García-Mateo Carmen - Voice Biometrics
Here you can read online García-Mateo Carmen - Voice Biometrics full text of the book (entire story) in english for free. Download pdf and epub, get meaning, cover and reviews about this ebook. year: 2021, publisher: Institution of Engineering & Technology, genre: Romance novel. Description of the work, (preface) as well as reviews are available. Best literature library LitArk.com created for fans of good reading and offers a wide selection of genres:
Romance novel
Science fiction
Adventure
Detective
Science
History
Home and family
Prose
Art
Politics
Computer
Non-fiction
Religion
Business
Children
Humor
Choose a favorite category and find really read worthwhile books. Enjoy immersion in the world of imagination, feel the emotions of the characters or learn something new for yourself, make an fascinating discovery.
- Book:Voice Biometrics
- Author:
- Publisher:Institution of Engineering & Technology
- Genre:
- Year:2021
- Rating:4 / 5
- Favourites:Add to favourites
- Your mark:
- 80
- 1
- 2
- 3
- 4
- 5
Voice Biometrics: summary, description and annotation
We offer to read an annotation, description, summary or preface (depends on what the author of the book "Voice Biometrics" wrote himself). If you haven't found the necessary information about the book — write in the comments, we will try to find it.
Voice Biometrics — read online for free the complete book (whole text) full work
Below is the text of the book, divided by pages. System saving the place of the last page read, allows you to conveniently read the book "Voice Biometrics" online for free, without having to search again every time where you left off. Put a bookmark, and you can go to the page where you finished reading at any time.
Font size:
Interval:
Bookmark:

IET Book Series in Advances in Biometrics Call for authors
Book Series Editor:Michael Fairhurst, University of Kent, UK
This Book Series provides the foundation on which a valuable library of reference volumes on the topic of Biometrics is build. Iris and Periocular Biometric Recognition, Mobile Biometrics and User-centric Privacyand Security in Biometrics are the first published volumes in the Series, with further titles currently being commissioned. Proposals for coherently integrated, multi-author edited contributions are welcome for consideration. Please email your proposal to the Book Series Editor, Professor Michael Fairhurst, at: .
Published Titles in This Series:
Published 2018 Drahansk Martin (ed) / Hand-Based Biometrics: Methods and technology
Published 2017 Guo and Wechsler (Eds) / Mobile Biometrics
Published 2017 Rathgeb and Bush (eds) / Iris and Periocular Biometric Recognition.
Published 2017 Vielhauer / Privacy and Security in Biometrics
Published 2013 Fairhurst / Age Factors in Biometrics Processing
Edited by
Carmen Garca-Mateo and Grard Chollet
The Institution of Engineering and Technology
Published by The Institution of Engineering and Technology, London, United Kingdom
The Institution of Engineering and Technology is registered as a Charity in England & Wales (no. 211014) and Scotland (no. SC038698).
The Institution of Engineering and Technology 2021
First published 2021
This publication is copyright under the Berne Convention and the Universal Copyright Convention. All rights reserved. Apart from any fair dealing for the purposes of research or private study, or criticism or review, as permitted under the Copyright, Designs and Patents Act 1988, this publication may be reproduced, stored or transmitted, in any form or by any means, only with the prior permission in writing of the publishers, or in the case of reprographic reproduction in accordance with the terms of licences issued by the Copyright Licensing Agency. Enquiries concerning reproduction outside those terms should be sent to the publisher at the undermentioned address:
The Institution of Engineering and Technology
Michael Faraday House
Six Hills Way, Stevenage
Herts, SG1 2AY, United Kingdom
www.theiet.org
While the authors and publisher believe that the information and guidance given in this work are correct, all parties must rely upon their own skill and judgement when making use of them. Neither the author nor publisher assumes any liability to anyone for any loss or damage caused by any error or omission in the work, whether such an error or omission is the result of negligence or any other cause. Any and all such liability is disclaimed.
The moral rights of the author to be identified as author of this work have been asserted by him in accordance with the Copyright, Designs and Patents Act 1988.
