Hacking with Python
The Ultimate Beginne r s Guide
Introduction
This book will show you how to use Python, create your own hacking tools, and make the most out of available resources that are made using this programming language.
If you do not have experience in programming, dont worry this book will show guide you through understanding the basic concepts of programming and navigating Python codes.
This book will also serve as your guide in understanding common hacking methodologies and in learning how different hackers use them for exploiting vulnerabilities or improving security. You will also be able to create your own hacking scripts using Python, use modules and libraries that are available from third-party sources, and learn how to tweak existing hacking scripts to address your own computing needs.
Thank you and I hope you enjoy it!
Copyright 2017 by Steve Tale All rights reserved.
This document is geared towards providing exact and reliable information in regards to the topic and issue covered. The publication is sold with the idea that the publisher is not required to render accounting, officially permitted, or otherwise, qualified services. If advice is necessary, legal or professional, a 21practiced individual in the profession should be ordered.
- From a Declaration of Principles which was accepted and approved equally by a Committee of the American Bar Association and a Committee of Publishers and Associations.
In no way is it legal to reproduce, duplicate, or transmit any part of this document in either electronic means or in printed format. Recording of this publication is strictly prohibited and any storage of this document is not allowed unless with written permission from the publisher. All rights reserved.
The information provided herein is stated to be truthful and consistent, in that any liability, in terms of inattention or otherwise, by any usage or abuse of any policies, processes, or directions contained within is the solitary and utter responsibility of the recipient reader. Under no circumstances will any legal responsibility or blame be held against the publisher for any reparation, damages, or monetary loss due to the information herein, either directly or indirectly.
Respective authors own all copyrights not held by the publisher.
The information herein is offered for informational purposes solely, and is universal as so. The presentation of the information is without contract or any type of guarantee assurance.
The trademarks that are used are without any consent, and the publication of the trademark is without permission or backing by the trademark owner. All trademarks and brands within this book are for clarifying purposes only and are the owned by the owners themselves, not affiliated with this document.
Table of contents
Chapter 1: Preparation for hacking
Every aspiring hacker should learn how to use a programming language in order to discover and exploit weaknesses in a computer. While there is nothing wrong with using resources that are already made available, you will want to develop better tools that can allow you to make better use of your own computer. Because you are the best judge when it comes to understanding your own needs, you are aware that many of the existing tools available online or in the market lack some of the features that you may need to make your computer perform just the way you want it.
The computing world changes every day new hacks are developed by the hour and you can also expect that different security experts discover them. If you are stuck on using old hacking tools to either perform reconnaissance or protect yourself from a possibility of an attack, then you are likely to run into some trouble. For example, launching a malware on a targeted machine that has already improved its security system will not only cause your attack to fail the likelihood of the attack being traced back to you is also high.
Learning a programming language will also allow you to increase your probability of hacking success and decrease the likelihood of getting detected by IDS (intrusion detection systems), antivirus software, or tools that are used by law enforcement. If you are learning how to be a white hat hacker by learning how criminal hackers act and develop their own tools for system exploitation and manipulation, then you will definitely be able to use updated security codes to combat new cracking programs that are developed every day. By being able to code programs on the go, you will also be able to detect and prevent attacks as they happen.
Being able to code your own hacking tools will also allow you to contribute to the community of hackers that are sharing their resources with you by discovering a better way to perform an attack, do a countermeasure against an illegal hack, or update security protocols or abilities of a known tool, you will be able to do your share in making the computing world a more secure place to be in.
What is Python?
Python is considered an open source language, which means that you can download it from the python.orgs website free of charge. This high-level language has been around since the late 80s, but has definitely survived the test of time it is still used today to create GUIs, web apps, games, and more importantly, hacking exploits and intrusion mitigation.
If you are migrating from another programming language, you will be able to easily learn Python thanks to its easy readability. Most of the commands use typical English statements which will allow you to immediately understand their purpose even if it is the first time that you have encountered this language. Python codes are also so much shorter and simpler compared to other high-level languages such as Java, and comes with a library and features that are already built-in, as well as access to third-party modules and libraries. Its robust integrated libraries and the availability of resources that are compiled by other users make it one of the favorite programming languages of hackers.
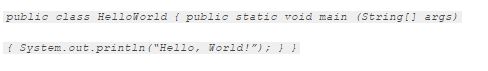
Heres an example: if you want to perform the classic Print command to type out Hello, World! using Java, you will have to type out the following:
However, Python will just require you to key in the following:
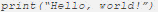
At this point, you get the idea that a complete hacking script will be much simpler and shorter using Python, compared to other high-level languages that are typically used for creating programs.
If you are a first-time programmer, you will find Python to be relatively easy to learn, thanks to its simpler codes and syntax. You will also be able to run your codes on different types of devices and operating systems, such as Android, Windows, Linux, and Mac OS X. If you are interested in jumping right into hacking, you will definitely have endless fun discovering what you can manipulate with your own programs Python does not only allow you to exploit and manipulate laptops, smartphones, and desktops, but also allow you to run your programs on microcontrollers that are found in toys, remote controls, appliances, and virtually any device that has a computer in it.
Starting with Python
If you are using a recent Linux or UNIX distribution, you probably have the Python installed already. Some Windows users, particularly HP computer owners, may also have it installed in their computers. However, if you need a fresh install of the package, you can download it from www.python.org .