CHAPTER
A Little Bit of Everything
This chapter is a nod to everyone who has ADHD. Im going to constantly change topics, and none of them are going to fit together! Its the place where Im putting every topic that I wanted to discuss but wasnt long enough to have its own chapter.
Other IBM i 7.5 Enhancements to Be Aware Of
Ive already described some of the enhancements and changes in this release, but there are several more I want to point out.
- Its been best practice to change the sign-on messages CPF1120 - User xxx does not exist and CPF1107 - Password not correct to be the same text and to remove the message IDs so people with ill intent dont know which one theyve gotten wrong. IBM i 7.5 eliminates the need to change these messages. IBM has changed the text for CPF1120 to be User xxx does not exist or Password not correct for user profile. CPF1107 is no longer issued. New Nav also issues a generic sign-on failed message. Yay! This is a great enhancement because as many times as Ive recommended people do this, they rarely do!
- List functions (both commands and SQL Services), such as those that list the contents of a library or directory or objects secured with an authorization list, have been changed to require that the user has some authority to the object. In other words, if the user has *EXCLUDE to the object, it wont display in the list or be returned via a retrieve function. This change also ensures that what is returned by commands is the same list as is available via the SQL Services. (In some cases, an SQL Service returned objects the user didnt have authority to but the command did not.) Getting these list functions to return only what a user is authorized to is an important security change/enhancement. If a user doesnt have authority to an object, they absolutely have no reason to know it exists and definitely shouldnt be seeing information or statistics. This change can be overridden by changing the default setting or allowing some users access to the QIBM_LIST_ALL_OBJS or QIBM_LIST_ALL_OBJS_SQL functions (using the Function Usage feature in New Nav or the Work with Function Usage (WRKFCNUSG) command), but I highly recommend that you not change the default setting unless something truly breaks; and even then, perhaps the better (more secure) action would be to change the process rather than these functions.
- Another important change is similar to the previous bullet: Objects under /home will not be listed if users are excluded from them. Prior to IBM i 7.5, if you have *R to /home, its contents will be listed, which is usually at least a partial list of user profiles on the system. Now, if you set individuals /home/profile_name directory to DTAAUT(*EXCLUDE) OBJAUT(*NONE), the home/profile_name directory wont be listed using interfaces such as ls in QSH, and the profile names wont be exposed. (Dont forget to set the Object authorities to *NONE; if you dont, the *PUBLIC authority will still have some authority, and it will continue to be listed!) Prior to upgrading to 7.5, you can eliminate this exposure by removing *R authority from /home.
- The Service tool IDs 11111111 and 22222222 are removed, which I think is great because I know of no one who used them and they were consistently left with default passwords.
- In much the same way that you can lock security-related system values from being changed, you can now lock password exit programs. In other words, by using service tools you can determine whether password-related system values can be removed.
- The QRETSVRSEC system value is now obsolete. This makes sense because everyone changed it from the default of 0 to 1 anyway. In fact, many things didnt work if you didnt change it, so getting rid of it makes sense.
- RSTUSRPRF *ALL no longer has to be performed in restricted state.
- The default *PUBLIC authority setting when creating a journal and journal receiver is now *EXCLUDE. Again, a great change. (This should serve as a reminder to check the *PUBLIC authority of QAUDJRN and the attached journal receivers, all of which should be *PUBLIC *EXCLUDE.)
- A new feature of the IBM i procedure SET_SERVER_SBS_ROUTING allows you to route users into specific subsystems when the connection is coming in from a secure (encrypted) databasesuch as ODBC(QZDASSINIT) or file server (QPWFSERVSS) connection. Routing users to specific subsystems isnt new, but prior to this you couldnt route them when these connections were encrypted.
- When you read the Memo to Users (MTU), youll notice a whole bunch of programs, files, job descriptions, and other object types in several IBM-supplied libraries whose *PUBLIC authority has been changed from *ALL or *CHANGE to *USE. I consider this a cleanup rather than a major change. These objects should have been shipping as *USE and somehow slipped through with another authority. Its good to see IBM set these authorities correctly. None of the changes should cause compatibility issues, but youll want to read through the list to make sure.
- Many other changes are occurring in this release. If you are not in the habit of reading the MTU, do not skip this important step, and read it thoroughly before you upgrade! And if youre skipping a release (for example, upgrading from IBM i 7.3 to 7.5), make sure you read the MTU for both releasesthe one youre upgrading to as well as the one youre skipping.
