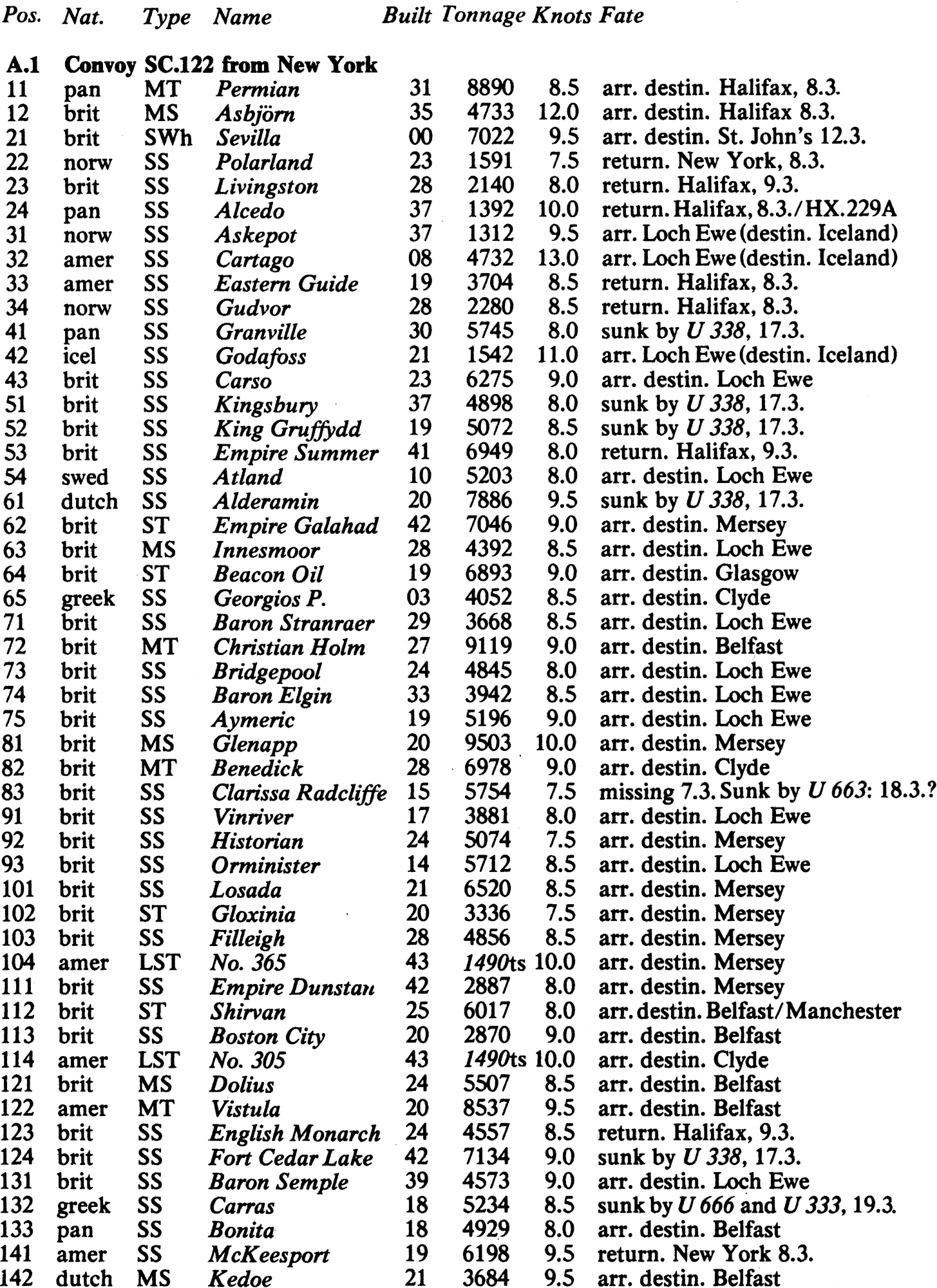
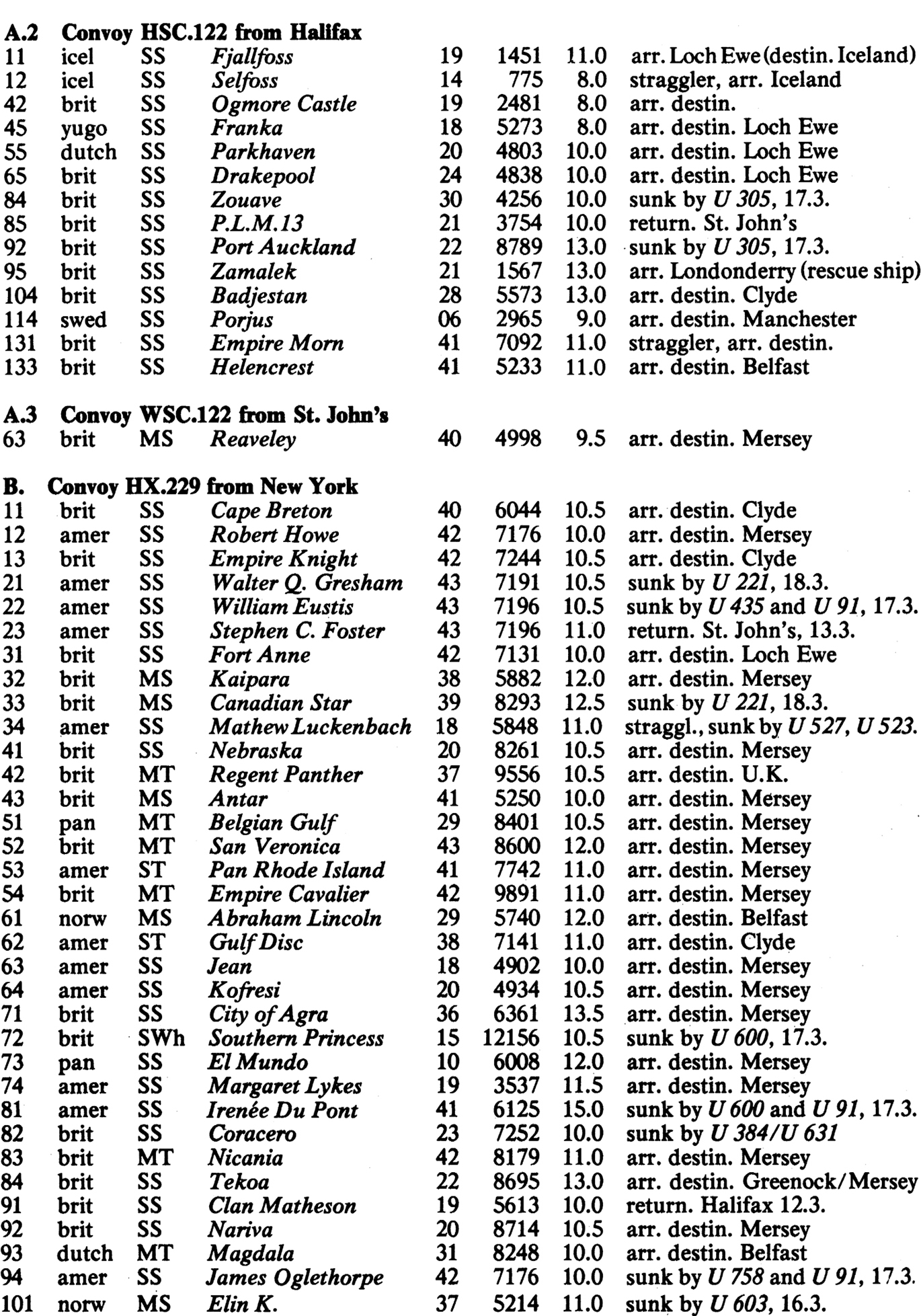
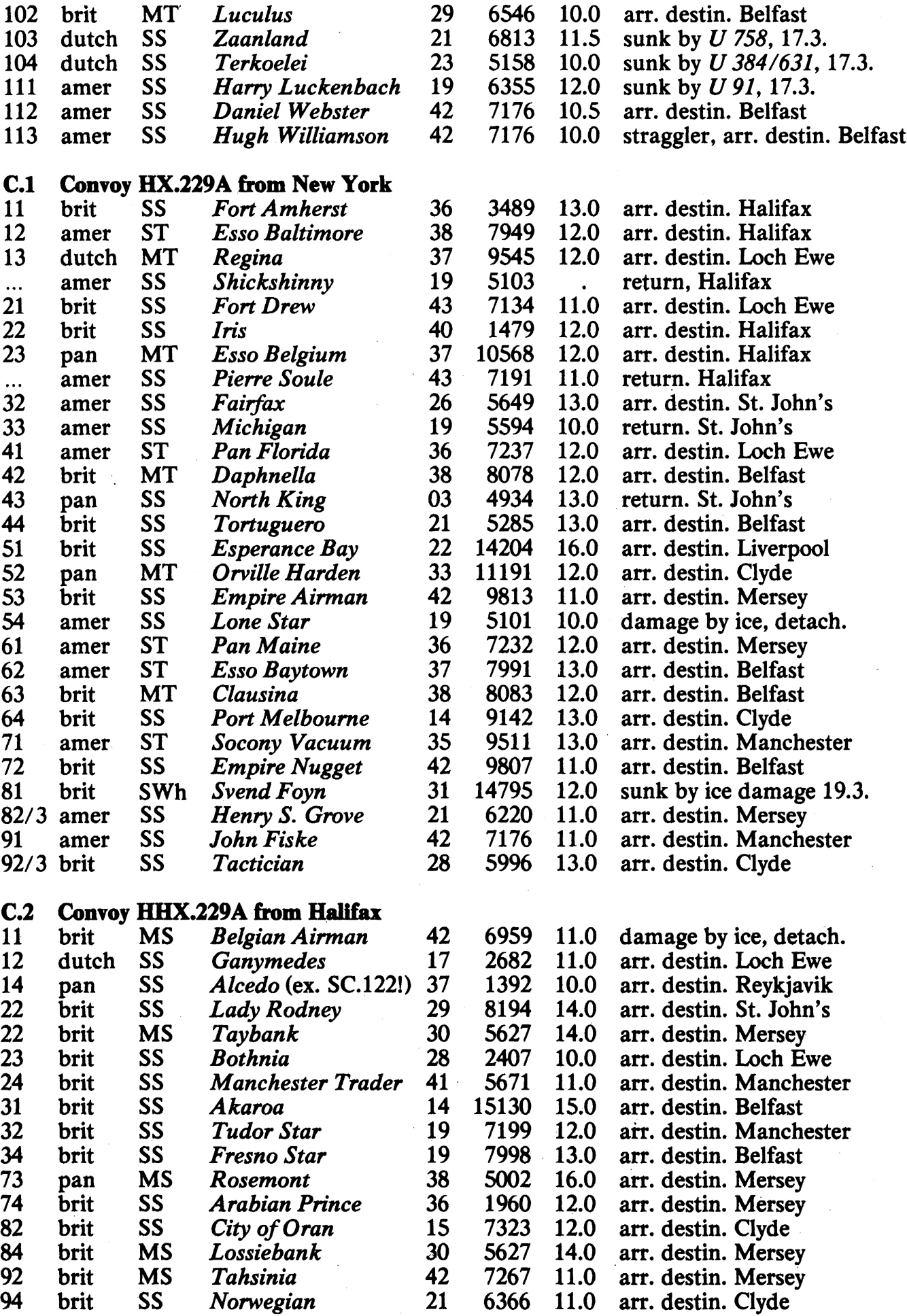
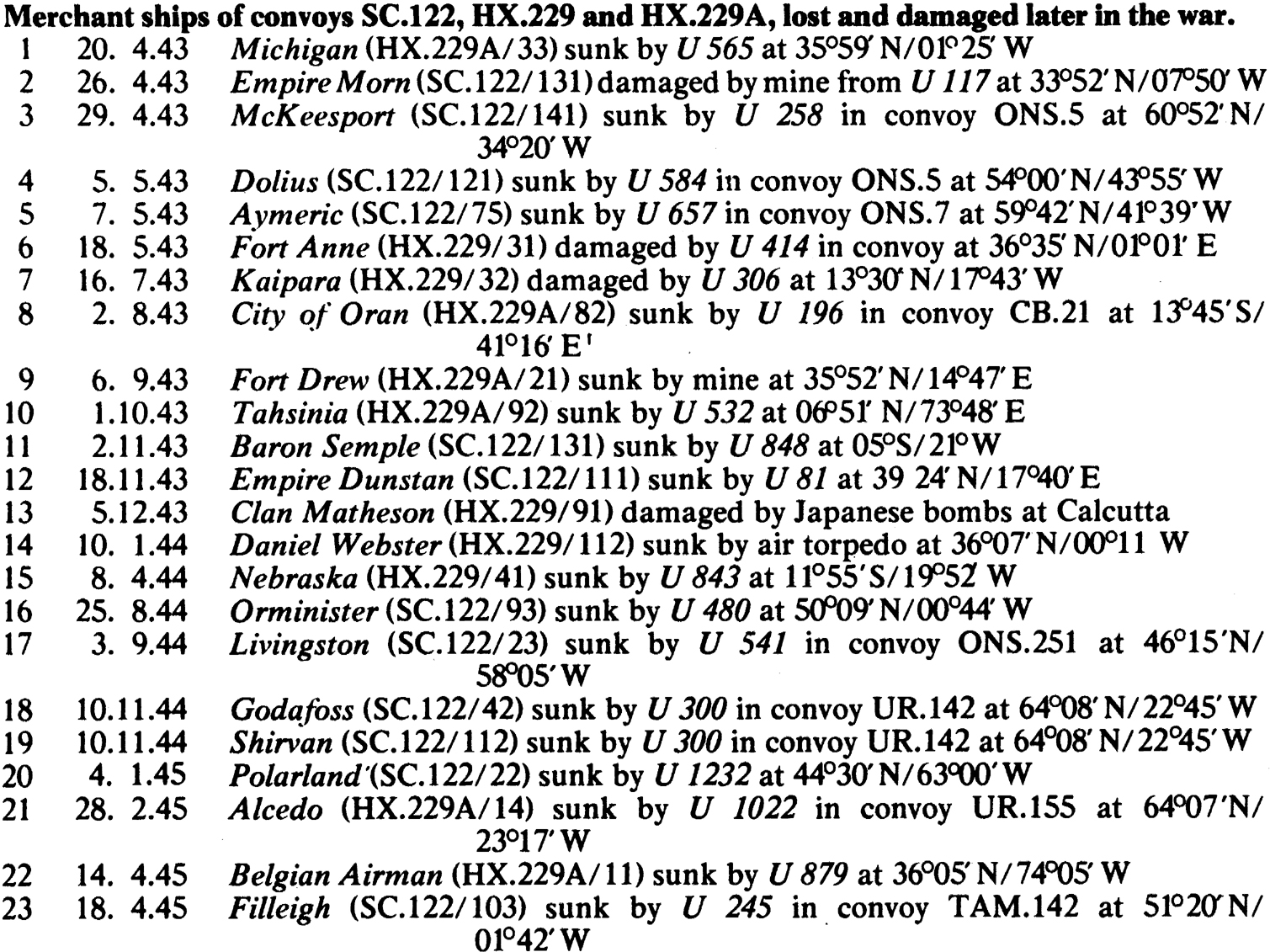
APPENDIX 10
Notes on the Security of the German Decoding Systems
Translated by Lt. Col. A. J. Barker
S hortly after the manuscript of this book had been sent to the publishers, the author learned that three new books dealing with Allied code-breaking operations in World War 2 had appeared in Poland, France and Britain respectively. (1) Published in Britain, Group Captain F. W. Winterbotham's book caused a sensation as he had held an important post at the British Code and Cipher School at Bletchley Park. Because until 1975 code-breaking techniques were considered to be a classified subject, Winterbotham's account was based solely on personal recollections. But his book stimulated interest which led to the publication (2) of a number of articles, some of which were critical (3) of Winterbotham's claimsthe criticism stemming mainly from circles associated with the Royal Navy. Because of the controversy that had been aroused, the British Government reviewed the security classification of wartime deciphering activities and sanctioned the publication of certain files on the subject in the spring of 1976.
