1.1 Overview
A recent development in communication technology, storage device, and digital recording has created an Internet environment with the ability to distribute, duplicate, obtain, and replicate digital media without any quality lossless. However, this technology advancement is worrying multimedia content publishing industries due to unauthorized access through digital media content which is requiring a serious and immediate protection for Intellectual Property Rights. Although a traditional cryptography approach can apply to prevent an unauthorized party to access a digital media content by encrypting the content of the media, cryptography technology has some limitations to fully protect the Intellectual Property Rights. Therefore, it is obvious that other technology should be applied to construct the Intellectual Property Rights, track the digital media content, and provide the digital media content authentication which ensure authorized access and prevent illegal manipulation to the content of digital media. As an effective solution, Digital Watermarking is applying to facilitate the requirements for protecting the Intellectual Property Rights of a digital media. Currently, digital watermarking is becoming the hot topic for the research communities that actively working on this industry. The idea of digital watermarking is the hiding information about digital content as a metadata within digital content to protect the ownership. Probably, this idea is invented in Germany due to a German term wassermark is available that means effect of water on paper [].
Apart from the basic concepts in data hiding, this book is attempting to cover recent and practical applications of digital watermarking in all computer science fields in order to provide an overview on different roles of digital watermarking in computer science. Figure shows the main branch in data-hiding technology. It presents the main focus of this book to narrow down the constraints in the field of data hiding. As shown, each chapter of this book is dedicated to an application of digital watermarking in order to provide a deep and comprehensive overview on major digital watermarking technology.
Fig. 1.1
Book focus in the field of data hiding
1.2 Fundamentals of Digital Watermarking
The art of watermarking is hiding extra information (which could be an image logo, text message, and raw watermark bits) inside the content of the host objects such as images, audio signals, speech signals, 3D graphical objects, videos, texts, software codes, network streams, XML data, and ontologies without serious degradation on the quality of the objects. The watermark must be detectable from the watermarked content even when intentional and unintentional manipulations have been conducted on the digital watermarked content. Therefore, digital watermarking can be expressed by two main processes: watermark embedding and watermark extraction, which are illustrated in Fig..
Fig. 1.2
Concept of digital watermarking
The watermarking processes can be described formally. For creating a watermarked cover W C, a watermark data W should be embedded into a cover object O c. As a result, watermark distortion is defined by the deference between O c and W C. Usually, the raw watermark data W is encoded by using a secret key K in order to improve the security and decrease the watermark payload P. Then, a modulated/scaled watermark method W M is used to embed watermark bits into the cover object O c with minimum embedding distortion to provide enough imperceptibility. After embedding the watermark, the watermarked cover W C may be imposed to intentional and unintentional manipulations such as conversions, compression, noise, adding, removing, and editing which would change it to manipulated watermarked cover
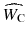
. The amount of degradation can be computed by finding the deference between
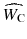
and W C which may be considered as noise of the environment.
Detection of the watermark is done based on the received manipulated watermarked cover
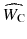
and the watermark key K . There are two major approaches for watermark detection: The first one is informed detector (non-blind) approach that requires original cover work O c, and the second one is oblivious detector (blind) approach which extracts watermark only from manipulated watermarked cover
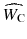
without any knowledge of the original cover O c. Thus, digital watermarking can be categorized based on source and extraction module into three main classes:
- (a)
Blind watermarking that detects the watermark without the original cover O c. However, in some applications, key K uses are required for generating random sequences.
- (b)
Semi-blind watermarking that detects the watermark with using some information about the original cover O c. For example, it should access to the published watermarked signal that is the original signal after just adding the watermarks.
- (c)
Non-blind watermarking that detects the watermark using the original cover O c and manipulated watermarked cover
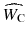
together.
There is always possibility to categorize the watermarking techniques based on various factors. With respect to robustness, the watermarking methods can be divided into three main groups:
- (a)
Robust digital watermarking that detects the watermark even under serious and malicious manipulation.
- (b)
Semi-fragile digital watermarking that detects the watermark just under unintentional manipulation.
- (c)
Fragile digital watermarking that detects the watermark only if no intentional and unintentional manipulations are took place. This type of watermark is needed for paper of bank notes. These watermarks do not survive any kind of copying and can be used to indicate the bills authenticity. Reaching for fragility is more difficult than robustness.
1.3 Requirements of Digital Watermarking
Basically digital watermarking can be considered as a tradeoff problem due to the nature of digital watermarking which is competing among payload, transparency, robustness, and security. Depending on various and wide applications of the digital watermarking, the watermarking system is designed based on these requirement and system inherent properties. Figure illustrates the requirements of digital watermarking. As shown, these requirements oppose one another and to make them meet is difficult. Within this magic triangle, the mode of operation of a particular watermarking system can be set. For example, a high data rate system may enhance its rate by lowering the robustness at the same moment.













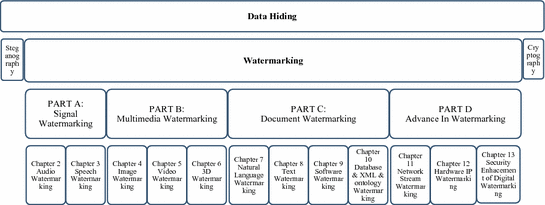

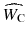 . The amount of degradation can be computed by finding the deference between
. The amount of degradation can be computed by finding the deference between 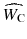 and W C which may be considered as noise of the environment.
and W C which may be considered as noise of the environment.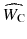 and the watermark key K . There are two major approaches for watermark detection: The first one is informed detector (non-blind) approach that requires original cover work O c, and the second one is oblivious detector (blind) approach which extracts watermark only from manipulated watermarked cover
and the watermark key K . There are two major approaches for watermark detection: The first one is informed detector (non-blind) approach that requires original cover work O c, and the second one is oblivious detector (blind) approach which extracts watermark only from manipulated watermarked cover 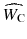 without any knowledge of the original cover O c. Thus, digital watermarking can be categorized based on source and extraction module into three main classes:
without any knowledge of the original cover O c. Thus, digital watermarking can be categorized based on source and extraction module into three main classes: 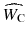 together.
together.