INTRODUCTION
This book is just a starting of a full series, In which we will go through the depth of internet security and techniques used by top professionals in this field. We will explain everything as simple as we can.
Coming to this book, we have explained some beginning ideas of internet security tricks. How some very common hacks. Easy to understand.
We have included some Bonus Video tutorials with this small E-Book for our first 100 Buyers.
Thanks !
Abhishek Sagar
index
- Phishing How Hackers Steal your information
- Anonymity
- SQL Injection How a Hacker, Hacks a website
- Hex Editing Modding, Manipulations of Hexadecimal Data
- Key logger
PhishinG
the art of stealing
According to Wikipedia
Phishing is the attempt to acquire sensitive information such as usernames, passwords, and credit card details (and sometimes, indirectly, money), often for malicious reasons, by masquerading as trustworthy entity in an electronic communication.
So how do a hacker steal such information from you?
Okay lets get started.
First a hacker creates a fake login page, which looks like an original page and somehow, convince you to enter your usernames and passwords to it.
By sending fake offers, promises or any other eye catching things.
This can be done by the means of SMS, MMS, On Social Networking Sites.
This is how a fake E-mail Looks Like
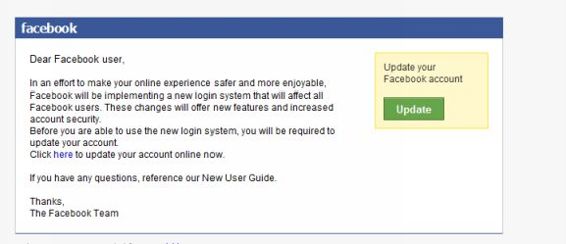
A Hacker can send you a email with any email id (We will discuss it later)
And when you click this update button above, you will be redirected to the fake Facebook page which is created to steal your information.
This page is designed in such a manner that after stealing your information you will be redirected to the original Facebook page. Smart, right
Lets see how a fake login page looks like:
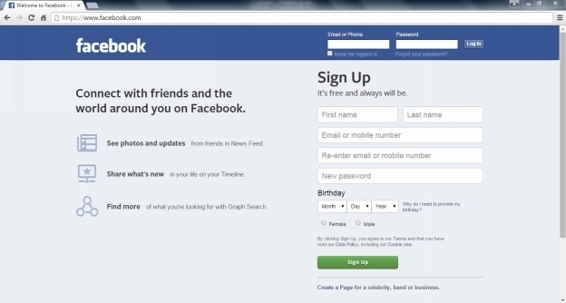
Everything is normal in this image. Right ?
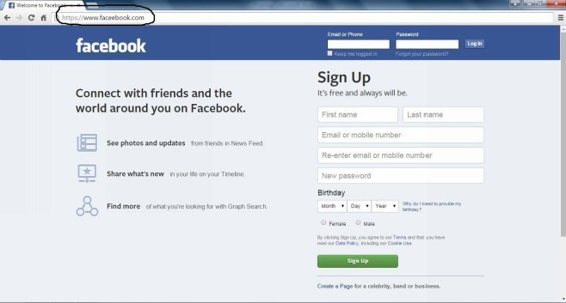
Now look at the rounded area The Address Bar. Its https://faceebook.com an extra e which is an ideal way of trapping users. Making a similar looking address.
This is how a basic phishing hack works. It works for all websites and even for bank accounts, when the user is not aware of this kind of hack.
So, Always look for an address bar for your safety.
Phishing is illegal, and by this method many criminal minded peoples are stealing information from common peoples who does not have a proper knowledge of cyber tricks and hacking.
ANONYMITY

Anonymity is the state when nobody knows who you are on the Internet.
This State is used by Hackers Worldwide to perform their activities so that no one can trace them.
Internet Protocol (IP)
Internet protocol is an unique numeric identification number of every individual internet user which can be used to track your name, geographical location and your online activities.
An IP Looks like this
225.2.665.233
This is your address and to this address the data is being sent by your internet provider as data packets and this is how your internet works.
Hackers hide their identification on the internet to perform hacking activities so that no one can trace them.
