David Zhang and Guangming Lu 3D Biometrics 2013 Systems and Applications 10.1007/978-1-4614-7400-5 Springer Science+Business Media New York 2013
David Zhang and Guangming Lu 3D Biometrics 2013 Systems and Applications 10.1007/978-1-4614-7400-5_1 Springer Science+Business Media New York 2013
1. Overview
Abstract
Recently, biometrics technology is one of the hot research topics in the IT field because of the demands for accurate personal identification or verification to solve security problems in various applications. This chapter gives an all-around introduction to biometrics technologies, and the new trend: 3D biometrics.
1.1 The Need for Biometrics
Biometrics lies in the heart of todays society. There has been an ever-growing need to automatically authenticate individuals at various occasions in our modern and automated society, such as information confidentiality, homeland security, and computer security. Traditional knowledge based or token based personal identification or verification is so unreliable, inconvenient, and inefficient, which is incapable to meet such a fast-pacing society. Knowledge-based approaches use something that you know to make a personal identification, such as password and personal identity number. Token-based approaches use something that you have to make a personal identification, such as passport or ID card. Since those approaches are not based on any inherent attributes of an individual to make the identification, it is unable to differentiate between an authorized person and an impostor who fraudulently acquires the token or knowledge of the authorized person. This is why biometrics identification or verification system started to be more focused in the recent years.
Biometrics involves identifying an individual based on his/her physiological or behavioral characteristics. Many parts of our body and various behaviors are embedded such information for personal identification. In fact, using biometrics for person authentication is not new, which has been implemented over 1,000 years, numerous research efforts have been put on this subject resulting in developing various techniques related to signal acquisition, feature extraction, matching and classification. Most importantly, various biometrics systems including, fingerprint, iris, hand geometry, voice and face recognition systems have been deployed for various applications (Jain et al. ).
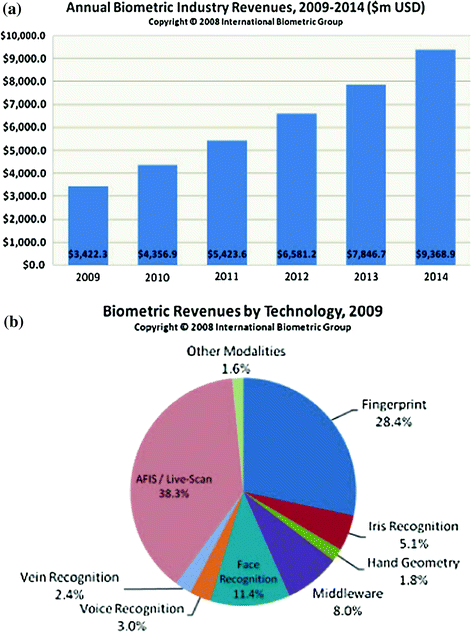
According to the annual report of the International Biometric Group (IBG, New York), the market for biometrics technologies increased around 25 % each year in the past 3 years. Figure b shows Comparative Market Share by different biometrics technologies for the year 2009.
Fig. 1.1
a Total biometrics revenues prediction in 20092014. b Comparative market sharing by biometrics technologies in 2009 (International Biometric Group )
1.1.1 Biometrics System Architecture
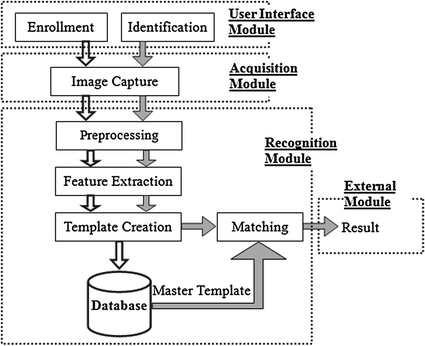
A biometrics system has four major components: User Interface Module, Acquisition Module, Recognition Module and External Module. Figure shows the breakdown of each module of the biometrics authentication system. The functions of each component are listed below:
Fig. 1.2
The modules in biometrics system
User Interface Module provides an interface between the system and users for the smooth authentication operation. It is crucial to develop a good user interface such that users are happy to use the device.
Acquisition Module is the channel for the biometrics traits to be acquired for the further processing.
Recognition Module is the key part of our system, which will determine whether a user is authenticated. It consists of image pre-processing, feature extraction, template creation, database updating, and matching. Then it gives an identification/verification result.
External Module receives the signal come from the recognition module, to allow some operations to be performed, or denied the operations requested. This module actually is an interfacing component, which may be connected to another hardware components or software components.
1.1.2 Operation Mode of a Biometrics System
A biometrics system is usually operated in three modes: enrollment, identification and verification. But some systems only have either identification or verification modes.
EnrollmentBefore a user can be verified or identified by the system, he/she must be enrolled by the biometrics system. The users biometrics data is captured, preprocessed and feature extracted as shown in stages 13 of Fig.. Then, the users template is stored in a database or file system.
IdentificationThis refers to the identification of a user based solely on his/her biometrics information, without any prior knowledge about the identity of a user. Sometimes it is referred to 1-to-many matching, or recognition. It will go through stages 13 to create an identification template. Then the system will retrieve all the templates from the database for the feature matching. A result of success or failure is given finally. Generally, accuracy decreases as the size of the database grows.
VerificationThis requires that an identity (ID card, smart card or ID number) is claimed, and then a matching of the verification template with master templates is performed to verify the persons identity claim. Sometimes verification is referred to a 1-to-1 matching, or authentication.
1.1.3 Evaluation of Biometrics and Biometrics System
Seven factors affect the determination of a biometrics identifier, including: universality, uniqueness, permanence, collectability, performance, acceptability, and circumvention. Table ).
Table 1.1
Perception of five common biometrics technologies by three biometrics experts (Jain et al. )
| Face | Fingerprint | Hand geometry | Iris | Palm print |
|---|
Universality | High | Medium | Medium | High | Medium |
Uniqueness | Low | High | Medium | High | High |
Permanence | Medium | High | Medium | High | High |
Collectability | High | Medium | High | Medium | Medium |
Performance | Low | High | Medium |