Natasa Zivic - Security in Autonomous Driving
Here you can read online Natasa Zivic - Security in Autonomous Driving full text of the book (entire story) in english for free. Download pdf and epub, get meaning, cover and reviews about this ebook. year: 2020, publisher: De Gruyter, genre: Home and family. Description of the work, (preface) as well as reviews are available. Best literature library LitArk.com created for fans of good reading and offers a wide selection of genres:
Romance novel
Science fiction
Adventure
Detective
Science
History
Home and family
Prose
Art
Politics
Computer
Non-fiction
Religion
Business
Children
Humor
Choose a favorite category and find really read worthwhile books. Enjoy immersion in the world of imagination, feel the emotions of the characters or learn something new for yourself, make an fascinating discovery.

- Book:Security in Autonomous Driving
- Author:
- Publisher:De Gruyter
- Genre:
- Year:2020
- Rating:3 / 5
- Favourites:Add to favourites
- Your mark:
- 60
- 1
- 2
- 3
- 4
- 5
Security in Autonomous Driving: summary, description and annotation
We offer to read an annotation, description, summary or preface (depends on what the author of the book "Security in Autonomous Driving" wrote himself). If you haven't found the necessary information about the book — write in the comments, we will try to find it.
Security in Autonomous Driving — read online for free the complete book (whole text) full work
Below is the text of the book, divided by pages. System saving the place of the last page read, allows you to conveniently read the book "Security in Autonomous Driving" online for free, without having to search again every time where you left off. Put a bookmark, and you can go to the page where you finished reading at any time.
Font size:
Interval:
Bookmark:

ISBN 9783110627077
e-ISBN (PDF) 9783110629613
e-ISBN (EPUB) 9783110627152
Bibliographic information published by the Deutsche Nationalbibliothek
The Deutsche Nationalbibliothek lists this publication in the Deutsche Nationalbibliografie; detailed bibliographic data are available on the Internet at http://dnb.dnb.de.
2020 Walter de Gruyter GmbH, Berlin/Boston
Cryptography is essential to providing security. In this chapter, the basic cryptographic concepts and terminologies are introduced. These concepts and terminologies will be used in different contexts in the following chapters.
Although cryptography is the main point of discussion in this chapter, there is a more generic umbrella term, called cryptology, which can be further split into cryptography and cryptanalysis.
Cryptography is the study and practice of methods for secure communication between two or more parties in the presence of adversaries. The goal is to conceal the meaning of messages exchanged among the communication partners. Cryptography can be further split into subfields such as symmetric encryption, asymmetric encryption and security protocols.
Cryptography provides among others
Data confidentiality through encryption and decryption
Data integrity
Authentication of the communication partners
Authentication of data source
Cryptography is ubiquitous in the modern digital. Some of the applications of cryptography include
Online banking
E-mail exchange
Internet communications
Mobile communications
Virtual private networks
shows cryptology and some of its most important subfields.
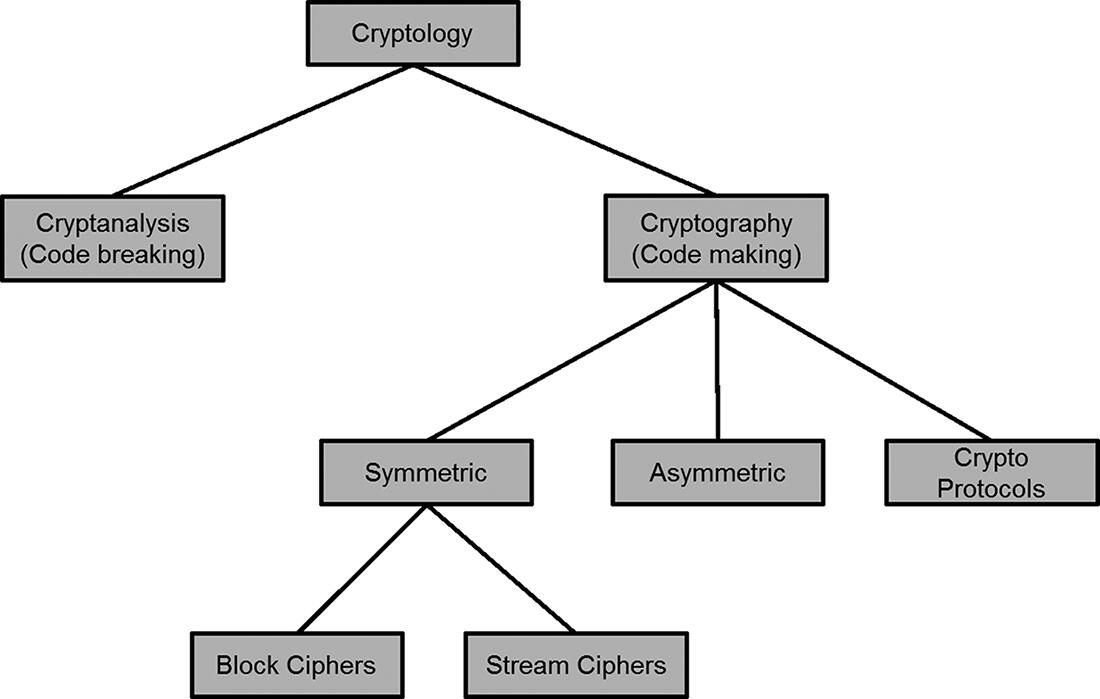
Fig. 1.1: Branches of cryptology.
