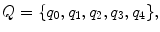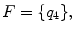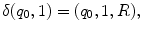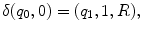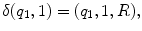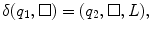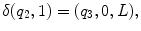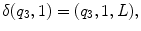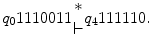Yan - Quantum Attacks on Public-Key Cryptosystems
Here you can read online Yan - Quantum Attacks on Public-Key Cryptosystems full text of the book (entire story) in english for free. Download pdf and epub, get meaning, cover and reviews about this ebook. City: Boston;MA;New York;NY u.a, year: 2013, publisher: Springer US, genre: Children. Description of the work, (preface) as well as reviews are available. Best literature library LitArk.com created for fans of good reading and offers a wide selection of genres:
Romance novel
Science fiction
Adventure
Detective
Science
History
Home and family
Prose
Art
Politics
Computer
Non-fiction
Religion
Business
Children
Humor
Choose a favorite category and find really read worthwhile books. Enjoy immersion in the world of imagination, feel the emotions of the characters or learn something new for yourself, make an fascinating discovery.
Quantum Attacks on Public-Key Cryptosystems: summary, description and annotation
We offer to read an annotation, description, summary or preface (depends on what the author of the book "Quantum Attacks on Public-Key Cryptosystems" wrote himself). If you haven't found the necessary information about the book — write in the comments, we will try to find it.
Yan: author's other books
Who wrote Quantum Attacks on Public-Key Cryptosystems? Find out the surname, the name of the author of the book and a list of all author's works by series.














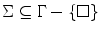 .
.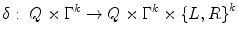
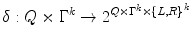
 is a special symbol called the blank .
is a special symbol called the blank .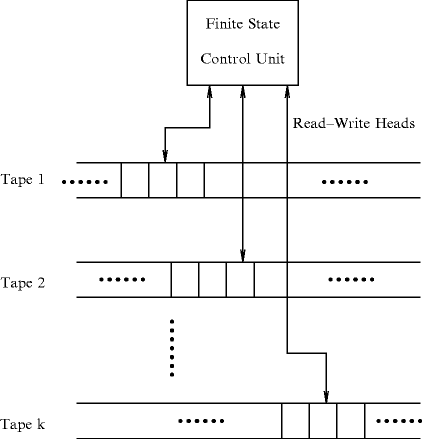
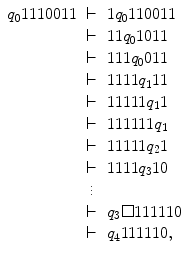
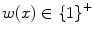 , such that| w ( x )|= x . Thus in this notation, 4 will be represented by 1111. We must also decide how x and y are placed on the tape initially and how their sum is to appear at the end of the computation. It is assumed that w ( x ) and w ( y ) are on the tape in unary notation, separated by a single 0, with the readwrite head on the leftmost symbol of w ( x ). After the computation, w ( x + y ) will be on the tape followed by a single 0, and the readwrite head will be positioned at the left end of the result. We therefore want to design a Turing machine for performing the computation
, such that| w ( x )|= x . Thus in this notation, 4 will be represented by 1111. We must also decide how x and y are placed on the tape initially and how their sum is to appear at the end of the computation. It is assumed that w ( x ) and w ( y ) are on the tape in unary notation, separated by a single 0, with the readwrite head on the leftmost symbol of w ( x ). After the computation, w ( x + y ) will be on the tape followed by a single 0, and the readwrite head will be positioned at the left end of the result. We therefore want to design a Turing machine for performing the computation 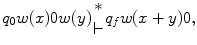
 indicates an unspecified number of steps as follows:
indicates an unspecified number of steps as follows: