Troy McMillan - CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide, 2ed Edition
Here you can read online Troy McMillan - CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide, 2ed Edition full text of the book (entire story) in english for free. Download pdf and epub, get meaning, cover and reviews about this ebook. year: 2020, publisher: Pearson, genre: Politics. Description of the work, (preface) as well as reviews are available. Best literature library LitArk.com created for fans of good reading and offers a wide selection of genres:
Romance novel
Science fiction
Adventure
Detective
Science
History
Home and family
Prose
Art
Politics
Computer
Non-fiction
Religion
Business
Children
Humor
Choose a favorite category and find really read worthwhile books. Enjoy immersion in the world of imagination, feel the emotions of the characters or learn something new for yourself, make an fascinating discovery.

- Book:CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide, 2ed Edition
- Author:
- Publisher:Pearson
- Genre:
- Year:2020
- Rating:3 / 5
- Favourites:Add to favourites
- Your mark:
- 60
- 1
- 2
- 3
- 4
- 5
CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide, 2ed Edition: summary, description and annotation
We offer to read an annotation, description, summary or preface (depends on what the author of the book "CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide, 2ed Edition" wrote himself). If you haven't found the necessary information about the book — write in the comments, we will try to find it.
CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide, 2ed Edition — read online for free the complete book (whole text) full work
Below is the text of the book, divided by pages. System saving the place of the last page read, allows you to conveniently read the book "CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide, 2ed Edition" online for free, without having to search again every time where you left off. Put a bookmark, and you can go to the page where you finished reading at any time.
Font size:
Interval:
Bookmark:

Troy McMillan
()

This chapter covers the following topics related to Objective 1.1 (Explain the importance of threat data and intelligence) of the CompTIA Cybersecurity Analyst (CySA+) CS0-002 certification exam:
: Examines open-source intelligence, proprietary/closed-source intelligence, timeliness, relevancy, and accuracy
: Covers the importance of identifying levels of confidence in data
: Introduces Structured Threat Information eXpression (STIX), Trusted Automated eXchange of Indicator Information (TAXII), and OpenIOC
: Investigates known threats vs. unknown threats, zero-day threats, and advanced persistent threats
: Identifies actors such as nation-state, hacktivist, organized crime, and intentional and unintentional insider threats
: Explains the requirements, collection, analysis, dissemination, and feedback stages
: Describes the types of malware that commonly infect networks
: Discusses data sharing among members of healthcare, financial, aviation, government, and critical infrastructure communities
When a war is fought, the gathering and processing of intelligence information is critical to the success of a campaign. Likewise, when conducting the daily war that comprises the defense of an enterprises security, threat intelligence can be the difference between success and failure. This opening chapter discusses the types of threat intelligence, the sources and characteristics of such data, and common threat classification systems. This chapter also discusses the threat cycle, common malware, and systems of information sharing among enterprises.
The Do I Know This Already? quiz enables you to assess whether you should read the entire chapter. If you miss no more than one of these seven self-assessment questions, you might want to skip ahead to the Exam Preparation Tasks section. lists the major headings in this chapter and the Do I Know This Already? quiz questions covering the material in those headings so that you can assess your knowledge of these specific areas. The answers to the Do I Know This Already? quiz appear in Appendix A.
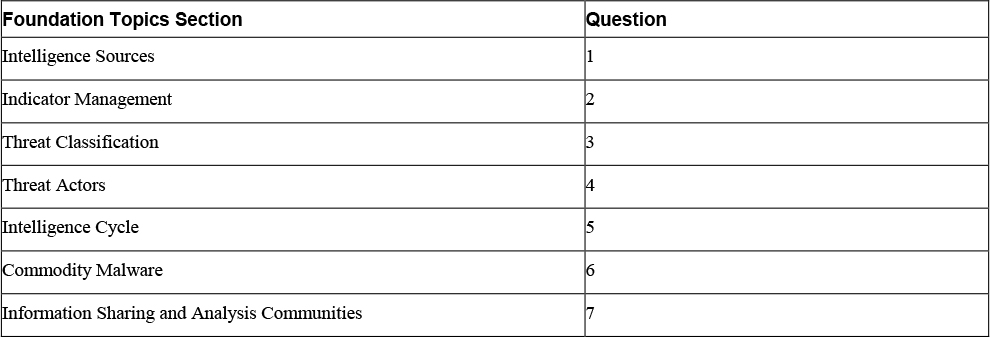
Table 1-1 Do I Know This Already? Foundation Topics Section-to-Question Mapping
Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as wrong for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
Which of the following is an example of closed-source intelligence?
a. Internet blogs and discussion groups
b. Print and online media
c. Unclassified government data
d. Platforms maintained by private organizations
Which of the following is an application protocol for exchanging cyber threat information over HTTPS?
a. TAXII
b. STIX
c. OpenIOC
d. OSINT
Which of the following are threats discovered in live environments that have no current fix or patch?
a. Known threats
b. Zero-day threats
c. Unknown threats
d. Advanced persistent threats
Which of the following threat actors uses attacks as a means to get their message out and affect the businesses that they feel are detrimental to their cause?
a. Organized crime
b. Terrorist group
c. Hacktivist
d. Insider threat
In which stage of the intelligence cycle does most of the hard work occur?
a. Requirements
b. Collection
c. Dissemination
d. Analysis
Malware that is widely available for either purchase or by free download is called what?
a. Advanced
b. Commodity
c. Bulk
d. Proprietary
Which of the following information sharing and analysis communities is driven by the requirements of HIPAA?
a. H-ISAC
b. Financial Services Information Sharing and Analysis Center
c. Aviation Government Coordinating Council
d. ENISA
Threat intelligence comes in many forms and can be obtained from a number of different sources. When gathering this critical data, the security professional should always classify the information with respect to its timeliness and relevancy. Lets look at some types of threat intelligence and the process of attaching a confidence level to the data.

(OSINT) consists of information that is publicly available to everyone, though not everyone knows that it is available. OSINT comes from public search engines, social media sites, newspapers, magazine articles, or any source that does not limit access to that information. Examples of these sources include the following:
Print and online media
Internet blogs and discussion groups
Unclassified government data
Academic and professional publications
Industry group data
Papers and reports that are unpublished (gray data)

sources are those that are not publicly available and usually require a fee to access. Examples of these sources are platforms maintained by private organizations that supply constantly updating intelligence information. In many cases this data is developed from all of the providers customers and other sources.
An example of such a platform is offered by CYFIRMA, a market leader in predictive cyber threat visibility and intelligence. CYFIRMA announced the launch of cloud-based Cyber Intelligence Analytics Platform (CAP) v2.0. In 2019, using its proprietary artificial intelligence and machine learning algorithms, CYFIRMA helping organizations unravel cyber risks and threats and enable proactive cyber posture management.
One of the considerations when analyzing intelligence data (of any kind, not just cyber data) is the of such data. Obviously, if an organization receives threat data that is two weeks old, quite likely it is too late to avoid that threat. One of the attractions of closed-source intelligence is that these platforms typically provide near real-time alerts concerning such threats.
Font size:
Interval:
Bookmark:
Similar books «CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide, 2ed Edition»
Look at similar books to CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide, 2ed Edition. We have selected literature similar in name and meaning in the hope of providing readers with more options to find new, interesting, not yet read works.
Discussion, reviews of the book CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide, 2ed Edition and just readers' own opinions. Leave your comments, write what you think about the work, its meaning or the main characters. Specify what exactly you liked and what you didn't like, and why you think so.