Encryption transforms the original data, called plaintext, by applying mathematical transformations into another form, called ciphertext, which cannot be understood by a third party or an adversary. The transformation is reversible, which means it is always possible to get back the corresponding plaintext from a given ciphertext. Encryption algorithm uses side information, called a cryptographic key, in order to perform the transformation. The key is shared with the recipient through a secure channel. It is not intended to be disclosed to third parties and should be known only to the intended recipients of the message.
A simplified view of the encryption and decryption process with the help of a shared key K is shown in for example, in a database, and retrieved later when it is decrypted. When the transmission occurs in space, it means that the encrypted data is sent to the receiver over an insecure communication channel. An insecure communication channel is the one which is shared by many communication partners including adversaries.
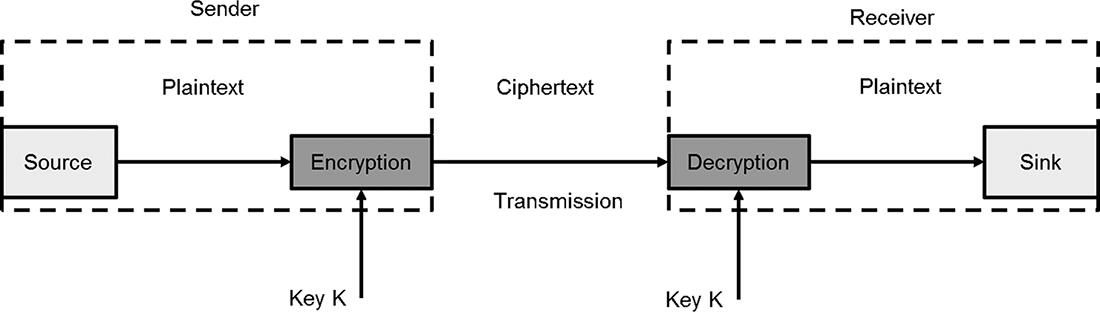
Fig. 1.2: Encryption and decryption.
Decryption is the reverse process of encryption and transforms the ciphertext back to the corresponding plaintext by applying the mathematical transformations in reverse order. In order for decryption to be successful, the same key is needed which was used earlier for encryption of the data. Therefore, it is important to share this key with the desired communication partner and not to disclose it to unintended recipients.
A cryptographic key is needed for encryption as well as decryption. The key is exchanged between the communication partners prior to the start of encrypted communication, that is, encryption/decryption. The key should be kept secret and never be disclosed. If the key is disclosed, the previous and future communication encrypted with the same key is compromised.
A cryptographic protocol performs a security-related function by applying cryptographic functions, that is, it is the application of cryptographic algorithm for a specific purpose. It describes how a cryptographic algorithm should be used in practice.
Most prominent cryptographic protocols used in practice include
Secure hypertext transfer protocol
Transport layer security
Internet protocol security
Medium access control security
Cryptanalysis is the study and application of methods to defeat the objectives of cryptography, for example, by successfully decrypting the ciphertext without the knowledge of key. This can be done in many ways, such as through mathematical analysis or by exploiting the weaknesses in the implementation of cryptographic algorithms. The weaknesses of implementation might exist in the software implementation of the algorithm, the hardware on which the algorithm is running, in the design of the security protocols which make use of the cryptographic algorithms, in the implementation of these protocols or in a combination of these.
A person who performs cryptanalysis is called a cryptanalyst. A cryptanalyst is also typically called an attacker or a hacker in laymans terms. The main goal of a cryptanalyst is defeating the objectives of cryptography. A cryptanalyst is interested in knowing the plaintext corresponding to a given ciphertext. However, the ideal success scenario for a cryptanalyst is his or her ability to extract the cryptographic key used in cryptography. In order to obtain this key, a cryptanalyst can use multiple methods.
The most trivial of these methods is a brute-force attack. Brute-force attack looks for all possible combinations of the key, until the right key is found. Considering a key length of 32 bits, this would mean that the cryptanalyst looks for all possible keys. This is equal to trying all of the 232 possibilities, also known as the key space. The effort required by the cryptanalyst can be increased considerably by increasing the key length. For example, doubling the key length to 64 bits will increase the efforts of the brute-force attack to 264 searches. However, with even larger key lengths, such as 1,024 bits, a brute-force attack becomes impractical with the current technology. A cryptanalyst needs other intelligent methods to reduce the efforts required to search for a key. As an example, dictionary attacks might be used instead of searching the whole key space.
Confusion aims to make the relationship between a given plaintext and the corresponding ciphertext as complicated as possible. Confusion is a mathematical operation, after which it is not possible to link the statistics of the plaintext with the statistics of the corresponding ciphertext. Thus given a ciphertext, it should be impossible to derive the corresponding plaintext or parts of it. Typically, confusion is obtained through bit or byte substitution in todays ciphers.
Font size:
Interval:
Bookmark:
Similar books «Security in Autonomous Driving»
Look at similar books to Security in Autonomous Driving. We have selected literature similar in name and meaning in the hope of providing readers with more options to find new, interesting, not yet read works.
Discussion, reviews of the book Security in Autonomous Driving and just readers' own opinions. Leave your comments, write what you think about the work, its meaning or the main characters. Specify what exactly you liked and what you didn't like, and why you think so.