Anirban Sengupta
Indian Institute of Technology Indore
Institute for Development and Research in Banking Technology, Hyderabad
1.1 Introduction
IoT is omnipresent in todays world. IoT applications find space in smart homes, smart cities, smart healthcare systems, wearable electronics, smart grids, connected cars, and in many other applications. The Internet of Things can exist with conventional microcontrollers and System on Chips (SoCs), but issues such as low power requirements and wireless support have accelerated the development of platforms designed for IoT applications. Thus, DSP coprocessors play a pivotal role for developing SoC-based IoT applications (. This chapter discusses four state-of-the-art structural obfuscation approaches proposed by various researchers. All these approaches target DSP application for providing protection. The analysis of their corresponding results is shown in the subsequent section.
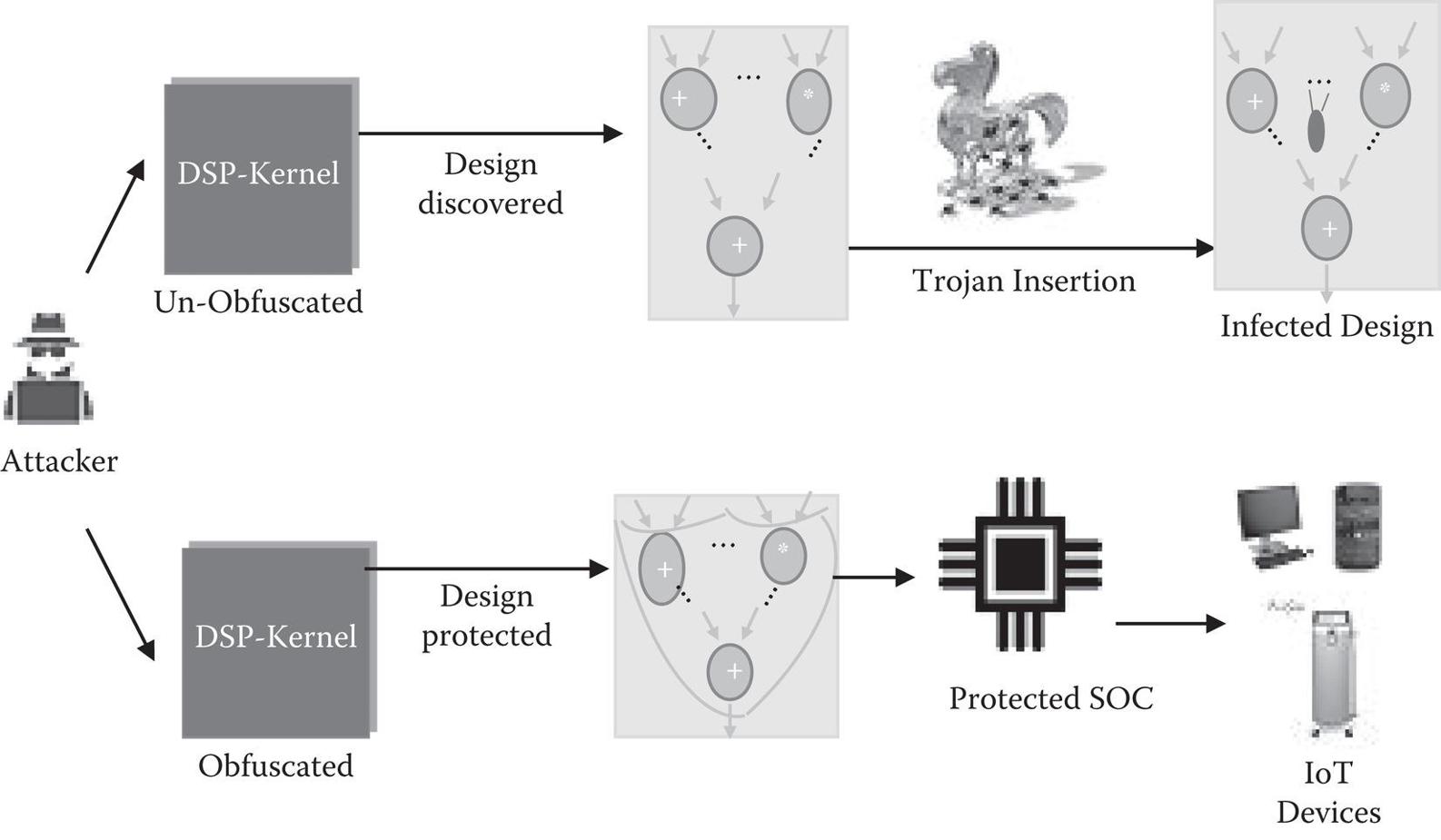
Figure 1.1
Typical attack and protection scenario for IoT devices.
