APPENDIX A

Pageant Use and Implementation
Pageant is an SSH authentication agent that can be used with PuTTY or WinSCP for holding your decrypted keys in memory, so that you dont need to enter your passphrase to decrypt your key every time you are authenticating to a server using a key pair ( discusses key-based authentication in detail). If you are using multiple key pairs to authenticate to multiple servers, Pageant is even more useful. You can use Pageant to hold all your decrypted keys in memory, meaning you need to enter the respective passphrases only once when you start your Windows session. When you log off your Windows session, Pageant exits without saving the decrypted keys on disk, which is the reason you need to enter your passphrase again when you start your Windows session.
Because Pageant is part of PuTTY installation package, you can download it from the same URL ( http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html ). When you run the executable file Pageant.exe to start Pageant, an icon that looks like a computer wearing a hat will appear in your system tray. Right-click the icon to invoke the Pageant menu, and then select the menu option you need: New Session, Saved Sessions, View Keys, Add Key, About, or Exit. If you select View Keys before adding keys, however, you will just see an empty list box.
Using Pageant
To use Pageant, you need first to generate a key pair and copy the public key to the server to which you need to connect. For example, I generated a key pair and saved the keys as keytest.ppk (private key) and keytest.pub (public key). I then encrypted the private key using a passphrase. Because I wanted to connect to the host pract_hdp_sec , I pasted my public key in the authorized_keys file in .ssh directory (as discussed in illustrates selecting and adding the key.
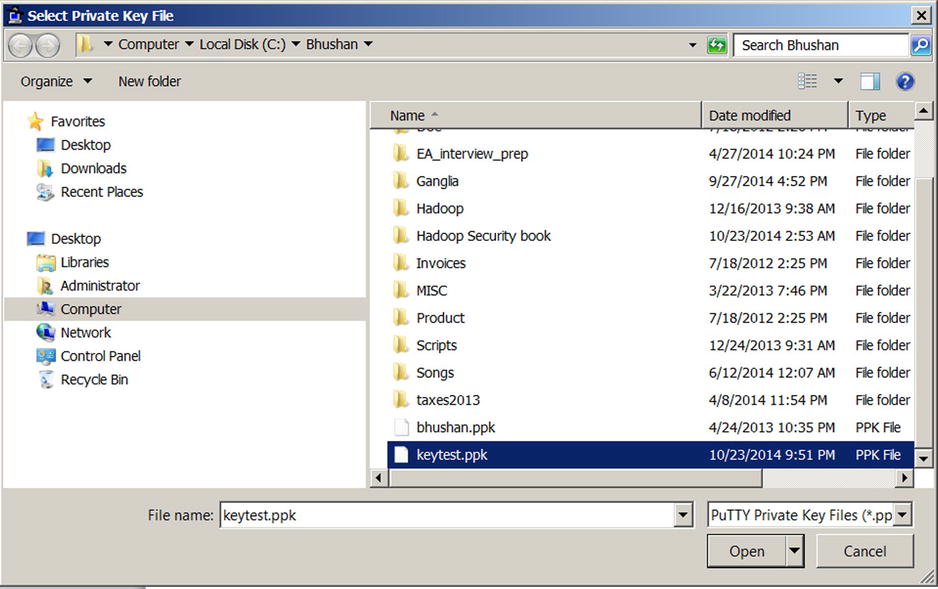
. Adding a key to Pageant
When you select a key (here, testkey.ppk ), you are prompted for the passphrase ().
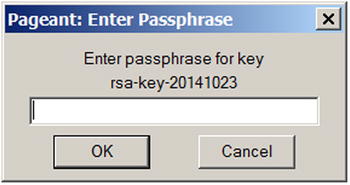
. Using Pageant to store passphrase for a key
After you enter the right passphrase, Pageant decrypts your private key and holds it in memory until you log off your Windows session. You can see your key listed within Pageant, as shown in .
