About Author
Gurpej Singh writes books in computer science areas like Network Security, Cyber security and Ethical Hacking. His books have received starred reviews in Publishers Weekly, Library Journal, and Booklist.
He lives in the INDIA Before he started writing about Security .He got a under graduate degree in Computer Science and Engineering. After that, just to shake things up, he completed many courses, live experiences from Cyber Experts in Security field to become a Network Security Certified Specialist. He now writes full-time.
Network Security and Cyber Defence (CNSS)
This course provides a holistic view of modern network security including operating system hardening, rewalls, intrusion-detection systems, VPNs and Encryption.Physical Security, Standards, System Security and Security Policies are alsoincluded.
Course Objectives
Achieve skills to jump into penetration testing
Prepare for the Certied Network Security Specialist Exam
Audience System administrators, network administrators, security professionals, studentsand anyone who is interested in network security technologies.
Prerequisites
Basic Familiarity with Windows Operating System
1.Introduction To Network Security
1.1 Network Basics
Before diving into how to protect a network, exploring what networks are,would probably be a good idea.
For many readers this section will be a review, but for some it might be new material. Whether this is a review for you, or new information, having a thorough understanding of basic networking before attempting to study network security is critical. Also, be aware this is just a brief introduction of basic network concepts.
A network is simply a way for machines / computers to communicate.
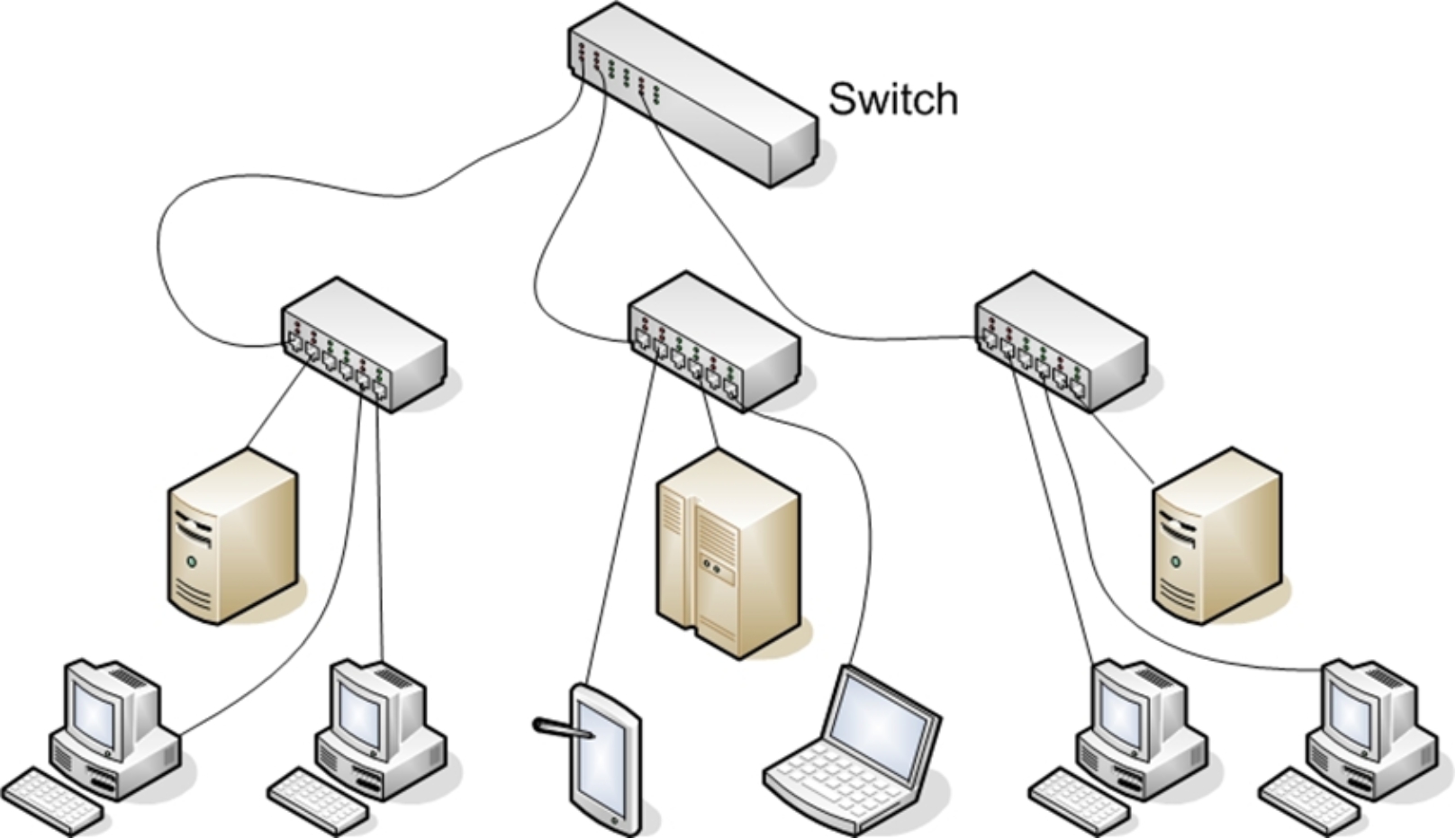
On a physical level, it consists of all machines that you want to connect and the devices that you use to connect them. Individual machines are connected either with a physical connection (a category 5 cable going into a network interface card, or NIC) or wirelessly. To connect multiple machines together, each machine must be connected to a hub or a switch. These hubs / switches must be connected together. In largernetworks, each subnetwork is connected to the others by a router
1.1.1 Basic Network Structure
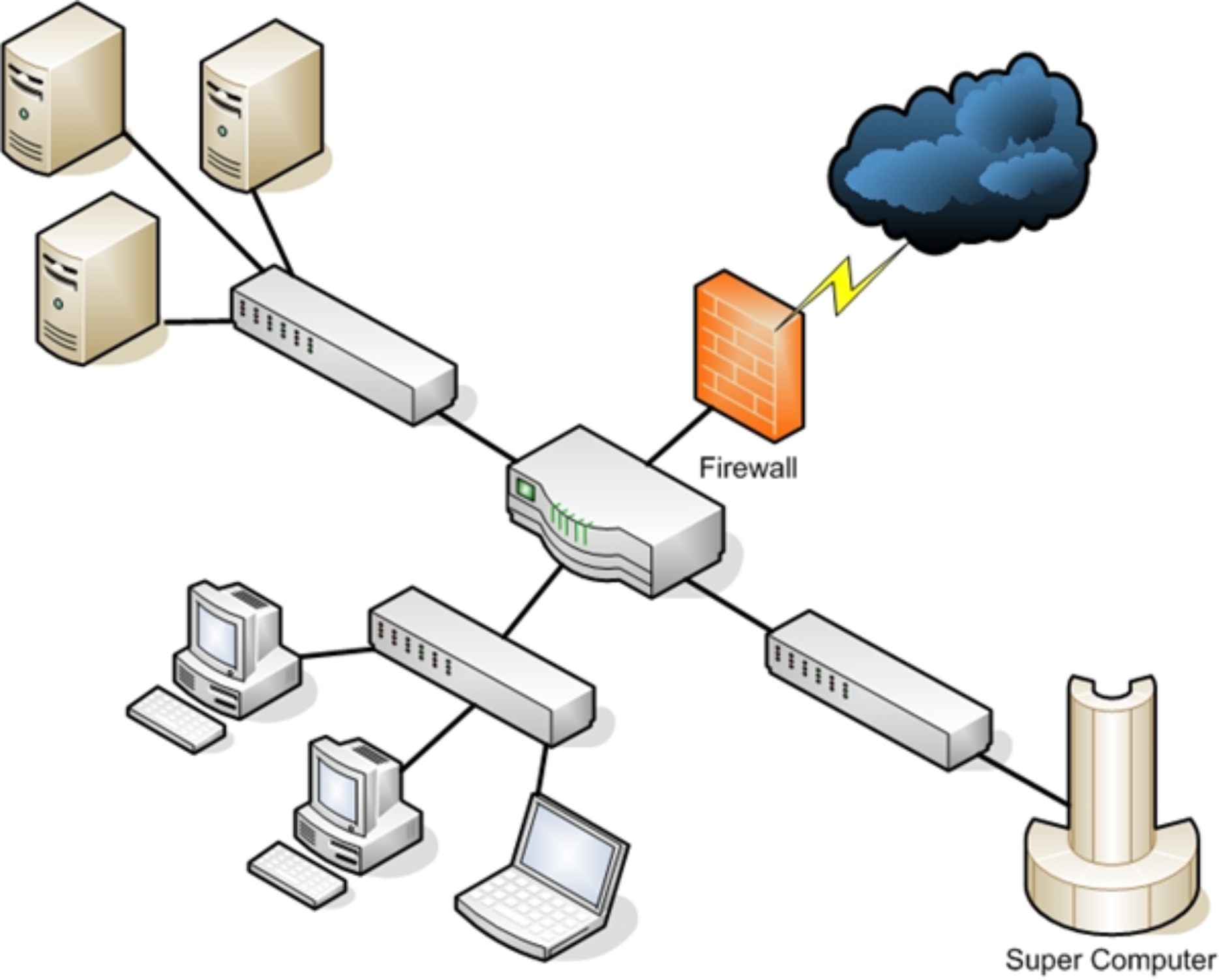
Connection point(s) must exist between your network and the outsideworld. A barrier is set up between that specic network and the Internet,usually in the form of a rewall. The real essence of networks is to allow communication from one machine to another.