1.2 Discussion on Contemporary Structural Obfuscation Approaches used for Securing DSP Hardware/Coprocessor
Workflow of the methodology is shown in .
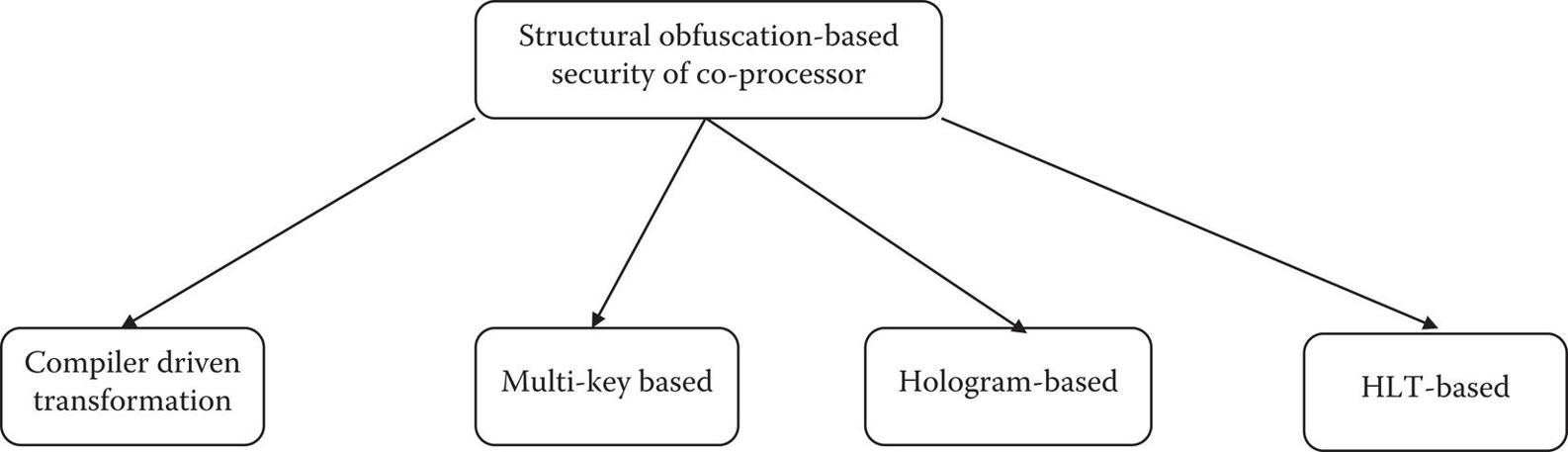
Figure 1.2
Workflow of structural obfuscation-based security methodology for co-processor design.
1.2.1 Securing DSP Designs Using Compiler Driven Transformation Based Structural Obfuscation
The methodology proposed by .