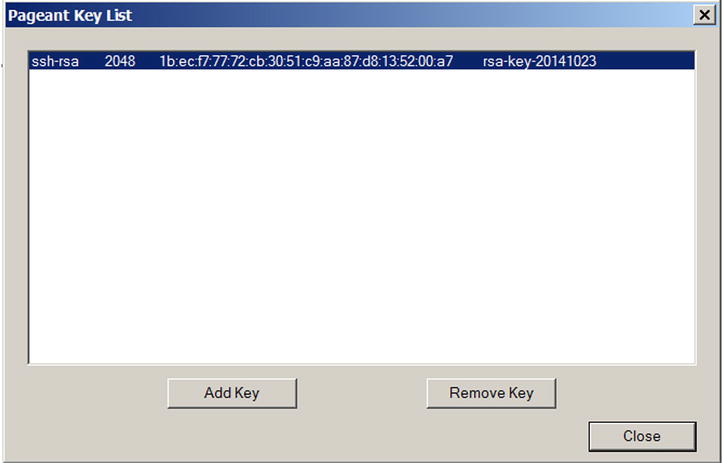
. Listing a stored key within Pageant
Now, you just need to specify your private key as means of authorization within PuTTY ().
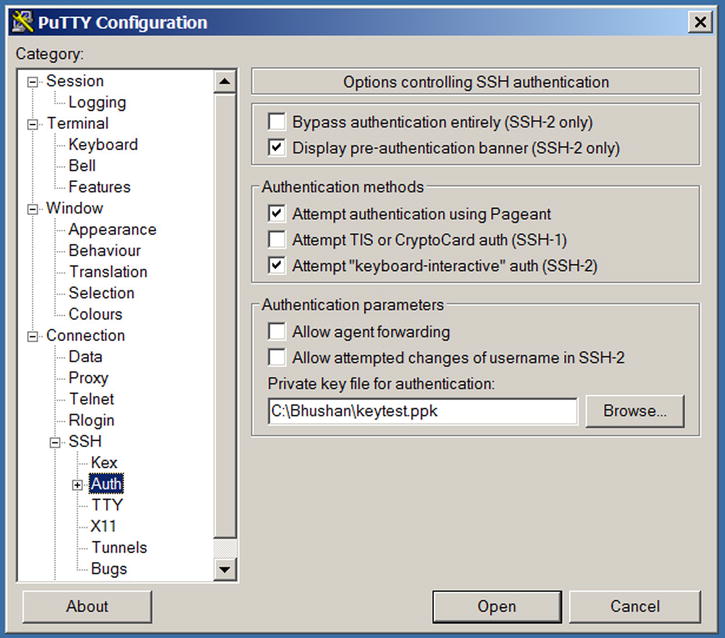
. Specifying key-based authentication within PuTTY
Next time you want to connect to the server pract_hdp_sec , just open a PuTTY session, and it will prompt you for login name. Once you enter the login name, PuTTY directly connects you to the server, as you can see in .
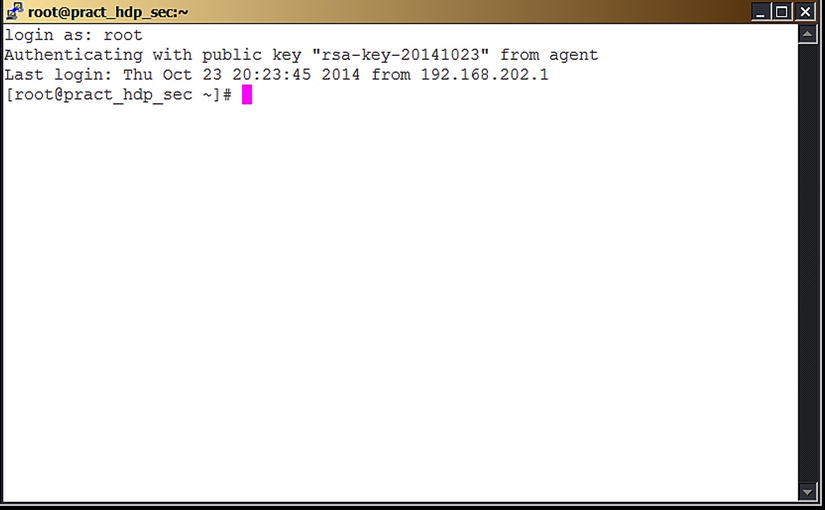
. Key-based authentication performed using decrypted key from Pageant
PuTTY recognizes that Pageant is running, retrieves the decrypted key automatically, and uses it to authenticate. You can open as many PuTTY sessions for the same server as you need without typing your passphrase again.
