Contents
Guide
Hunt A Killer Mystery
The Detectives Puzzle Book
True-Crime Inspired Ciphers, Codes, and Brain Games
Copyright 2022 by Gnomish Hat, Inc. All rights reserved. Any unauthorized duplication in whole or in part or dissemination of this edition by any means (including but not limited to photocopying, electronic devices, digital versions, and the internet) will be prosecuted to the fullest extent of the law.
Published by:
ULYSSES PRESS
PO Box 3440
Berkeley, CA 94703
www.ulyssespress.com
ISBN: 978-1-64604-399-6
ISBN-13: 978-1-6460-4400-9 (eBook)
Library of Congress Control Number: 2022933299
Acquisitions editor: Casie Vogel
Managing editor: Claire Chun
Editor: Kate St.Clair
Proofreader: Renee Rutledge
Interior design and layout: what!design @ whatweb.com
Production: Yesenia Garcia-Lopez
Artwork: from
For sleuths, code-crackers, and puzzle-solvers everywhere

GRAY INVESTIGATIONS
Hello,
Welcome to Hunt A Killer: The Detectives Puzzle Book. First, I want to thank you for your help with my most important cases at Gray Investigations, LLC. But everyone can use some practice, right? Ive designed this training manual as a tool to hone your investigative skills between cases. In the following pages, youll face a variety of challenges, from simple solves to more advanced brainteasers.
These puzzles were designed using details from my previous cases. Each puzzle will offer a scenario and all the necessary hints to solve it.
The challenges in this book are divided into three sections of increasing difficulty. Ill start you off at Aspiring Sleuth (beginner puzzles, ).
By the end of the book, you will find your mental faculties put to the ultimate test. Ive provided some investigative best practices () that include some tips for successful sleuthing as well as an overview of different ciphers Ive seen when people are trying to communicate secrets.
Refer to this whenever you are feeling stuck. All solutions can be found in the back of the book in the order in which they appear. However, to stretch your mind, I advise that you only review the solutions once youre absolutely certain youve already deduced the correct answer.
Im in need of first-rate sleuths on my team. The kind of investigator who can rise to the challenge, doesnt back down when things get hard, and possesses a curious and sharp mind. The kind of investigator who can solve all of these puzzles.
I believe thats you. Good luck!
Michelle Gray
INVESTIGATIVE BEST PRACTICES
Here are some tips, tricks, and strategies to keep in mind as you conduct your investigation:
- Remember to consistently use all of the tools at your disposal.
- Examine every clue, sentence, or piece of evidence very carefully. You never know when an innocuous-seeming phrase will be the key to cracking a code.
- Always keep an eye on the big picture, even when youre combing through the small details. If something isnt lining up right, try to cross-reference it with other facts.
- Always take notes on your findings. Feel free to underline, write on, or highlight the text. Any piece of information, no matter how inconsequential it may seem at first, could prove crucial in cracking the case wide open.
CODES AND CIPHERS GUIDE
Throughout this training guide, you might come across a few codes and ciphers. People with things to hide tend not to leave their secrets sitting out in the open unprotected. Ive created this list to help crack some of the most common cipher types.
ABJAD
This is less a form of cipher and more a system of writing, but Ive seen it used to encode information plenty of times in the past. In simple terms, its the omission of vowels from the text. Sometimes the writer will replace the vowels with a neutral symbol.
If you come across a word written in abjad that could be read several different ways depending on the missing vowels, try looking at the big picture. Context clues can be a lifesaver when youre trying to decipher messages written in this format.
