Using Digital Forensics and Investigative Techniques to Identify Cybercrime Suspects
Copyright
Syngress is an imprint of Elsevier
The Boulevard, Langford Lane, Kidlington, Oxford, OX5 1GB, UK
225 Wyman Street, Waltham, MA 02451, USA
First published 2013
Copyright 2013 Elsevier Inc. All rights reserved.
The material in this book is excerpted from Placing the Suspect Behind the Keyboard: Using Digital Forensics and Investigative Techniques to Identify Cybercrime Suspects.
No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or any information storage and retrieval system, without permission in writing from the publisher. Details on how to seek permission, further information about the Publishers permissions policies and our arrangement with organizations such as the Copyright Clearance Center and the Copyright Licensing Agency, can be found at our website: www.elsevier.com/permissions
This book and the individual contributions contained in it are protected under copyright by the Publisher (other than as may be noted herein).
Notices
Knowledge and best practice in this field are constantly changing. As new research and experience broaden our understanding, changes in research methods, professional practices, or medical treatment may become necessary.
Practitioners and researchers must always rely on their own experience and knowledge in evaluating and using any information, methods, compounds, or experiments described herein. In using such information or methods they should be mindful of their own safety and the safety of others, including parties for whom they have a professional responsibility.
To the fullest extent of the law, neither the Publisher nor the authors, contributors, or editors, assume any liability for any injury and/or damage to persons or property as a matter of products liability, negligence or otherwise, or from any use or operation of any methods, products, instructions, or ideas contained in the material herein.
Trademarks/Registered Trademarks: Brand names mentioned in this book are protected by their respective trademarks and are acknowledged.
British Library Cataloguing in Publication Data
A catalogue record for this book is available from the British Library
Library of Congress Cataloging-in-Publication Data
A catalog record for this book is available from the Library of Congress
ISBN: 978-0-12-409504-5
For information on all Syngress publications visit our website at store.elsevier.com
This book has been manufactured using Print On Demand technology. Each copy is produced to order and is limited to black ink. The online version of this book will show color figures where appropriate.

Chapter 1
Case Presentation
Introduction
Its Not Whether You Win or Lose
Investigative Mindset
Your Audience
Preparation
Organizing Case Information
Value of Visuals
Presentation Media
Slideshows and Animations
Charts and Diagrams
The Suspects Machine
Analogies
Avoid Too Much Information
Your Presentation
Summary
Bibliography
This chapter will discuss methods of presenting electronic evidence for a variety of audiences. The admissibility, authentication, chain of custody, and other aspects of what is evidence are extremely important to every case; however, this chapter will only minimally discuss the actual evidence and focus more on methods of presenting your case. After all, the objective of any investigation is to convey to an audience the facts of the case in a manner that they understand it.
Articulating your case in a manner in which your audience creates a picture in their mind will also have your audience place the suspect behind the keyboard. This can be accomplished without you having to say it directly as the audience will say it for you.
hearings. Why did you suspect this person and not that person? Did you focus your entire investigation on one person? These types of questions are intended to discover your mindset and to find out what you were thinking. The investigative mindset not only helps you to be a great examiner or investigator but it also helps you to prepare your case for presentation by being able to articulate your thought processes.
, is dtSearch, an indexing application typically used as a forensic tool but also excels at indexing your case information to be searched on the fly.
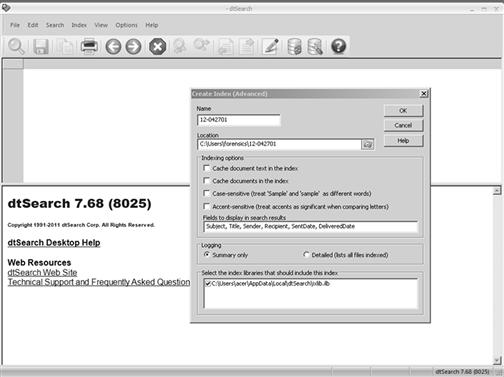
Fig. 1.1 dtSearch indexing application: http://www.dtsearch.com.
Complex cases that contain hundreds of thousands of electronic files are better served being indexed, that is, a database of words and numbers of the files created for ease of searching. dtSearch not only indexes large datasets but it can also create reports of the searches, export the files found, and even highlight the key words found. A utility such as dtSearch enables you to find information quickly that might have been easily be overlooked when manually searching files on a hard drive. Being asked a question on the spot by your boss, client, or judge for whom you dont have answer is stressful enough, but not being able to find the answer makes it that much worse.
1.7 Value of Visuals
The clich that a picture is worth a thousand words does not accurately describe a visual used in your presentation. In a case presentation, one visual can be worth the entire case. As most people grow up learning visually, whether in math class using charts and graphs to see numbers or through art, understanding by seeing is an effective method of learning.
In the tale of three blind men attempting to describe an elephant with words, each basing their description on the part of the elephant each person touched, such as the tusk or the tail, they could not agree on the totality of the elephants description. Presentations require the spoken word for descriptions, but visuals can make sure that each person in your audience understands and sees the same thing.
Compare the following examples. shows a paragraph describing an average evidence scene with multiple evidence items.

Fig. 1.2 Written description of an evidence scene with multiple items.
The accompanying figure to the written description is seen in , the photo clarifies the scene in the mind of your audience without misunderstanding.