SIP
Understanding the Session Initiation Protocol
Fourth Edition
For a complete listing of titles in the Artech House Telecommunications Library, turn to the back of this book.
SIP
Understanding the Session Initiation Protocol
Fourth Edition
Alan B. Johnston

Library of Congress Cataloging-in-Publication Data
A catalog record for this book is available from the U.S. Library of Congress.
British Library Cataloguing in Publication Data
A catalogue record for this book is available from the British Library.
Cover design by John Gomes
ISBN 13: 978-1-60807-863-9
2016 ARTECH HOUSE
685 Canton Street
Norwood, MA 02062
All rights reserved. Printed and bound in the United States of America. No part of this book may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage and retrieval system, without permission in writing from the publisher.
All terms mentioned in this book that are known to be trademarks or service marks have been appropriately capitalized. Artech House cannot attest to the accuracy of this information. Use of a term in this book should not be regarded as affecting the validity of any trademark or service mark.
10 9 8 7 6 5 4 3 2 1
Contents
Preface to the Fourth Edition
This fourth edition of the book, much like the SIP protocol itself, is a refinement, rather than a wholesale revolution. There are updates and additions throughout the book, but the major changes are new chapters on security and a new chapter on WebRTC, a related technology that didnt even exist when the third edition was published. Large parts of the security sections are based on material originally written for my book, Understanding VoIP Security, so thanks to Dave Piscitello for collaborating with me on that project.
I would like to take this opportunity to thank additional key people who have contributed to my writing, teaching, and researching career related to SIP.
To my colleagues at MCI, thanks for getting me started in SIP, including Vint Cerf who approved the publication of my first ever Internet-Draft submission to the IETF and Henry Sinnreich who was my partner-in-crime for many years in promoting SIP internally and externally. Thanks to Mark Walsh at Artech House for giving me my first break in publishing. Thanks to Professor Paul Min at Washington University in St. Louis, who invited me to give adjunct teaching a try, and to Dean Jody OSullivan, who for many years supported my Internet Communications elective class at Washington University in St Louis. A big thank you to Harvey Waxman, Phil Edholm, and Anwar Siddiqui my former colleagues at Avaya who all supported my IETF standards work and my writing. Thank you to my current colleagues, Avayans Dan Romascanu, Jake Chacko, and Barbara Augun for their continued support. Thanks to Carol Davids and Dean Bob Carlson for getting me involved as an adjunct at Illinois Institute of Technology. And for this edition, thanks to Marissa Koors, who has been very patient with my writing schedule.
And of course, thanks to all my colleagues in the IETF and SIP Forum, and others in the real-time communication industry. As a community, we are beginning to age, and we recently have lost one of our best, Francois Audet, whose SIP RFCs are referenced throughout this book, especially in the security chapters. We all miss him deeply as a friend, a colleague, and a source of great knowledge on SIP and real-time communication.
And thank you, reader, for your interest and attention. I wish you well with all your SIP projects and deployments!
Acknowledgment
Material in was jointly developed with Dave Piscitello from our book, Understanding VoIP Security.
SIP and the Internet
The Session Initiation Protocol (SIP) is a signaling, presence, and instant messaging protocol developed to set up, modify, and tear down multimedia sessions; request and deliver presence; and send and receive instant messages . When teaching or lecturing about SIP, I begin by explaining that SIP is an Internet protocol. This actually means much more than just that SIP runs over the Internet. This means that SIP uses and takes advantage of the Internet architecture and protocol suite. This chapter will introduce the Transmission Control Protocol/Internet Protocol (TCP/IP) suite that is the foundation for the Internet and SIP. First, some of the basic concepts of Internet protocols such as TCP, IP, User Datagram Protocol (UDP), and the Domain Name System (DNS) will be covered. SIP, along with many other Internet protocols, has been developed by the Internet Engineering Task Force (IETF). The processes, steps, and life cycle involved in the development of Internet standards will also be covered. This chapter ends with a brief history of SIP.
1.1Signaling Protocols
This book is about the session initiation protocol (SIP). As the name implies, the protocol allows two end points to establish media sessions with each other. The main signaling functions of the protocol are as follows:
Location of an end point;
Contacting an end point to determine willingness to establish a session;
Exchange of media information to allow a session to be established;
Modification of existing media sessions;
Teardown of existing media sessions.
SIP has also been extended to request and deliver presence information (online/off-line status and location information such as that contained in a buddy list) as well as instant message sessions. These functions include:
Publishing and uploading of presence information;
Requesting delivery of presence information;
Presence and other event notification;
Transporting of instant messages.
While some of the examples discuss SIP from a telephony perspective, there will be many nontelephony uses for SIP. SIP will likely be used to establish a set of session types that bear almost no resemblance to a telephone call.
The following section will introduce the Internet multimedia protocol stack and discuss these protocols at a high level.
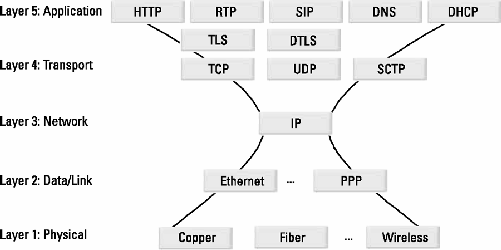
1.2Internet Multimedia Protocol Stack
shows the five layer Internet multimedia protocol stack. The layers shown and protocols identified will be discussed.
1.2.1Physical Layer
The physical layer is the lowest layer of the protocol stack. It shows how devices are physically connected with each other. Common physical layer methods include copper (coax, twisted pair, or other wired connections), photons (fiber optics, laser light, or other photonic sources), or phonons (radio waves, microwaves, or other electromagnetic transmissions).
1.2.2Data/Link Layer
The next layer is the data/link layer, which could be an Ethernet local area network (LAN), Point-to-Point Protocol (PPP), a digital subscriber line (DSL), or even a wireless 802.11 network. This layer performs such functions as symbol exchange, frame synchronization, and physical interface specification. Ethernet typically adds a 13-octet header and a 3-octet footer to every packet sent. Note that an octet is 8 bits of data, sometimes called a byte.
Next page










