LINUX SERVICES DEPLOYMENT
Tested in Red Hat Linux 8.x
FABIAN MESTRE SOCARRAS
Copyright 2021 Aptiva Labs SAS
The texts related in this material are part of the Intellectual Property of Aptiva Labs SAS in the Republic of Colombia and outside of it; its distribution and use is under the authorization of Aptiva Labs SAS. This material is licensed under a Creative Commons CC-BY-NC-ND license.
Red Hat Inc, Red Hat Enterprise Linux, their logos and other identifying elements are registered in the United States of America and other countries.
Linux is a registered trademark of Linus Torvalds in the United States of America and other countries.
XFS is a registered trademark of Silicon Graphics International Corp and its subsidiaries in the United States of America and other countries.
PostgreSQL, MariaDB, Microsoft Windows Server, Oracle, Ubuntu, Debian, CentOs, Ansible are trademarks of their manufacturer owners.
Dedication
This book is dedicated to God, the source of all knowledge and source of all inspiration, who has given me the intellectual capacity to address these issues and to be able to share them with other people.
I dedicate this book to my wife Gina, for her support and motivation in starting and finishing this book.
To my mother, Elsy, for her effort and commitment to make her children good people. To my dad, Neil, in the presence of God, an example of resilience.
To my daughters and nieces, the future of the family.
My family, my support.
Acknowledgments
I want to thank all those who have accompanied me in my professional career in each of the companies where I have been a collaborator, the company of each of them has been for the growth and formation of the background that today allows me to publish this work.
Special recognition for Farid Boudez, Miguel Higuera, Jairo Rodrguez, Fause Rizcala, Fabio Ramrez, Freddy Mosquera, Helmuth Corzo, Edgard Polo and Gerardo Solorzano, who at various moments in life have believed in my professional qualities and have entrusted me with important responsibilities.
Special thanks to Juan Carlos Velez and Liliana Hoyos, for their care and prayers for so many years.
Reader Profile
This book is aimed at:
Table of Contents
About of Author
Fabian Mestre Socarras is a Strategic Consultant in Information Technology and Linux Technical Writer. Systems Engineer with a Postgraduate Degree in Information Technology Management, with RHCSA, RHCVA, ITIL, Xorcom certifications, among others. Implementer of IP Telephony and Data Storage solutions on Linux systems. CEO & Founder at Aptiva Labs SAS where he has developed consulting activities for companies such as Bioagricola del Llano SA ESP, Emdupar SA ESP, LlanoGas SA ESP, Compgenioss SAS, Ejrcito Nacional del Colombia, Electrocom SAS, SINGS SAS, Thomas Processing Systems SAS, AppFuture SAS, among others. Write to the author at fabian.mestre@gmail.com.
About This Document
This document is intended for all those whose task is to administer Linux servers and who in one way or another are searching the Internet for how to develop certain technical procedures, however, they are aware that the information published on the Internet may or may not be true.
The labs developed in this document follow the guide recommended by Red Hat Linux and can be applied in distributions such as Oracle Linux 8.x, Centos 8.x, Rocky Linux, Amazon Linux 2, as well as in any other distribution derived from the base distribution. Red Hat Enterprise Linux 8.x.
RECOVERING ACCESS AS "root" USER
Having to recover the password of the "root" user is an unfortunate event, but it does have a procedure defined for this purpose. Recovering the password of the "root" user is something easy to do when the system administrator is still "logged in" in the console or from any type of terminal; Different is the case when the system has not yet been entered and it is required to perform administration tasks.
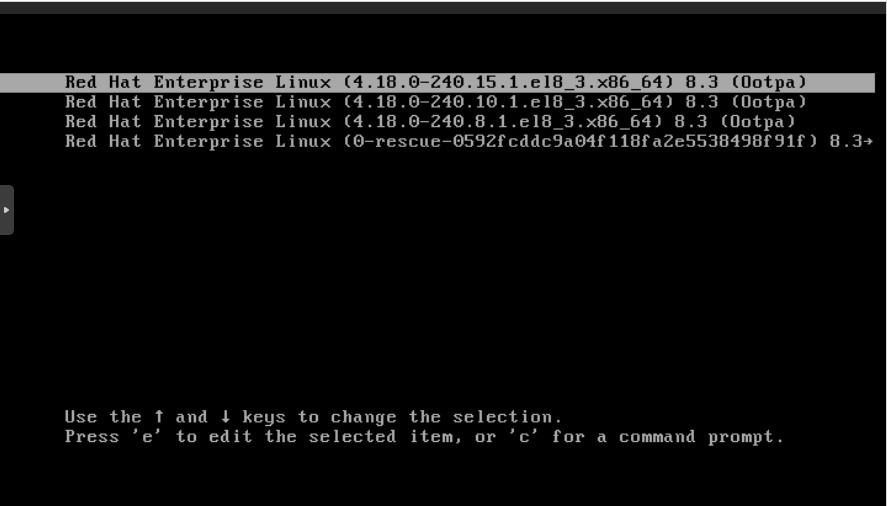
When GRUB2 prompts you to choose a kernel to start, you must stop the kernel startup process by defautl pressing any key on the keyboard; With the positioning keys ("arrows"), you will choose the kernel to execute, in this example "4.18.0-240.15.1" is chosen; Once chosen, press the letter "e", as indicated in the menu below:
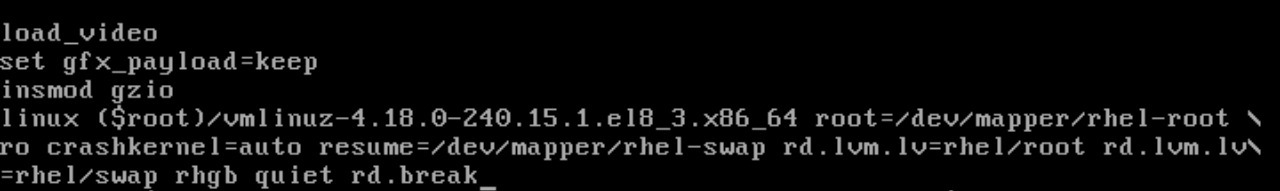
After pressing the letter "e" (edit), locate the line with the word "linux" as the first word of a line; scroll to the end of that line and add a space, as shown below:
This is the line where parameters are sent to the kernel. Go to the end of that line and add the expression "rd.break" to start in console mode. At the end press CTRL + X to boot.