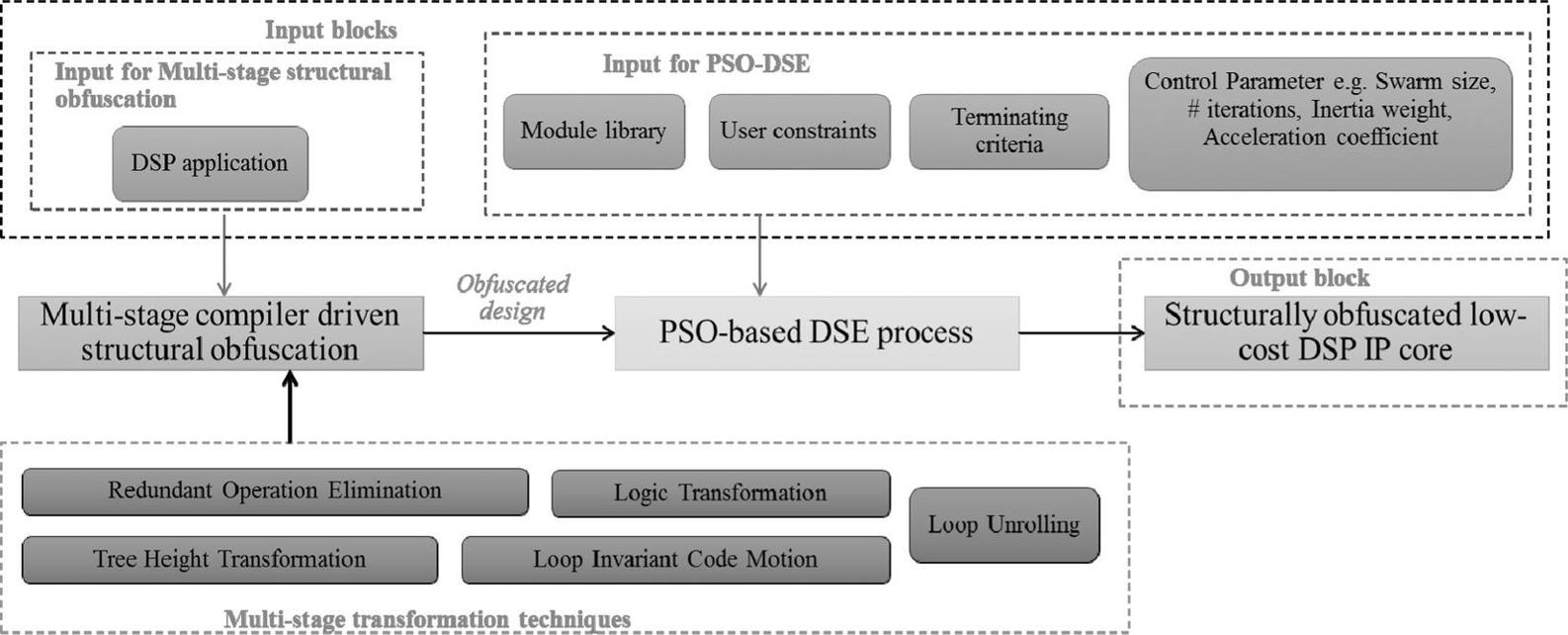
Figure 1.3
Overview of low-cost compiler driven structural obfuscation approach.
Redundant Operation Elimination: ROE is one of the compiler-driven transformation techniques used for generating a structurally obscured but functionally equivalent RTL DSP design. This technique removes redundant operations from the application. As mentioned earlier, the inputs are accepted as a CDFG; therefore, each operation of the application is represented as a node. Each node accepts input data from its parent nodes and after processing passes the output to its child node(s). A redundant operation can be identified if two nodes have the same parents as well as the same operator to process the data. A search algorithm based on the aforementioned rules runs on all the operations of the application based on their node number in ascending order to identify the list of redundant operations. Whenever a pair of redundant nodes is identified, the node with the higher node number is removed from the CDFG. Thereafter, the child of the removed node is adjusted as the child of the equivalent node. Thus, the correctness of the design is preserved. To verify the same, functional equivalence testing is performed before and after applying ROE. ROE can decrease the total node count of the application. It can also change the dependencies between nodes ().