During the past twelve months the author has been studying the problems associated with the World War II code-breaking operationsin particular those related to the German Navy's radio traffic. For this study it was necessary to reproduce the sequence of development for the Kriegsmarine's decoding machine, and on the basis of declassified information available this appeared to be a formidable undertaking. Fortunately it was found that some gaps in the story could be closed with information provided by experts who had worked on the original projects. For this information and other help the author is indebted to the following: Dr Erich Httenhain, formerly employed in the Coding Section of the German High Command; Captain Hanns Singer of the German Navy who was concerned with the development of cipher equipment for the Kriegsmarine; and Captain Hans Meckel, also of the German Navy, who was responsible for telecommunications in the German U-Boat Command. On the Allied side the help and cooperation afforded by the naval historian Captain S. W. Roskill; Vice-Admiral B. B. Schofield, Director of the Trade Division; Commander Patrick Beesly, Acting Head of the Admiralty's Submarine Tracking Room; Mrs. Mary Z. Pain, wartime assistant to the Royal Navy's Liaison Officer at the Code Centre Bletchley Park; Commander M. G. Saunders; Captain Kenneth Knowles, Chief of the Convoy Routing SectionWashington's equivalent to the British Submarine Tracking Room, is gratefully acknowledged. Their efforts facilitated access to the relevant documents in the Public Records Office, and made possible the correct interpretation of their contents. This, then is the background to the brief survey of German cipher systems and the British code-breaking operations which follows.
THE DEVELOPMENT OF THE CIPHER SYSTEMS BASED ON THE CIPHER MACHINES ENIGMA AND M
Radio traffic in war is an important source of intelligence, as radio waves cannot be limited to specific receivers and military transmissions are picked up by the enemy. A listening watch is maintained on enemy radio frequencies, and all transmissions are monitored. The evaluation process of such transmissions then begins by three different methods.
The evaluation of contents system takes clear texts and using them in comparison attempts to decode or decipher the encoded texts by analytical or technical methods one of which is code-breaking. Even without being able to understand the contents of the messages, however, a good deal of information will already have been revealed. An analysis of the trafficits overall density and the relationship of transmissions to particular stationswill indicate the deployment of the enemy's forces and hence his Order of Battle. It may also indicate that he is concentrating units for an operation; this is important information of current interest. Additionally, direction finding techniques enable the geographical location of a transmitter to be plotted. This information, together with that gleaned from the traffic analysis, enables conclusions to be drawn to the positioning and movement of enemy units and vessels.
Thus, from one or more of the three components of the radio-monitoring process it is possible to gain a fairly accurate picture of the deployment of enemy radio transmitters [and hence of units and vessels]. Consequently [in World War 2], in order to make the construction of the intelligence jigsaw more difficult, army and air force units would employ telephone and teletype communications for as long as possible and until they were actually operationally deployed. Ships in port would also use the shore telephone links, and vessels at sea would preserve radio silence for as long as possible before an operation or until their presence had been detected by the enemy.
If the three components of the radio-monitoring process appear to be overshadowed by interest in code-breaking procedures, it must be stressed that traffic analysis and direction finding always played a major role in wartime intelligenceoften supplementing the information disclosed by the code-breakers, and facilitating the proper evaluation of such information.
There are two methods of encoding a text. The simplest is to substitute different letters and figures for those appearing in the original. This substitution process may range from the replacement of one letter by another, producing a form of code easily cracked, via complicated exchange systems requiring the use of manually serviced exchange tablets, to mechanical systems in which the exchange of letters is effected in such a way that a specific letter or figure of the original text is replaced by the same substitute letter only after long periods. The second method involves the use of a form of dictionary termed a Code Book by means of which groups of letters in the textwords, phrases, or sentencesare replaced by arbitrarily assigned signals known as a code group. A combination of both methods is of course possiblecode groups being reencoded by a letter exchange system.
Because it increased the length of periods in the letter substitution system the invention of the cryptographic cylinder was an important advance. Rows of figures or letters of the alphabet are inscribed on an adjustable ring and during an encoding operation this ring is automatically rotated when a letter of the text has been exchanged for the appropriate symbol on the cylinder. Thus, in a word of the uncoded text in which the same letter appears twice, the same symbol is not repeated. This automatic rotationthe symbol shunting which rearranges the encoding alphabetis known by cryptographers as a Caesar series, and a message encoded in this method, while more difficult to solve than messages encoded by the two simpler methods, is still relatively easy to decipher. However, the cryptographic cylinder continued to serve as the basis of many sophisticated machines, but in power-driven machines the contacts on the starting symbols were linked electrically to contacts on other symbols arbitrarily selected as the end symbols of the message; the effect was to upset the continuity of the symbols.