British Library Cataloguing in Publication Data
A catalogue record for this product is available from the British Library
ISBN 978-1-78561-900-7 (hardback)
ISBN 978-1-78561-901-4 (PDF)
Typeset in India by Exeter Premedia Services Private Limited
Printed in the UK by CPI Group (UK) Ltd, Croydon
This figure represents a standard feed-forward DNN architecture, with an input layer, a given number of hidden layers and the output layer. Each hidden unit applies a transformation g (usually non-linear function) to the weighted sum of the inputs to that given unit according to the following expression: 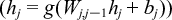 , where W and b are the parameters of the DNN (weights matrices and bias vectors, respectively). Finally, the output layer provides the score vector according to the target task (e.g., for the case of classification, the probability of an input vector belong to each class) , where W and b are the parameters of the DNN (weights matrices and bias vectors, respectively). Finally, the output layer provides the score vector according to the target task (e.g., for the case of classification, the probability of an input vector belong to each class) |
| This figure shows a graphical representation of a cepstral (upper part) versus bottleneck (bottom part) feature-based speaker recognition system. For the bottleneck (BN) feature-based approach, sometimes, MFCCs are concatenated with the bottleneck features before the i-vector modeling |
| This is a representation of the generic scheme of a DNN used as embedding extractor |
| Direct vs. indirect attacks. After [] |
| Classification of various attacks on an ASV system |
| Motivation for attacks on ASV |
| SSD system for ASV system |
| Using ASV to attack the victim ASV |
| Privacy-preservation for speech corpus. After [] |
| (a) Attack using target selection but without voice privacy system, and (b) attack using target selection with voice privacy system |
| Example of a privacy-preserving machine learning framework |
| Fifth degree Chebyshev polynomial approximation () |
| Piecewise linear approximation of a FW |
| Diagram of the proposed speaker selection strategy for voice conversion. The dots represent the different speakers, and those inside the blue ellipse are training speakers that share a parallel corpus |
| DET curves of the different systems on the VCTK corpus |
| DET curves of the different systems on the VCC 2016 corpus |
| General design of a biometric system; source and shape semantics: ISO/IEC 39794-1 [] |
| Overview on attack points in biometric systems with depicted scope of ISO/IEC 30107-1 [] |
| General biometric system composition with PAD; source and shape semantics: ISO/IEC 30107-1 [] |
| Typical architecture for a commercial automated password reset system |
| Standard deviation of error rate estimate as a function of N. FA: false accept; STD, standard deviation |
| Histogram of false accept rates across 10000 population with global threshold |
| 95% Confidence interval for user false accept rate using global and per-user thresholds. FA: false accept |
| Histogram of false accept rates across 10000 population with per-user thresholds |
| An example of LR estimation given the same-speaker (H0) and different-speaker (H1) hypotheses and an evidential speaker recognition score E |
| Block diagram of TSPs common speaker verification systems for NIST 2019 CTS and multimedia challenges |
| DET performance curves on the development set of SRE19 CTS database for system (1) based on TDNN, system (2) based on E-TDNN, and the fusion of (1) and (2) |
| Block diagram of the TSP face recognition system for SRE19 multimedia challenge |
| The Multi-PIE 68 points markup [] used for face landmark annotation |
| Example of the preprocessing of an image from LFW using eyes and nose positions |
| Examples from the alignment of images from the ATSIP2018 database with good acquisition conditions, i.e., frontal face, good illumination |
| Examples from the alignment of images from the ATSIP2018 database with bad acquisition conditions, i.e., face turned to a great degree |
| DET curve performance of the submitted face recognition system on the dev and test partitions of the multimedia challenge |
Font size:
Interval:
Bookmark:
Similar books «Voice Biometrics»
Look at similar books to Voice Biometrics. We have selected literature similar in name and meaning in the hope of providing readers with more options to find new, interesting, not yet read works.
Discussion, reviews of the book Voice Biometrics and just readers' own opinions. Leave your comments, write what you think about the work, its meaning or the main characters. Specify what exactly you liked and what you didn't like, and why you think so.