Table Functions That Help Keep Your System Current
One of my absolute favorite table functions that I want to make sure youre aware of is SYSTOOLS.GROUP_PTF_CURRENCY. When run, it does a phone home to IBM to get the latest group PTFs and then performs a comparison to determine whether the system youre running the table function on has the current group PTFs installed or theres a newer group PTF available. Im not sure how you determine this information any other way. Im guessing its available on some IBM Support website, but good luck finding it. Another table function to be aware of, SYSTOOLS.FIRMWARE_CURRENCY, performs a phone home and comparison to determine if your systems firmware is current.
These two simple and easy-to-use functions help you ensure that your system stays current. Use them!
Using the Integrated Security Tools: SECTOOLS
While Ive talked about New Nav and using SQL to get information about IBM i security, I realize that some of you are more comfortable in the green-screen environment or you run in a very strict environment where you can only use a green-screen (yes, those exist!), so I want to make sure youre aware of the CL command-based security tools that come with the operating system. Be aware: They are basic. And what you see is what you get; zero customization is available. But if you want or need something basic, this is it. And these tools come with the operating system.
You access these tools by typing GO SECTOOLS from a command line. The SECTOOLS menu lists numerous utilities and reports that will help you make an assessment of your IBM i security configuration. See Figure 14.1.
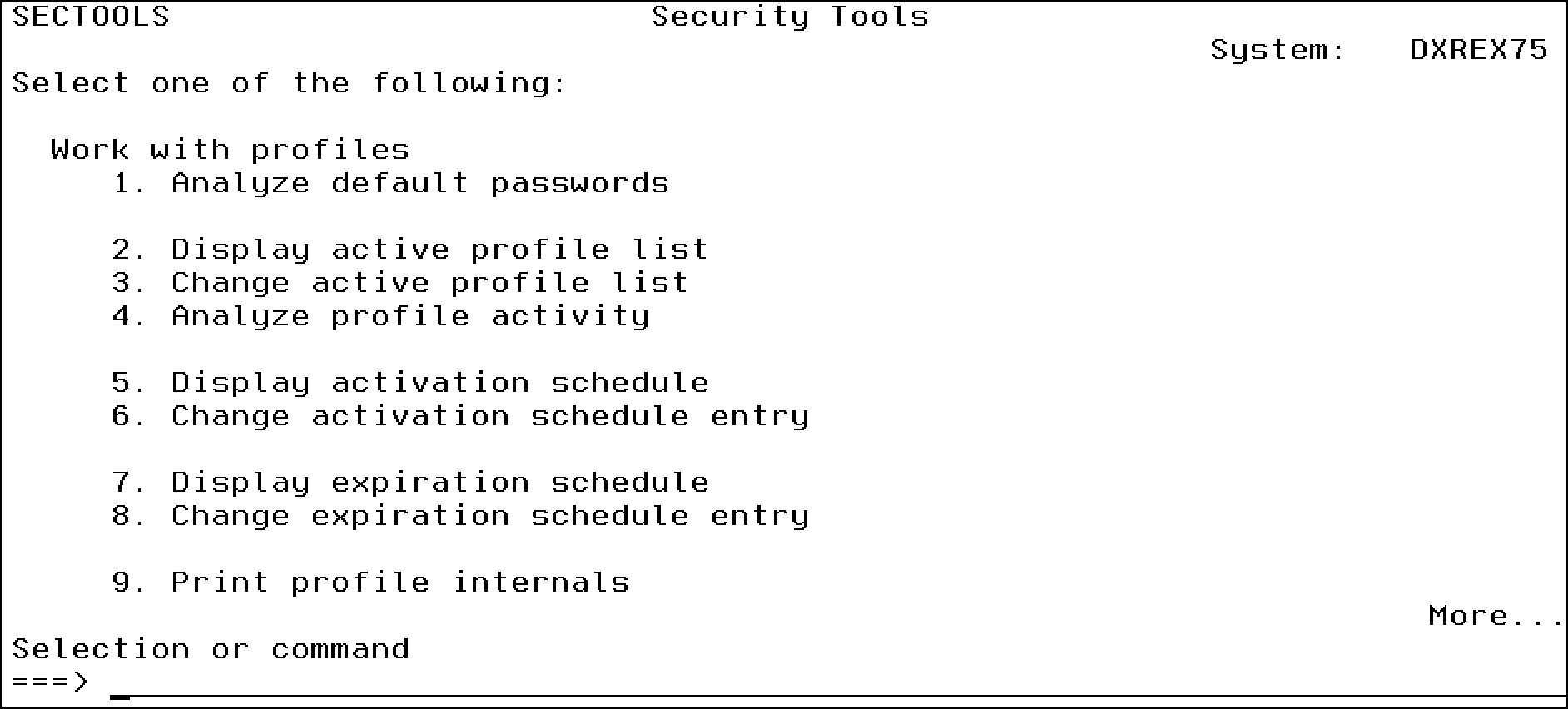
Figure 14.1: Type GO SECTOOLS to get to this menu.
