Hatch - Hacking exposed Linux: Linux security secrets & solutions
Here you can read online Hatch - Hacking exposed Linux: Linux security secrets & solutions full text of the book (entire story) in english for free. Download pdf and epub, get meaning, cover and reviews about this ebook. City: New York, year: 2008, publisher: McGraw-Hill Education, genre: Computer. Description of the work, (preface) as well as reviews are available. Best literature library LitArk.com created for fans of good reading and offers a wide selection of genres:
Romance novel
Science fiction
Adventure
Detective
Science
History
Home and family
Prose
Art
Politics
Computer
Non-fiction
Religion
Business
Children
Humor
Choose a favorite category and find really read worthwhile books. Enjoy immersion in the world of imagination, feel the emotions of the characters or learn something new for yourself, make an fascinating discovery.

Hacking exposed Linux: Linux security secrets & solutions: summary, description and annotation
We offer to read an annotation, description, summary or preface (depends on what the author of the book "Hacking exposed Linux: Linux security secrets & solutions" wrote himself). If you haven't found the necessary information about the book — write in the comments, we will try to find it.
Hatch: author's other books
Who wrote Hacking exposed Linux: Linux security secrets & solutions? Find out the surname, the name of the author of the book and a list of all author's works by series.
Hacking exposed Linux: Linux security secrets & solutions — read online for free the complete book (whole text) full work
Below is the text of the book, divided by pages. System saving the place of the last page read, allows you to conveniently read the book "Hacking exposed Linux: Linux security secrets & solutions" online for free, without having to search again every time where you left off. Put a bookmark, and you can go to the page where you finished reading at any time.
Font size:
Interval:
Bookmark:
.
Special thanks to Jonathan Bokovza,  ar
ar nas Grigali
nas Grigali nas, and Harald Welte for their timely assistance when a little help was required. Also special thanks to Jane Brownlow, Jennifer Housh, and LeeAnn Pickrell.
nas, and Harald Welte for their timely assistance when a little help was required. Also special thanks to Jane Brownlow, Jennifer Housh, and LeeAnn Pickrell.
MANAGEMENT AND MAINTENANCE
.
Being responsible for a computer environment is a task that requires thorough procedures and helpful tools. This appendix gives insight into the decisions a system administrator needs to make when setting up nodes, designing a network, and implementing tools that help in everyday system administration tasks. The first half of this appendix could be used as a sort of checklist, whereas the other half includes references to interesting projects and applications.
A best practices setup begins at its lowest level: the nodes. A node could be a server, a blackbox device, a workstation, or anything else that is connected to a network. The next few sections detail necessary decisions that influence the way you set up a node. The hints are intended to be operating-system independent, but the mentioned tools and commands have been tested on Linux.
Cryptography has been used in computers only for a short time. Therefore, many solutions and applications still transmit data unencrypted and unauthenticated. This increases the possibility of two common attacks:
 Sniffing passwords and other sensitive information off the wire
Sniffing passwords and other sensitive information off the wire
 Man-in-the-middle attacks
Man-in-the-middle attacks
Man-in-the-Middle Attack (MITM) |
The phrase man-in-the-middle attack refers to an attack in which an attacker is able to compromise a link between two parties in which they do not notice the compromise. This enables the attacker to read, insert, or manipulate transmitted messages at will. |
Using a network sniffer, such as Wireshark or tcpdump , you can reveal the contents of a clear-text network transmission. shows an example of Wireshark, which displays a clear-text HTTP connection with the help of the Follow TCP Stream function. Looking at that example, it is quite clear that the network communication was unencrypted and thus vulnerable.
Today's best practices solution against these threats is to use cryptographically secured services wherever possible. These services have three common characteristics:
 Data is transmitted encrypted, thus making it quite complex, if not impossible, for an attacker to discover the transmitted contents in clear text.
Data is transmitted encrypted, thus making it quite complex, if not impossible, for an attacker to discover the transmitted contents in clear text.
