and so on. At this point in the process, I want you to think only of the G in GRC.
Next pageFont size:
Interval:
Bookmark:
Similar books «Building an Effective Cybersecurity Program»
Look at similar books to Building an Effective Cybersecurity Program. We have selected literature similar in name and meaning in the hope of providing readers with more options to find new, interesting, not yet read works.
Discussion, reviews of the book Building an Effective Cybersecurity Program and just readers' own opinions. Leave your comments, write what you think about the work, its meaning or the main characters. Specify what exactly you liked and what you didn't like, and why you think so.










