Martin Gardner

CODES, CIPHERS
AND SECRET
WRITING
Dover Publications, Inc.
New York
For
QSVVZ ZYTZC KJLQZ
Copyright
Copyright 1972 by Martin Gardner.
All rights reserved.
Bibliographical Note
This Dover edition, first published in 1984, is an unabridged and un ltered republication of the work first published by Simon & Schuster, Inc., New York, in 1972.
ltered republication of the work first published by Simon & Schuster, Inc., New York, in 1972.
Library of Congress Cataloging in Publication Data
Gardner, Martin, 1914
Codes, ciphers, and secret writing.
Reprint. Originally published: New York : Simon & Schuster, cl972. Bibliography: p.
1. Cryptography. 2. Ciphers. I. Title.
[Z103.G3 1984] 001.54'36 84-8024
ISBN-13: 978-0-486-24761-8
ISBN-10: 0-486-24761-9
Manufactured in the United States by Courier Corporation
24761917
www.doverpublications.com
Contents
Cryptography, the writing and deciphering of messages in secret code, and other forms of secret writing have always played, and still play today, vital roles in the history of every nation. It is necessary in this crazy world of ours for governments and spies to send special information in secret ciphers. It is just as necessary for every major nation to have a staff of expert cryptanalysts who work day and night, with electronic computers at their elbows, to crack the codes used by other countries. The history of cryptanalysis (so marvelously told by David Kahn in his comprehensive book The Codebreakers ) is a fascinating one, filled with dramatic incidents in which the fates of empires and political leaders hinged on the success or failure of a small group of specialists in this ancient, curious kind of puzzle solving.
I say small because in earlier centuries such work was often done by only a few cryptanalysts, sometimes only by one man. Today, codebreaking is a vast and rapidly growing profession. No one knows exactly how many people are now engaged in codebreaking for the United States, but they certainly number in the tens of thousands and cost us more than a billion dollars a year. During World War II, 30,000 persons in Great Britain alone were assigned to such work. It is probably our governments most reliable method of gathering intelligence.
The United States Navys great victory at Midway Island in 1942 was a direct consequence of our having learned the secret of Japans PURPLE machine code, a remarkable feat of codebreaking that will be described in . In the same war Germanys 1943 U-boat victories against Allied shipping were the result of Germany having broken the British merchant ship code. The tide did not turn until American and British cryptanalysts solved the cipher that was being used by German submarines.
The most sensational solution of a single coded message in recent history occurred during World War I. In 1917 Arthur Zimmermann, the German foreign minister, sent a cable to Mexico, using a diplomatic code called 0075. It announced Germanys plan to begin unrestricted submarine warfare. If America entered the war, the cable continued, Germany promised to give Mexico the states of Arizona, Texas and New Mexico if Mexico would only join in fighting against the United States. The cable was intercepted and the code broken by British intelligence, then passed on to President Woodrow Wilson.
America had been reluctant to enter the war. But news about the Zimmermann telegram so enraged Congress and the public that we declared war on Germany. Had we not done so, it is probable that Germany would have won the war. Never before or since, writes Kahn, has so much turned upon the solution of a secret message.
Interest in cryptography is not restricted to governments and professional spies. Everybody enjoys a secret. Surely that is one reason why so many young people like to send and receive coded messages even when there is no special reason for them to be secret. Coded messages are fun to encipher (put in cipher form) and decipher (translate back to the original), and it is even more fun to break a code used by someone else. If you belong to a secret club, you and your friends may want to communicate with one another by one of the methods explained in this book. If you keep a diary, you may wish to protect it from prying eyes by using a code.
Many famous people have written all or parts of their diaries in code. When Franklin Delano Roosevelt was twenty-one, he used a cipher for four entries in a diary he was then keeping. In 1971 these entries were shown for the first time to several cryptographers, who had no trouble breaking the code. It was a simple substitution cipher using numbers for vowels and symbols for consonants. The translations proved to be so tame that one wonders why young Roosevelt bothered to put the entries in code.
If you are clever and diligent, you, too, can learn how to break secret codes. The solving of substitution ciphers is now a popular type of puzzle with enough fans to support a daily cryptogram in hundreds of newspapers throughout the country. There is even an American Cryptogram Association which publishes a bimonthly periodical called The Cryptogram. (If you are interested, you can write to the treasurer at 604 W. Monroe St., Mexico, Missouri 65265.) will introduce you to the exciting art of solving cryptograms.
The main purpose of this book, however, is to teach you how to use the most important codes, and other methods of secret communication, that have been invented since ancient times. A selected list of references at the end of the book will provide more reading material about the unusual techniques that have been employed for making ciphers, and for breaking ciphers used by others.
I am indebted to David B. Eisendrath, Jr., for many excellent suggestions which I have followed in , and to David Kahn for writing The Codebreakers, my principal source of information.
M ARTIN G ARDNER
Easy
Transposition
Ciphers
A transposition cipher is one that does not change any letters of the original message. (Cryptographers call the original the plaintext but we will simply call it the message.) It merely rearranges the letters, according to a secret system, so that anyone who knows the system can put the letters back in their proper order and read the message.
The simplest transposition cipher is made by just writing the message backward. AGENT 427 IS ON HIS WAY becomes YAW SIH NO SI 724 TNEGA. If the message happens to be a palindromea sentence that reads the same in both directionsthe letters will be in exactly the same order when reversed. For example: PULL UP IF I PULL UP, or TIS IVAN ON A VISIT. This is not likely to happen, however, with any genuine message.
The main trouble with backward writing is that it is too easy to recognize. If you keep the original word order, but reverse the letters of each word separately, the reversal is a bit harder to spot, but not much. The following transposition ciphers are better and almost as easy to remember and use.
Suppose you wish to encipher this message:
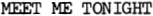
Count the number of letters. If the number is a multiple of 4, well and good. If not, add enough dummy letters at the end to make the number a multiple of 4. In this case there are 13 letters so we add three dummy letters, QXZ, to total 16. Such dummy letters are called nulls. In a moment we will see why the nulls are added.
Write the message by printing every other letter a trifle lower on the page. The message will look something like a rail fence:
Next page


















 ltered republication of the work first published by Simon & Schuster, Inc., New York, in 1972.
ltered republication of the work first published by Simon & Schuster, Inc., New York, in 1972.