Part I
Anatomy of Payment Application Vulnerabilities
Science in the service of humanity is technology, but lack of wisdom may make the service harmful.
Isaac Asimov
Chapter 1
Processing Payment Transactions
Because people have no thoughts to deal in, they deal cards, and try and win one another's money. Idiots!
Arthur Schopenhauer
In order to understand the vulnerability points of point-of-sale and payment applications, it is necessary to know the basicshow, when, and why sensitive cardholder data moves between different peers during the payment transaction cycle:
- Why (the reason): Is it really necessary to hold, store, and transmit this data throughout the entire process?
- How (the location and the routes): What are the areas with a concentration of sensitive records?
- When (the timing): How long is this information available in those areas?
Payment Cards
The use of payment cards is obviously one of the main subjects of this book. There are several main types of payment cards commonly used for payments:
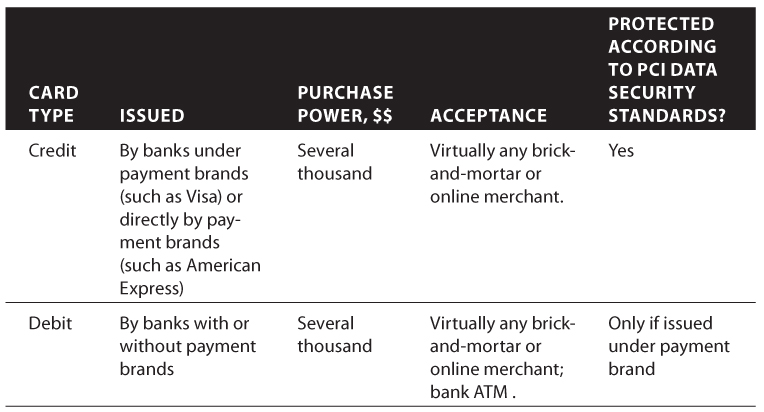
The credit card was the first payment card and it is still very common. By paying with a credit card, customers use their available credit and pay the bill afterwards. Credit cards are not usually protected by a Personal Identification Number (PIN), which allows them to be used for online purchases.
The debit (ATM, Cash) card is a relatively new method of payment. It is different from a credit card because the debit cardholder pays with the money available in their bank account, which is debited immediately in real time. A debit card seems to be more dangerous compared to a credit card because the debit card is directly linked to the bank checking account and usually allows ATM cash withdrawals. On the other hand, it is more protected by the required two-factor authentication (PIN number plus card itself). The real dangerous element of many branded debit cards is that they can be processed as credit cards, without entering the PIN.
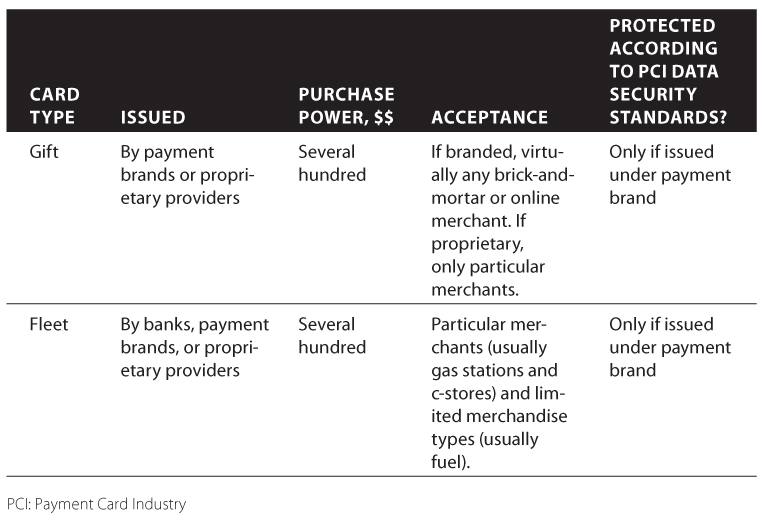
The gift card is similar to a debit card but usually does not have the protection provided by a PIN. The gift card is not linked to a bank account and normally contains fixed amounts of funds. The card itself does not hold any financial informationthe point-of-sale (POS) terminal communicates with the gift card provider during payment transactions in order to get authorization. Gift cards are less dangerous than credit and debit cards because only fixed, often very limited, amounts of money can be stolen.
The fleet (or proprietary) card is similar to a credit card but can be used only at particular locations (usually gas stations and convenience stores) and for purchasing only limited types of merchandise (such as fuel and other automobile items). Fleet cards, even though often issued by major card brands, are less interesting to bad guys because they cannot be used for ATM withdrawal, online shopping, or purchases in department or grocery stores.
shows a list of major payment card types and their main features.
Payment Card Types
Card Entry Methods
There are two main methods used to enter the card data into the POS in order to start a payment transaction: swipe and manual entry.
MSR
The first method uses a Magnetic Stripe Reader, or MSR, which is a device that reads the magnetic stripe on payment cards. Modern MSR devices have encryption capabilities and can be used in point-to-point encryption (P2PE) solutions (see Chapter 8 for more details). The easiest way to enter the card data into the POS is to just swipe the card in the MSR so it can read the magnetic stripe and automatically enter all the necessary information. However, if the magnetic stripe is damaged, the customer or cashier can manually enter the account number and expiration date embossed on the front of the card.
Some MSR devices emulate keyboard input, so swiping the card is equivalent to simply typing numbers and letters on the computer keyboard. Stealing the track data in this case is as simple as sniffing the MSR input by installing a keystroke logger.
Pinpad
The second method uses a pinpad. A pinpad, or Point of Interaction (POI) with a built-in MSR, is a more sophisticated device because it has firmware which can be customized for various functions including protection of the card's sensitive data. Most pinpads also have hardware encryption capabilities implemented as TRSM (Tamper-Resistant Security Module). In addition to MSR, POI also includes other peripherals, such as a customer display and keyboard (in addition to the pinpad), for better direct interaction with the customer throughout the payment process.
Key Players
According to Visa, there are five key players in the card payment processing game: Consumers, Merchants, Acquirers, Issuers, and Card Brands. However, in practice, there are usually more participants. In addition to Consumers, Merchants, Acquirers, Issuers, and Card Brands, there are also Gateways, Processors, Software Vendors, and Hardware Manufacturers who facilitate the payment transaction processing.
Before diving into the details of these players, I would like to remind you that the scope of this book is security of POS and associated payment applications which are located in brick-and-mortar stores. Despite the fact that merchants account for a relatively small percentage of the overall payment processing life cycle, their portion of responsibility and risk is incomparably larger than anyone else's share. There are several reasons for this:
First, merchants have a very distributed structure compared to othersa typical retail chain may consist of dozens to thousands of stores. Compare this to a processor who may have a few enterprise-scale data centers where it is much easier to organize the security measures.
Second, retail stores are public places with all the ensuing consequences for security.
Third, most merchants rely on hardware and software vendors as their technology providers (including security) and simply are not ready to accept the fact that they have a technology which is vulnerable by design. When the PC and Internet revolution in the late 1990s started replacing the old cash registers and standalone credit terminals with complex POS systems with integrated payment applications, it also began bringing countless system and network security flaws and eventually made them an inescapable day-to-day nightmare reality for millions of retailers around the world.
Consumer (Cardholder)
It's us. We go to stores, swipe the cards, and pay the bills.
Ideally, consumers are not supposed to care about security beyond keeping their PIN a secret. If the card is lost or stolen, the consumer just wants to call the bank and get a new one. When our card is swiped, our private information is shared with the merchant, whose POS system is supposed to protect our information throughout the process. We rely on modern high-end technologies to protect our plastic money.
Next page