Written in abjad, the word example would look like this:
ATBASH CIPHER
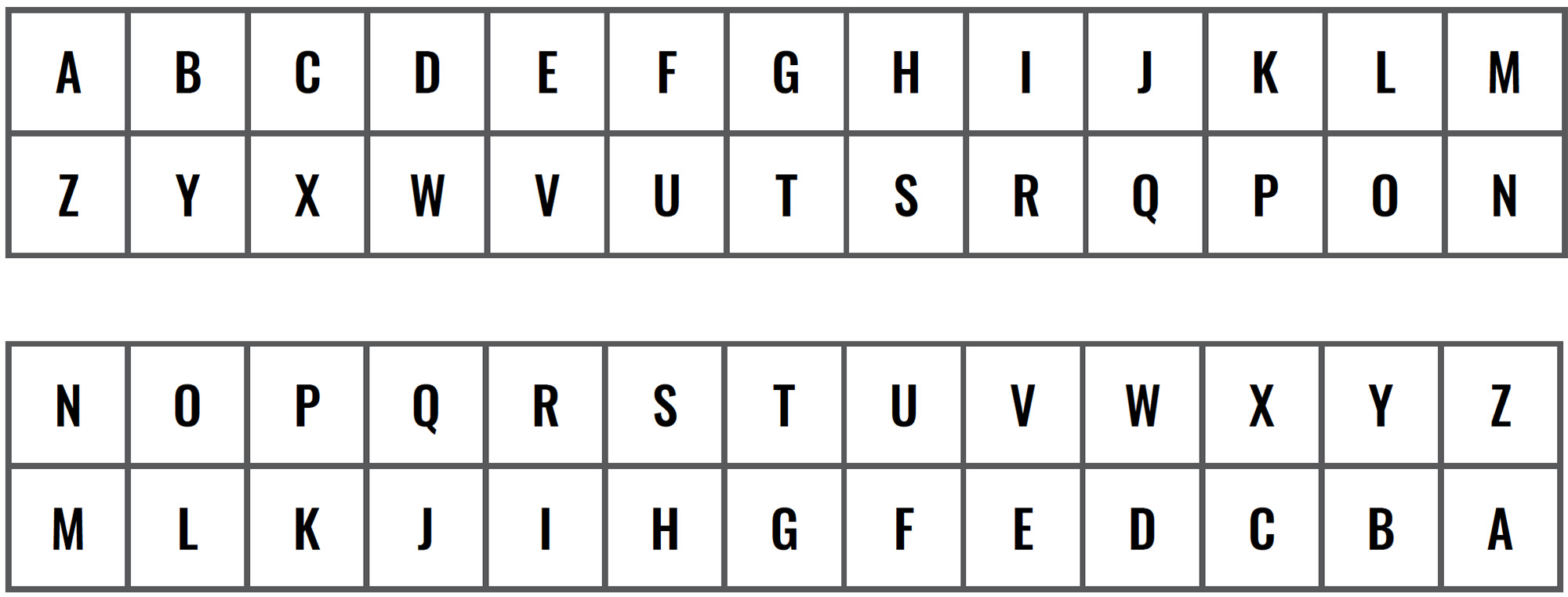
In an atbash cipher, the alphabet is mapped onto itself backward.
Heres a chart that shows what I mean:
In an atbash cipher, the word example would be: vcznkov.
BOOK CIPHER
A book cipher needs to be used in conjunction with a pretty large section of text. This text might be found on a separate piece of paper from the code itself or on the same page.
The cipher tells the reader what words or letters within a passage to look at, and in what order, to find a hidden message.
The text can be anything from a letter to the page of a book to a shopping list, so be vigilant!
To decode a book cipher, be on the lookout for anything that might indicate on what line of a page, what word in a line, or what letter in a word you should focus.
If I wanted to call your attention to the word example in the following text, I could do it by providing you with the location of the word itself with this key: (2/7).
He was exacting in his standards and minimal in his praise.
He always strove to lead by example.
The key (2/7) indicates the location of the hidden word. The word example is on the second line. It is the seventh word of that line.
I could scatter the information even further by providing you with something like this, which gives you the necessary information in the format of line/word/letter:
1/1/2 1/3/2 1/6/3 1/8/1 1/11/1 2/5/1 2/7/7
He was exacting in his standards and minimal in his praise.
He always strove to lead by example.
When read in order, the letters indicated by the key spell out the word example.
CAESAR SHIFT CIPHER
This cipher name is based on the belief that Julius Caesar used it to encrypt his personal communications. To encode a sentence using a shift cipher, the writer shifts each letter of the alphabet forward by a certain fixed number.
For example, the top row of the following chart is the regular, unencoded alphabet. The bottom row is the alphabet shifted forward by five letters.
The word example shifted forward by five letters is jcfruqj.
To decode jcfruqj, you must shift each individual letter backward by five places in the alphabet.
The alphabet can be shifted by any number, although shifting by numbers greater than 26 can get a bit redundant (since, of course, the English alphabet only has 26 letters). In other words, shifting by 27 would be the same as shifting by one, shifting by 28 would be the same as shifting by two, and so on.













 GRAY INVESTIGATIONS
GRAY INVESTIGATIONS