1.1 Introduction
In todays security conscious society, automatic personal authentication is important in different applications including government, commercial, educational institutions, industries, public places, etc. Questions such as Is this the person who he claims to be?, Should this individual be authorized to perform this transaction?, Does this employee have authorization to access this service? etc., are asked millions of time every day by thousands of organizations in both private and public sectors [].
Existing systems use either identity cards or passwords for personal authentication (Fig. a). These security systems no longer suffice for individual authentication because cards can be stolen or forged and a password can be forgotten or cracked. The following are some interesting statistics:
According to a report by Nilson, $11.27 billion losses due to credit card and debit card fraud during 2012 [].
According to American Bankers Associations Deposit Account Fraud Survey-2011, Financial institutions incurred $955 million in losses due to debit card fraud in 2010, which is around a 21% increase from the $788 million in losses incurred during 2008 [].
According to the Gartner Group, between 20 to 50% of all help desk calls are for password resets and the average help desk labor cost for a single password reset is about $70 [].
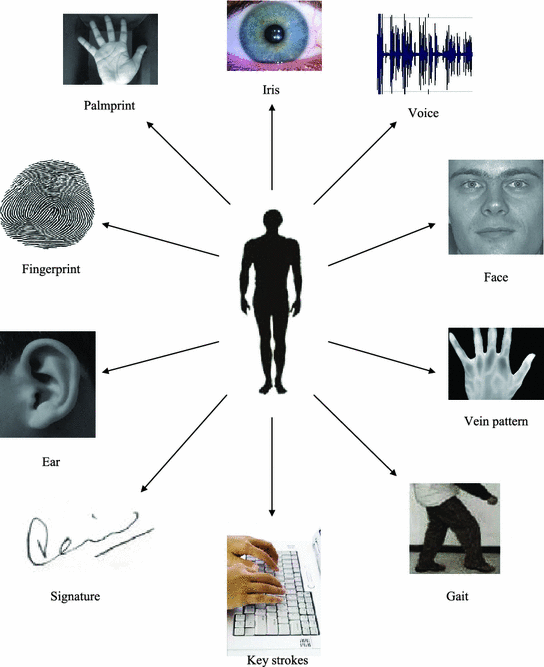
The above statistics shows the need of an accurate and efficient approach for personal recognition. Biometric recognition that uses humans fingerprint and/or palmprint and/or iris, etc., is a better choice and a reliable solution for convenient human recognition (Fig. ], recognition in these large biometric systems is a challenging problem. In this book, we explore methods that are capable of searching biometric databases in real time with a high level of confidence.
Fig. 1.1
Personal authentication techniques: a Traditional methods such as identity cards, Passwords, etc., b Biometric characteristics []
1.2 Biometric Recognition
A biometric system is a pattern recognition system that recognizes individuals based on the measurement of their physiological and/or behavioral traits: Physiological traits include a persons fingerprint, facial features, palmprint, vein pattern, or ocular characteristics; Behavioral traits include voice, gait, keystrokes, signature etc. [ shows a few of the biometric traits (including physiological and behavioral) for personal recognition.
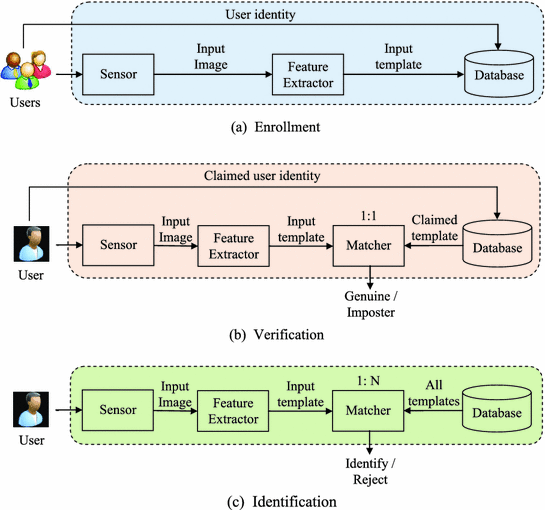
A generic biometric system is shown in Fig.. It consists of two modules: enrollment and recognition.
Enrollment
This module enrolls the individuals into the biometric system (Fig. a). During enrollment, a sensor captures the biometric characteristic of an individual, from which a set of features (template) are extracted by a feature extractor. Depending on the application context, the extracted feature template may be stored in a central database along with the individuals identity (name, ID number, etc.) or be recorded on a smart card issued to the individual.
Recognition
This module recognizes the identity of an individual at the point of service. During this phase, the sensor acquires the biometric characteristic of the individual to be recognized. The captured biometric image is preprocessed by the feature extractor to generate the template. The extracted template is compared to the prestored template(s) using a matcher to establish the identity. The process of user recognition in biometric systems is shown in Fig. b, c. A biometric recognition system is designed to work in one of the two different modes: (i) verification or (ii) identification.
Fig. 1.2
Different biometric traits for personal recognition
1.2.1 Verification
In verification mode, the user will claim his identity by using a user name, or a personal identification number, or a smart card, etc., along with the biometric data. The system will then verify the user by matching the acquired biometric characteristic with his own biometric sample prestored in the system. The system in this mode, conducts a one-to-one matching to determine whether the identity claimed by the individual is true or not [b.
1.2.2 Identification
In this mode, the user does not claim any identity. The user provides his biometric data, and the data is compared to the stored template of every individual in the system database. The system in this mode, conducts a one-to-many comparison to find the identity of an individual. In this case, the question To whom does the submitted biometric data belong? is answered. For example, if a fingerprint impression is found at a crime scene, to determine the suspect it is compared to all the enrolled fingerprints in the database. If a match is found, the identity of the suspect is determined. The process of recognizing a user in identification mode can be seen in Fig. c.
Fig. 1.3
Different modes of operation of a generic biometric system []
1.3 Indexing
In todays security conscious society, biometric recognition systems became more popular and deployed in variety of applications such as surveillance, border control, network access, banking, employee authentication, etc. The market for biometric applications is growing worldwide, and specifically in emerging economies, such as India, where scalability is a huge challenge. According to a market research report by Acuity Market Intelligence (AMI) [.
Note that, most of these biometric systems deal with large-scale databases and their size is increasing at a rapid pace. For instance, Indias national ID program []. Currently, it has records of over 51 million criminals and over 1.5 million noncriminals.