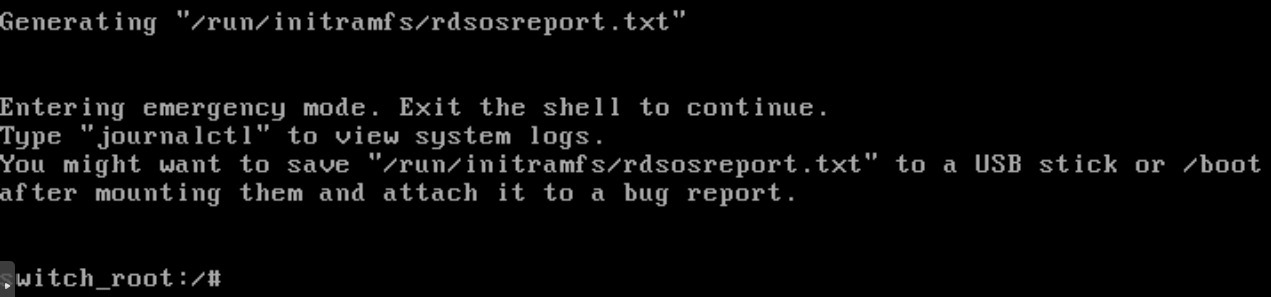
Once the system has booted, Linux has left us at a prompt similar to the one in the following image:
At this moment the standard file system is mounted on / sysroot in read-only form, which makes it necessary to make changes to remount in read-write mode, as follows:
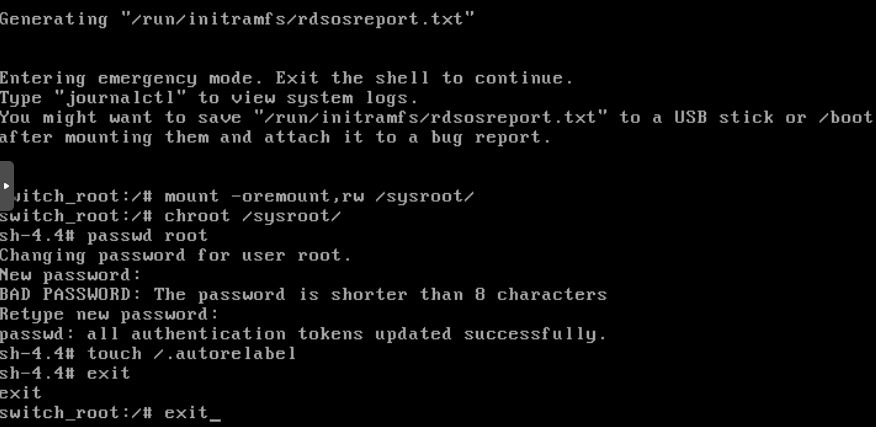
It is necessary to do a Jail (caging of the file system, so that nobody bothers it while the operation is running) of the root file system (/ sysroot) and then change the administrator password.
It is necessary to create the empty file /.autorelabel. Following this, it is necessary to exit the mode where we were (chroot and GRUB mode) by typing exit twice:
This will immediately cause the system to reboot, where initially SELinux will do the job of re-labeling the corresponding contexts where appropriate (files, directories, ports, and processes), if this operating system functionality is enabled.
KERNEL DATA DUMP FOR POST ANALYSIS
To analyze why a system failed, you can use the kdump service to save the contents of system memory for later analysis. In this sub section we will see a brief introduction to kdump using the RHEL Web Console. Kdump is a service that provides a crash-dump mechanism for the kernel. The service allows you to save the contents of the memory. Kdump uses the kexec system call to boot into a second kernel without rebooting, thus capturing the content of the failing kernel and saving the data for analysis. The second kernel resides in a reserved part of memory.
A kernel crash dump may be the only information available in the event of a system failure (a critical error), therefore ensuring that kdump is operational is important in mission critical environments. The procedure below shows you how to use the Kernel Dump tab in the Cockpit tool to configure the amount of memory reserved for the kdump kernel. The procedure also describes how to specify the destination location of the vmcore dump file and how to test its configuration.
Next page