However, every path of communication has a possibility for a potential attack. The rst step in understanding how to defend a network is having a detailed understanding on how computers communicate over a network.Network interface cards, switches, routers, hubs, and rewalls are the fundamental physical pieces of a network. The way they are connectedand the format they use for communication is the network architecture.
1.1.2 Data Packets
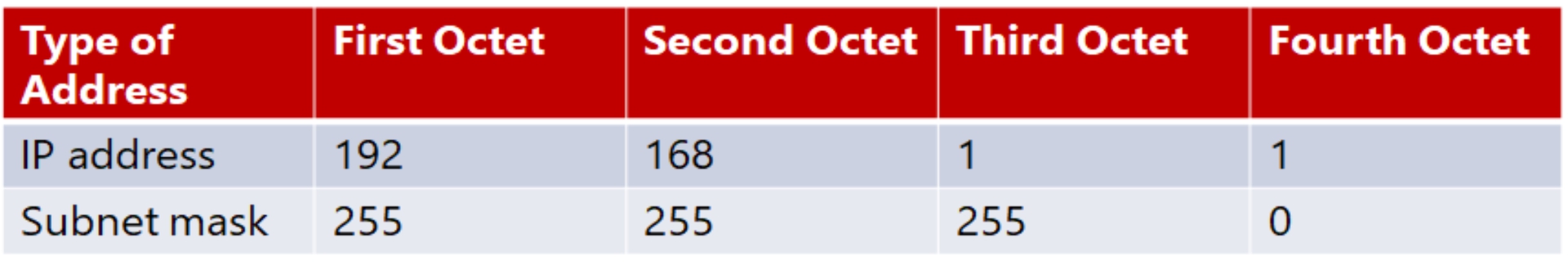
After you have established a connection with the network (whether it is physical or wireless), you need to send the data. The first part is to identify where you want it to be sent. All computers (as well as routers and switches), have an IP address that is a series of four numbers between 0 and 255 and is separated by periods, such as 192.168.0.1.
The second part is to format the data for transmission. All data is in binary form (1s and 0s). This binary data is placed into packets, roughly less than 65,000 bytes. The first few bytes consist of the header. This header states where the packet is going, where it came from, and how many more packets are coming as a part of this transmission. There is actually more than just one header, but for now we will discuss the header just as a single entity. Some attacks (IP spoofing, for example) try to change the header of packets in order to give false information. Other methods of attacks simply try to intercept packets and read the content (thus compromising the data).
A packet can have multiple headers. In fact, most packets will have at least three headers. The IP header has information such as IP addresses for the source and destination, as well as what protocol the packet is. The TCP header has information such as port number. The Ethernet header has information such as the MAC address for the source and destination. If a packet is encrypted with Transport Layer Security (TLS), it will also have a TLS header.
1.1.3 IP Addresses
The first major issue is to understand how packets reach their proper destination. Even small networks have many computers that could potentially be the final destination of any packet sent. The Internet has millions of computers spread out across the globe. How can you ensure that a packet arrives to its proper destination? This situation is no different than a letter not reaching its rightful destination. Lets begin by looking at IP version 4 addressing due to the fact that its the most commonly used in todays world. This section also briefly discusses IP version 6.
An IP version 4 address is a series of four three-digit numbers separated by periods (An example is 192.168.1.1.) Each of the three-digit numbers must be between 0 and 255. An address of 192.168.0.257 would not be a valid one. The reason for this rule is that these addresses are actually four binary numbers: The computer simply displays them to you in decimal format.
Recall that 1 byte is 8 bits (1s and 0s), and an 8-bit binary number converted to decimal format will be between 0 and 255. The total of 32 bits means that approximately 4.2 billion possible IP version 4 addresses exist.
The IP address of a computer highly informs you about that computer. The first byte (or the first decimal number) in an address reveals what network class the machine belongs to. Table 1-1 summarizes the five network classes.
Table 1-3 Five Network Classes
Class | IP Range | Use |
A | 0-127 | Used for large networks. All of them have been used |
B | 128-191 | Large corporate and government networks. All of them have been used |
C | 192-223 | Most common group of IP addresses. |
D | 224-239 | Reserved for multicasting |
E | 240-255 | Reserved for experimental use. |
The IP range of 127 is not listed in the above table. The IP address 127.0.0.1 designates to the machine you are on, regardless of the IP address assigned to your machine. This address is referred as the loopback address. This address is used to test the machine and the NIC card.