RAXX STAR - LINUX BASIC FOR ETHICAL HACKING PART-1: BY RAXXSTAR (Linux for Beginner)
Here you can read online RAXX STAR - LINUX BASIC FOR ETHICAL HACKING PART-1: BY RAXXSTAR (Linux for Beginner) full text of the book (entire story) in english for free. Download pdf and epub, get meaning, cover and reviews about this ebook. year: 2020, genre: Computer. Description of the work, (preface) as well as reviews are available. Best literature library LitArk.com created for fans of good reading and offers a wide selection of genres:
Romance novel
Science fiction
Adventure
Detective
Science
History
Home and family
Prose
Art
Politics
Computer
Non-fiction
Religion
Business
Children
Humor
Choose a favorite category and find really read worthwhile books. Enjoy immersion in the world of imagination, feel the emotions of the characters or learn something new for yourself, make an fascinating discovery.
LINUX BASIC FOR ETHICAL HACKING PART-1: BY RAXXSTAR (Linux for Beginner): summary, description and annotation
We offer to read an annotation, description, summary or preface (depends on what the author of the book "LINUX BASIC FOR ETHICAL HACKING PART-1: BY RAXXSTAR (Linux for Beginner)" wrote himself). If you haven't found the necessary information about the book — write in the comments, we will try to find it.
RAXX STAR: author's other books
Who wrote LINUX BASIC FOR ETHICAL HACKING PART-1: BY RAXXSTAR (Linux for Beginner)? Find out the surname, the name of the author of the book and a list of all author's works by series.
LINUX BASIC FOR ETHICAL HACKING PART-1: BY RAXXSTAR (Linux for Beginner) — read online for free the complete book (whole text) full work
Below is the text of the book, divided by pages. System saving the place of the last page read, allows you to conveniently read the book "LINUX BASIC FOR ETHICAL HACKING PART-1: BY RAXXSTAR (Linux for Beginner)" online for free, without having to search again every time where you left off. Put a bookmark, and you can go to the page where you finished reading at any time.
Font size:
Interval:
Bookmark:
Linux Basic for Ethical Hacking part-1
By
(RAXX STAR-pen name)
Copyright (Insert year of publishing) by (Insert author or publisher name) - All rights reserved.
It is not legal to reproduce, duplicate, or transmit any part of this document in either electronic means or printed format. Recording of this publication is strictly prohibited.
This book is dedicated to:
To all that brilliant minds who want to bring revolution in the society
Table of Contents
Chapter Six : Networking Besic
Chapter Seven: Managing permission
A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux.
There are some exceptions, though, including software like Cain and Abel , Havij, Zenmap , and Metasploit that are developed or ported for Windows.
When these Linux apps are developed in Linux and then ported over to Windows, they often lose some of their capabilities. In addition, there are capabilities built into Linux that simply are not available in Windows. That is why hacker tools are in most cases ONLY developed for Linux.
To summarize, to be a real expert hacker, you should master a few Linux skills and work from a Linux distribution like BackTrack or Kali.
For those of you who've never used Linux, I dedicate this series on the basics of Linux with an emphasis on the skills you need for hacking. So, let's open up BackTrack or your other Linux distribution and let me show you a few things.
(Capitalize first letter of each word in chapter titles)
Once you've booted up BackTrack, logged in as "root" and then type:
- bt > startx
You should have a screen that looks similar to this.
Step : 2 : Open a Terminal
To become proficient in Linux, you MUST master the terminal. Many things can be done now in the various Linux distributions by simply pointing and clicking, similar to Windows or Mac OS, but the expert hacker must know how to use the terminal to run most of the hacking tools.
If you've ever used the command prompt in Windows, the Linux terminal is similar, but far more powerful. Unlike the Windows command prompt, you can do EVERYTHING in Linux from the terminal and control it more precisely than in Windows.
It's important to keep in mind that unlike Windows, Linux is case-sensitive. This means that "Desktop" is different from "desktop" which is different from "DeskTop". Those who are new to Linux often find this challenging, so try to keep this in mind.
Step : 3 : Examine the directory structure
Let's start with some basic Linux. Many beginners get tripped up by the structure of the file system in Linux. Unlike Windows, Linux's file system is not linked to a physical drive like in Windows, so we don't have a c:\ at the beginning of our Linux file system, but rather a /.
The forward slash (/) represents the "root" of the file system or the very top of the file system. All other directories (folders) are beneath this directory just like folders and sub-folders are beneath the c:\ drive.
To visualize the file system, let's take a look at this diagram below.
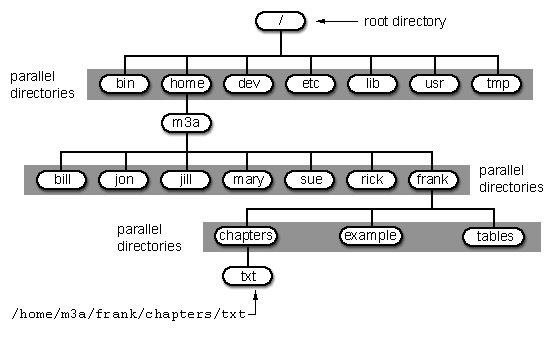
It's important to have a basic understanding of this file structure because often we need to navigate through it from the terminal without the use of a graphical tool like Windows Explorer.
A couple key things to note in this graphical representation:
- The /bin directory is where binaries are stored. These are the programs that make Linux run.
- /etc is generally where the configuration files are stored. In Linux, nearly everything is configured with a text file that is stored under /etc .
