Cybersecurity and cyber resiliency are the number one concerns for companies today. Organizations must protect their assets and defend against threats and attacks in order to stay in business. A break-in or breach can destroy a companys assets and/or reputation in a matter of minutes. Readiness is key, so that if the unthinkable happens, your company will have the tools and action plans to counter and recover from the attack.
Developing a cybersecurity and cyber resiliency strategy that supports the business and is resource efficient requires strategic planning. Most organizations lack the necessary experience to conduct the appropriate planning required to streamline efforts, while minimizing risks, as they strive toward their long-term strategic business objectives.
The cybersecurity profession is growing exponentially. Although there are numerous universities and technical schools that provide degrees in these new fields, they are not teaching how to develop a strategy: one that is unifying that allows an organization to develop a risk-based, efficient, and targeted effort that will be approved by top company management.
The cyber resiliency field is even younger, evolving from the traditional fields of disaster recovery and business continuity. It is, however, not fine-tuned to the cybersecurity threats of today and struggles to identify and prepare for the threats of tomorrow. There is much more growth that must happen in this arena in order for organizations to feel comfortable with their cyber programs in an age of persistent and advancing threats.
In larger organizations, pockets of cybersecurity and cyber resiliency can be found in company silos such as specific business units. A business unit or silo can have its own information security and disaster recovery/business continuity strategy that may or may not roll up into an enterprise-wide effort. Also, if a company has acquired other companies and joined additional networks, each legacy company or business unit will surely have their own policies, procedures, standards, and/or frameworks they follow. All of these strategies may have conflicting goals and not focus on the highest priority business objectives.
In order to respond to todays threats in a cohesive manner, communications and threat intelligence must utilize a common language and risk metrics. Defining a taxonomy for risks, threats, vulnerabilities, and controls will facilitate an effective and measurable response.
This book will provide concepts, processes, roadmaps, project development tools, and reporting templates to be used by any type of company in order to develop their enterprise-wide cybersecurity and cyber resiliency strategies. This book delivers a methodology for companies to bring together their disassociated strategic planning efforts into one corporate-wide strategy that will efficiently utilize resources, target high risk threats, evaluate resultant risk mitigation efforts, while engaging buy-in across the corporate culture, senior management, business silos, and diverse business interests. A mid-level manager, as well as a CISO or CIO, can use this book to create very real strategies that can be published by the Board of the company and approved by their supervisory entities. By using the unifying techniques discussed later, the strategy sponsor can assimilate strategies from other areas of the company that may be in development and align and/or incorporate them into a central enterprise-wide strategy.
The book will discuss the steps and tasks required from conception of the strategy through its planning, creation, success and performance measurement techniques, management reporting, and planning for future ongoing efforts.
In order for an organization to develop and maintain its cybersecurity and cyber resiliency strategy, there are 6 major STEPs that should be taken. If performed, the organizations cybersecurity and cyber resiliency strategy will be comprehensive, functional, long lasting, and have continued buy-in and support from senior management. They are:
STEP 1: Preplanning: Preparation for Strategy Development
STEP 2: Strategy Project Management
STEP 3: Cyber Threats, Vulnerabilities, and Intelligence Analysis
STEP 4: Cyber Risks and Controls
STEP 5: Current and Target State Assessments
STEP 6: Strategic Plan Performance Measurement and End of the Year (EoY) Tasks
The 6 Development and Annual Maintenance STEPs for a Cybersecurity and Cyber Resiliency Strategy () show a sequential representation of the 6 STEPs required.
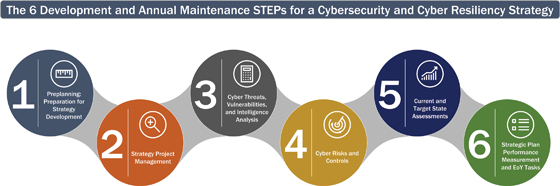
Figure 1.1 The 6 Development and Annual Maintenance STEPs for a Cybersecurity and Cyber Resiliency Strategy.
Each of the 6 STEPs will be discussed in detail throughout the book and methodologies presented for their approach and execution. NOTE: In striving to keep applicability of the strategy particulars and processes presented here current and continuously timely, the authors have decided to make this book technology agnostic, thereby not dating any particular technology, objective, initiative, or conclusion.
What job functions and management levels of people in an organization might need this information? The most obvious people would be any one in the information security, cybersecurity, cyber resiliency, business continuity/disaster recovery, and resiliency areas that are tasked with developing a strategic action plan to combat cyber threats and attacks over the longer term. This would include, but not be limited to, such roles as shown in .
TABLE 1.1 Cybersecurity and Cyber Resiliency Strategy Key Players
Developers, Approvers, or Readers |
|---|
Chief Information Security Officer (CISO) Chief Information Officer (CIO) Chief Technology Officer (CTO) Cyber/Security Architect Cyber/Security Engineer Security Administrator Cyber/Security Manager Security Software Developer Security Incident Responder Cryptographer Cybersecurity/Resiliency Consultant Data Security Strategist Chief Resiliency Officer Business Continuity Analyst Disaster Recovery Manager Resiliency Engineer Business Preparedness and Resiliency Program Manager Global Resiliency Project Manager
|
However, it is not just the security professionals who need to be concerned with a cyberattack. Increasingly more regulations are demanding accountability from senior management when there is a breach. Not just CISOs and CIOs, but also Chief Operating Officers (COO) and Chief Executive Officers (CEO) can be legally liable. Every level up the food chain can be deemed responsible and might have to pay penalties.
In fact, any one of the above job roles might have already initiated a cybersecurity or cyber resiliency strategy independently. From a top down perspective, it is clearly easier if a strategy is created and approved from a senior manager or c-level position as that level of management can authorize and dedicate the appropriate resources to the task more easily. In addition, a c-level or senior vice president frequently interfaces with governing boards and oversight bodies and is more apt to get buy-in more quickly. However, if the strategy is assigned to a subject matter expert (SME) further down the food chain, this approach will give him/her all the information and steps necessary to work the strategy up the corporate structure and get all the relevant participants involved.