In addition, Pageant can load multiple private keys automatically when it starts up. For example, suppose you need to connect to ten servers on a daily basis. Manually adding the keys every day to Pageant is difficult as well as error-prone. To automatically load multiple keys, use a Pageant command line similar to the following; the directory path, of course, depends on where your Pageant.exe or your private key file (.ppk file) is located:
C:\Users\Administrator\Desktop>pageant.exe c:\bhushan\keytest.ppk c:\bhushan\bhushan.ppk
You can add multiple keys separated by space. If the keys are encrypted, Pageant will prompt for passphrases at startup. If Pageant is already running and you execute this command, it will load keys into the existing Pageant.
You can also create a shortcut and specify the command line there, as shown in .
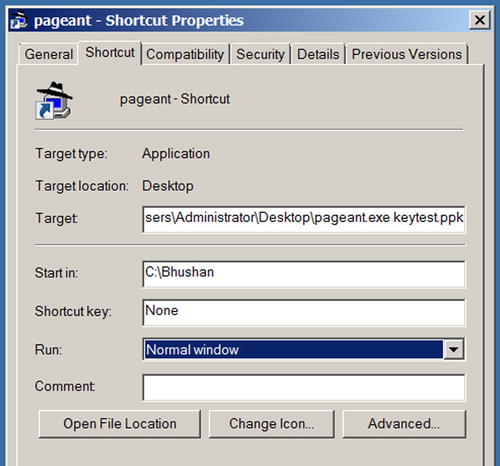
. Specifying a starting (default) directory for multiple keys
If you have just one private key, specify its full path within the Target field:
C:\Users\Administrator\Desktop>pageant.exe c:\bhushan\keytest.ppk
If you have multiple keys and the path is long, instead of specifying path for each key, you can just specify a starting directory. For example, to specify a starting point for my previous multi-key example, in the Target field enter C:\Users\Administrator\Desktop>pageant.exe keytest.ppk and in the Start in field enter C:\Bhushan .
After Pageant initializes and loads the keys specified on its command line, you can direct Pageant to start another program. This program (for e.g. WinSCP or PuTTY etc.) can then use the keys that Pageant loaded. The syntax is as follows:
C:\Users\Administrator\Desktop>pageant.exe c:\bhushan\keytest.ppk -c C:\PuTTY\putty.exe
Security Considerations
Holding your decrypted private keys in Pageant is more secure than storing key files on your local disk drive, but still has some known security issues.
For example, Windows doesnt protect swapped data (memory data written to a system swap file) in any way. So, if you using Pageant for a long time, the decrypted key data could likely be swapped and written to disk. A malicious attacker who gains access to your hard disk could also gain access to your keys. This is, of course, much more secure than storing an unencrypted file on your local disk drive, but still has vulnerabilities.
Windows only has safeguards to prevent excutable code writing into another excutable programs memory space; but still provides Read access to it. In other words, programs can access each others memory space, which is intended as a way to assist in debugging. Unfortunately, malicious programs can exploit this feature and can access Pageants memory to extract the decrypted keys and use them for unlawful purposes.
These risks can easily be mitigated, however, by making sure that your network infrastructure is secure and firewalls in place.
APPENDIX B

PuTTY and SSH Implementation for Linux-Based Clients
In the section Key-Based Authentication Using PuTTY in , you reviewed how PuTTY can effectively be used for key-based authentication for a Windows-based client. What about key-based authentication for Linux-based clients? The answer is PuTTY again.
You can download the Linux-based version of PuTTY from various sources. I used rpm (Red Hat Package Manager, a package management system used for software distribution in Linux domain) for the latest PuTTY version (0.63) for CentOS 6.2; the file is putty-0.63-1.el6.rf.x86_64.rpm . You can download the rpm from various sources; you just need to search for your operating system. After you download the file, install the rpm:
rpm -Uvh putty-0.63-1.el6.rf.x86_64.rpm
Next page




![Echeverria Joey - Hadoop security: [protecting your big data platform]](/uploads/posts/book/172570/thumbs/echeverria-joey-hadoop-security-protecting-your.jpg)