- /dev directory holds device files, similar to Windows device drivers.
- /var is generally where log files, among other files, are stored.
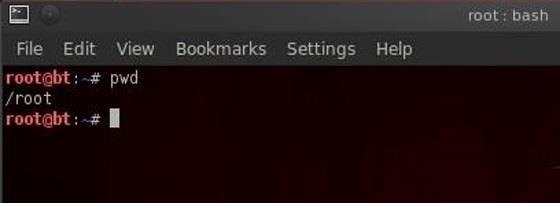
Step:4:Using pwd
When we open a terminal in BackTrack, the default directory we're in is our "home" directory. As you can see from the graphic above, it's to the right of the "root" directory or one level "below" root. We can confirm what directory we are in by typing:
bt > pwd
pwd stands for "present working directory" and as you can see, it returns "/root" meaning we're in the root users directory (don't confuse this with the top of the directory tree "root." This is the root users directory).
pwd is a handy command to remember as we can use it any time to tell us where we are in the directory tree.
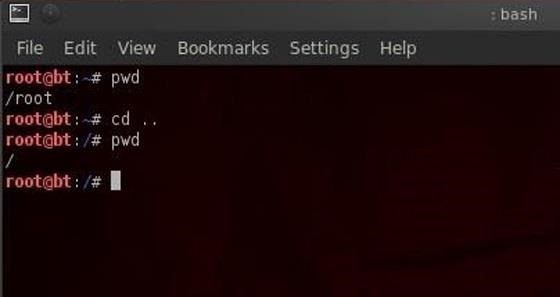
Step:5:Using Cd command
We can change the directory we're working in by using the cd (change directory) command. In this case, let's navigate "up" to the top of the directory structure by typing:
bt > cd ..
The cd command followed by the double dots (..) says, "move me up one level in the directory tree." Notice that our command prompt has changed and when we type pwd we see that Linux responds by telling us we are in the "/" or the top of the directory tree (or the root directory).
bt > pwd
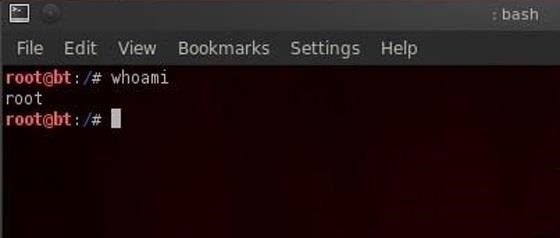
Step:6: Using The whoami command
In our last lesson of this tutorial, we'll use the whoami command. This command will return the name of the user we're logged in as. Since we're the root user, we can log in to any user account and that user's name would be displayed here.
bt > whoami
Step:1: Change Directory(cd)
We can change directories in multiple ways with cd. As I showed you in my previous article, we can use cd .. to move up one level in the directory tree. We can also move directly to the root directory by typing cd / or move to our home directory by cd ~.
More often, we will use cd to move to a directory by using the absolute path of the directory. This mean that we write out the entire path of the directory we want to move to after cd. We can also move to the directory by using the relative path of the directory. This means that we don't need to write the entire path, but simply use the path that we're currently in and append to it. Let's look at some examples.
Let's say we're in our root user directory in BackTrack and we want to move to the aircrack-ng directory (we'll be doing some aircrack tutorials soon). We can simply type:
bt > cd /pentest/wireless/aircrack-ng
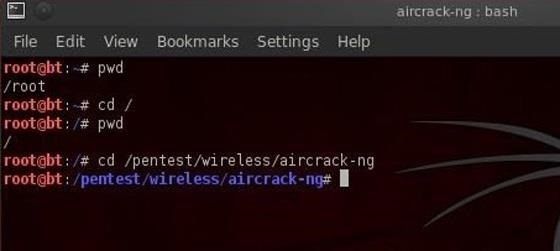
This will take us directly to the aircrack-ng directory.
Now let's say we want to go to the scripts sub-directory within aircrack-ng. We could type out the full path to the sub-directory, but it's much simpler to type the relative path from where we are. We know we are /pentest/wireless/aircrack-ng, so type:
bt > cd scripts
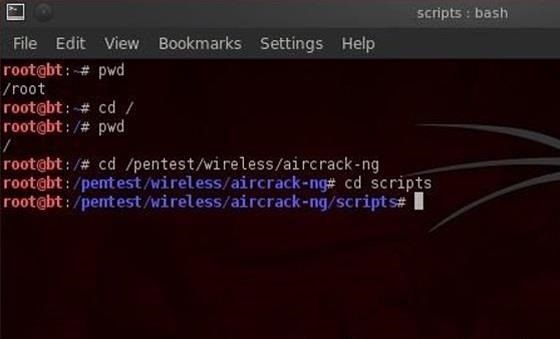
Font size:
Interval:
Bookmark:
Similar books «LINUX BASIC FOR ETHICAL HACKING PART-1: BY RAXXSTAR (Linux for Beginner)»
Look at similar books to LINUX BASIC FOR ETHICAL HACKING PART-1: BY RAXXSTAR (Linux for Beginner). We have selected literature similar in name and meaning in the hope of providing readers with more options to find new, interesting, not yet read works.
Discussion, reviews of the book LINUX BASIC FOR ETHICAL HACKING PART-1: BY RAXXSTAR (Linux for Beginner) and just readers' own opinions. Leave your comments, write what you think about the work, its meaning or the main characters. Specify what exactly you liked and what you didn't like, and why you think so.