How Hackers Hide their IP?
There are so many of ways to hide an IP, lets discuss about them.
VPN (Virtual Private Network)
VPN is a network that is constructed by using public wires, usually the internet.
To connect to a private network, such as a companys internal network. There are a number of systems that enables you to create networks using the internet as the medium for transporting data.
How VPN Works?
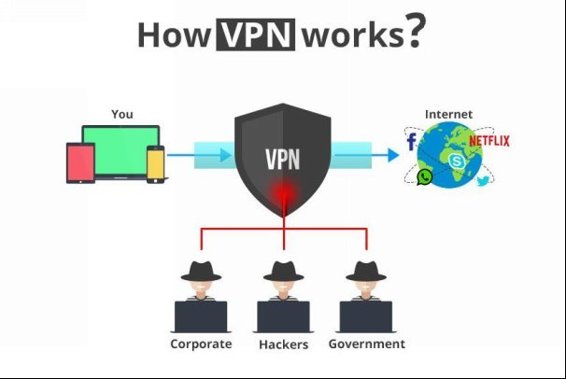
VPN Works as a medium between you and the internet, the data is first received by the VPN server than it will come to your computer.
Proxy Servers
A proxy or proxy servers is basically another computer which serves as a hub through which internet requests are processed. By connecting through one of these servers, your computer sends your requests to the proxy servers which then processes your request and returns what you were wanting.
This way you IP is not shown to the tracker.
TOR BROWSER (The Onion Reuter)
Tor browser is the best software for anonymous browsing till date.
Even FBI cant trace it easily. This works on layer IP basis. A circuit of different internet protocol is created (minimum 8 ) which acts as layers. (just like layers of an onion)
The data is first received by first IP than transferred to second than third and so on. Then finally you get the data on your browser. This is the first tool every hacker should have and surprisingly this is a free software. Very less people know about this browser.
sql injection
website hacking
According to Wikipedia
SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker).

A Basic HTML Website does not contain a SQL database which is based on structured query language. So This type of hack works only for SQL based websites.
What is a Database? Why it is Important for a website.
Database is a collection of data which is called by an application when required.
For explaining this lets take help from an example.
An attendance register of a class room contains daily attendance records for each student, you can say this is a database of class attendance. Whenever there is a requirement of counting attendance of any student, the register is taken for analysis, same thing happens in a website. Whenever a new user got registered on a website, his all information kept stored in database of the website for future.
How a Hacker Hacks a Website?
Data is Stored in a Database with SQL (Structured Query Language) Even the Administration data. So if somehow hacker gained access to the database, he can get the stored administration password (Owners Password to gain access to Websites Admin panel. Where you can add contents or even completely delete the website)
But this is not Enough, Many Criminal Hackers Gain access to the database of Online Shopping Websites to get Stored Credit Cards and other Confidential information and they Make Money With it.
At first Hacker Scan the whole website for Vulnerabilities in database.
After finding a loophole, he injects malicious codes in the database.
Than Finally the database is accessed and dumped (Downloaded to his computer with all the information)
SQLI Dumper
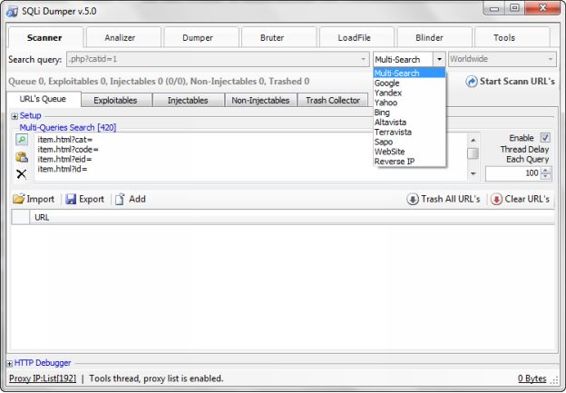
SQLI Dumper is a secret program developed to find out weak security websites from the internet and this program is powerful enough to dump databases quickly.
Next page

