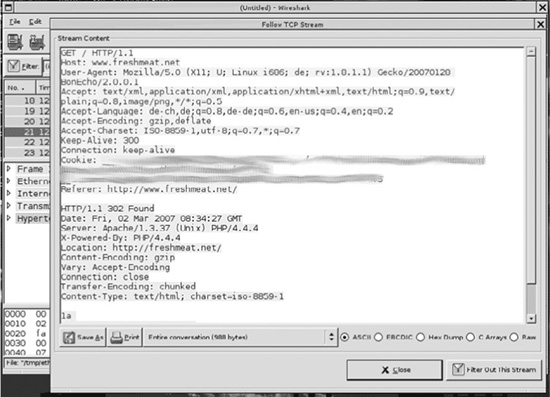
Figure A-1 Wireshark displays the contents of an unencrypted network connection.
 Each server and client involved in the communication can be identified. This makes spoofing an identity quite complex, if not impossible, for an attacker.
Each server and client involved in the communication can be identified. This makes spoofing an identity quite complex, if not impossible, for an attacker.
 Transmitted data is integrity checked, thus preventing unnoticed modifications on sent data.
Transmitted data is integrity checked, thus preventing unnoticed modifications on sent data.
A commonly used protocol that implements the cryptographic measures outlined here is HTTPS. All data is transmitted encrypted through SSL, and servers and clients can be identified through x.509 certificates. Although having a certificate isn't mandatory for clients, servers need to have one. Web browsers complain if a server certificate is considered invalid.
More resources are needed when using such cryptographically secured protocols as compared to their clear-text counterparts because they involve mathematical calculations. Fortunately, today's hardware renders the performance drawback practically unnoticeable, so there is no good reason not to deploy encrypted services.
Most of the protocols allow clear text and an encrypted variant (HTTP vs. HTTPS). Therefore, you need to take specific countermeasures to avoid users accidentally employing the clear-text variant (with the HTTP example, it would be possible to configure the server to accept only HTTPS connections).
A common attack to obtain access to a system is to brute-force usernames and passwords. The most promising prevention for this kind of attack is to avoid passwords altogether and switch the authentication method to one of the other available authentication techniques that are more resistant to such attacks (e.g., public key or smartcard authentication). The features and setup instructions vary depending upon the particular techniques. One popular service, where public key authentication is used, is SSH (the ssh-keygen man page includes setup instructions).
Brute-Force Attack |
A brute-force attack aims to circumvent security protection measures by trying a large number of possibilities. For example, a password might be circumvented by trying each possible combination of characters and numbers until access is granted. This attack can be especially successful in cases where users have weak passwords. Choosing long passwords that also contain additional characters and numbers increases the complexity needed to perform a brute-force attack successfully. A dictionary attack is very similar. As the name indicates, this attack uses a dictionary in order to circumvent the password protection. This type of attack will be successful in cases where passwords have been chosen that are included in dictionaries. A popular example is to use a dictionary containing first names to see if any users have used only a first name as password. |
An appropriate policy while configuring the services on a node is to generally deny everything and only allow what's specifically needed. For example, OpenSSH has configuration options for users that are allowed to log in. shows some of the configuration options that can be applied to sshd_config . The settings cover the following decisions:
 Is the root user allowed to log in?
Is the root user allowed to log in?
 Is anyone allowed to log in with an empty password?
Is anyone allowed to log in with an empty password?
 Is anyone allowed to log in with passwords at all?
Is anyone allowed to log in with passwords at all?
 Are only certain users or groups allowed to log in?
Are only certain users or groups allowed to log in?
If only public key authentication is used, why not disable password authentication completely in the services configuration? If only certain users need SSH access to a node, why not specifically only allow them in the service configuration? In a best practices setup, such considerations should be made and applied to the services configuration.
Font size:
Interval:
Bookmark:
Similar books «Hacking exposed Linux: Linux security secrets & solutions»
Look at similar books to Hacking exposed Linux: Linux security secrets & solutions. We have selected literature similar in name and meaning in the hope of providing readers with more options to find new, interesting, not yet read works.
Discussion, reviews of the book Hacking exposed Linux: Linux security secrets & solutions and just readers' own opinions. Leave your comments, write what you think about the work, its meaning or the main characters. Specify what exactly you liked and what you didn't like, and why you think so.