Option 1 is simply the Analyze Default Password (ANZDFTPWD) command, which produces a report listing profiles with a default password (a password that is the same as the user profile name). Im going to skip the rest of the menu options on this page for the moment and scroll down to the second page of the menu. See Figure 14.2.
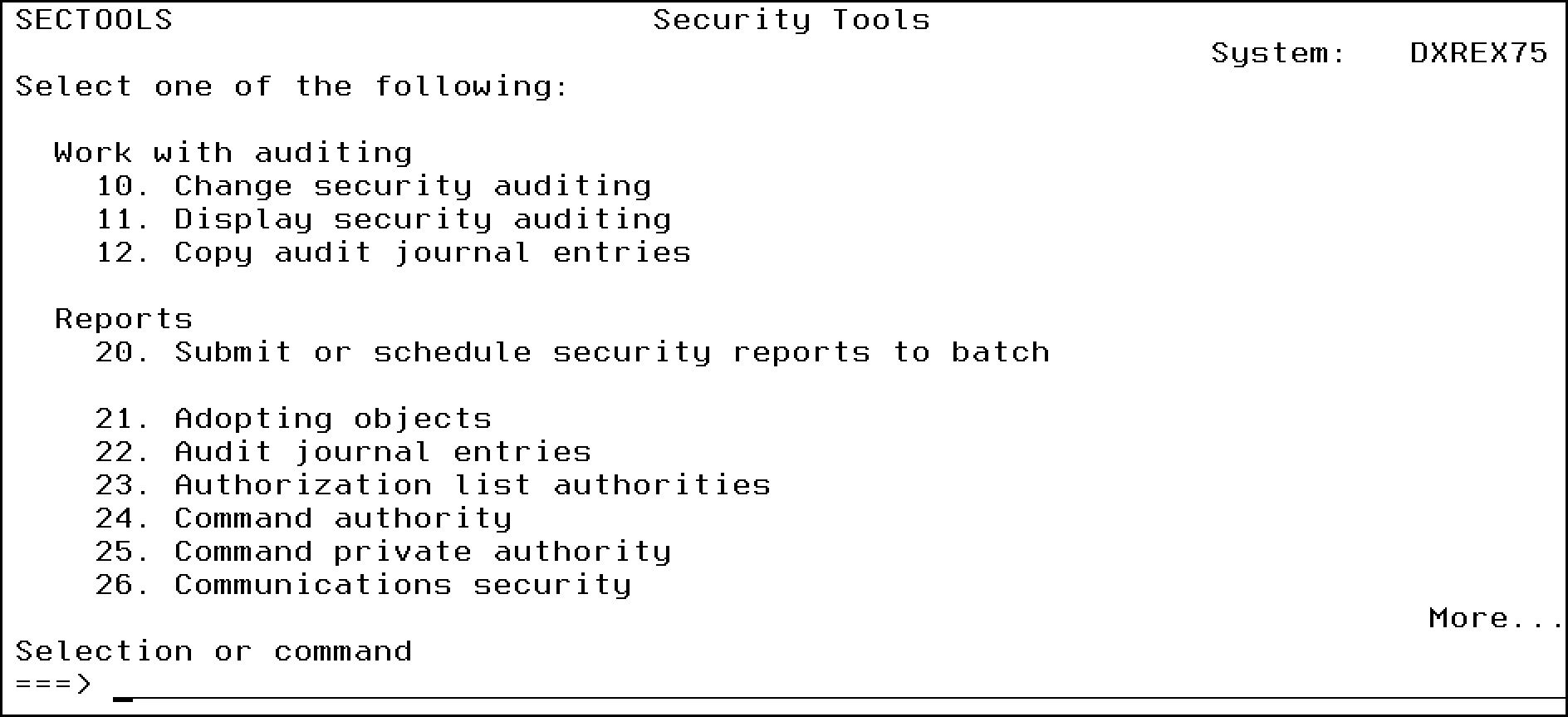
Figure 14.2: Auditing commands and Reports are on the second page of the menu.
Next page