Logic Transformation: LT is another compiler-driven transformation technique used for generating a structurally obscured but functionally equivalent RTL DSP design. This technique breaks the application into multiple sub-functions and then generates logical equivalence of each sub-function. It then replaces each sub-function with the currently generated sub-function. In the CDFG representation of an application, LT may alter one node with multiple nodes or vice-versa with different input values or operators, or both. To identify the list of sub-functions where LT can be applied, a search algorithm is run on all the possible sub-graphs that can be generated from the CDFG. Each sub-graph is then transformed and replaced with its logical equivalence graph. The parents (primary inputs), child and the dependencies of each sub-graph are adjusted accordingly to preserve the correctness of the design. To verify the same, functional equivalence testing is performed before and after applying LT. Here, LT can increase or decrease the total node count of the application. It can also change the operator type, the number of primary inputs, and the dependencies between nodes (). All these significantly contribute in structurally obfuscating (obscuring) when its equivalent RTL datapath is generated using DSE and HLS.
Tree Height Transformation: THT is another compiler-driven transformation technique used for generating a structurally obscured but functionally equivalent RTL DSP design. This technique converts the consecutive computations of serial operations into multiple parallel sub-computations. In other words, it introduces parallelism in sub-computations by modifying a long chain-like serial computation. In the CDFG representation of an application, THT replaces the serial dependencies with larger tree height into several parallel dependencies with lesser height. Therefore, THT not only decreases the height of the tree but increases the width of the tree (i.e., number of possible parallel executions). It may also reduce the length of the critical path of the CDFG. To identify the list of serial dependencies where THT can be applied, a search algorithm is run on all the paths starting from primary inputs to the final outputs. It identifies each associative operation that is executed serially; if the path length is three or more, THT can be applied to it. The parents, child and the dependencies of each sub-computation are adjusted accordingly to preserve the correctness of the design. To verify the same, functional equivalence testing is performed before and after applying THT. THT can increase or decrease the total height of the graph, the total number of possible parallel executions and can change the dependencies between nodes (). All these significantly contribute in structurally obfuscating (obscuring) when its equivalent RTL datapath is generated using DSE and HLS.
Loop Unrolling: LU is another compiler driven transformation technique used for generating a structurally obscured but functionally equivalent RTL DSP design. It is only applicable for loop-based applications. This technique converts the loops into their unwound form. In the CDFG representation of an application, LU unrolls the graph into multiple copies and executes the same calculation several times in parallel. The number of copies is decided by what is known as the unrolling factor. It may increase the area consumption of the design but decreases the execution latency, as multiple iterations can be executed in parallel. LU is applicable to all the loop-based applications. The primary inputs and outputs of each unroll are adjusted accordingly to preserve the correctness of the design. To verify the same, functional equivalence testing is performed before and after applying LU. LU can increase the number of nodes of the application (. The amount of obfuscation, also known as Strength of Obfuscation (SoO) depends on the unrolling factor besides the other transformations explained earlier.
Loop Invariant Code Motion: LICM is another compiler driven transformation technique used for generating a structurally obfuscated but functionally equivalent RTL DSP design. It is also only applicable to loop-based applications. This technique splits up the loop's independent operations from the loop body. In the CDFG representation of an application, LICM moves out those nodes from the loop body; this doesnt make any difference if it executes iteratively inside the loop or for a single time outside the loop. Therefore, it decreases the execution latency and alters the structure of the graph, without affecting the area consumption. To identify the list of a loop's independent operations, a search algorithm is run on all the nodes of the application based on their node number in ascending order. The parents, child and the dependencies of the loop's independent nodes are adjusted accordingly to preserve the correctness of the design. To verify the same, functional equivalence testing is performed before and after applying LICM (). LICM has capability to alter the structure of the CDFG, thus obfuscating its corresponding RTL datapath.