it-ebooks - computer_networks_a_systems_approach_5th_ed
Here you can read online it-ebooks - computer_networks_a_systems_approach_5th_ed full text of the book (entire story) in english for free. Download pdf and epub, get meaning, cover and reviews about this ebook. year: 2018, publisher: iBooker it-ebooks, genre: Computer. Description of the work, (preface) as well as reviews are available. Best literature library LitArk.com created for fans of good reading and offers a wide selection of genres:
Romance novel
Science fiction
Adventure
Detective
Science
History
Home and family
Prose
Art
Politics
Computer
Non-fiction
Religion
Business
Children
Humor
Choose a favorite category and find really read worthwhile books. Enjoy immersion in the world of imagination, feel the emotions of the characters or learn something new for yourself, make an fascinating discovery.
computer_networks_a_systems_approach_5th_ed: summary, description and annotation
We offer to read an annotation, description, summary or preface (depends on what the author of the book "computer_networks_a_systems_approach_5th_ed" wrote himself). If you haven't found the necessary information about the book — write in the comments, we will try to find it.
computer_networks_a_systems_approach_5th_ed — read online for free the complete book (whole text) full work
Below is the text of the book, divided by pages. System saving the place of the last page read, allows you to conveniently read the book "computer_networks_a_systems_approach_5th_ed" online for free, without having to search again every time where you left off. Put a bookmark, and you can go to the page where you finished reading at any time.
Font size:
Interval:
Bookmark:
- 1.1
- 1.2
- 1.2.1
- 1.2.2
- 1.2.3
- 1.2.4
- 1.2.5
- 1.2.6
- 1.3
- 1.3.1
- 1.3.2
- 1.3.3
- 1.3.4
- 1.3.5
- 1.3.6
- 1.3.7
- 1.3.8
- 1.4
- 1.4.1
- 1.4.2
- 1.4.3
- 1.4.4
- 1.4.5
- 1.5
- 1.5.1
- 1.5.2
- 1.5.3
- 1.5.4
- 1.5.5
- 1.6
- 1.6.1
- 1.6.2
- 1.6.3
- 1.6.4
- 1.6.5
- 1.7
- 1.7.1
- 1.7.2
- 1.7.3
- 1.7.4
- 1.7.5
- 1.7.6
- 1.8
- 1.8.1
- 1.8.2
- 1.8.3
- 1.9
- 1.9.1
- 1.9.2
- 1.9.3
- 1.9.4
- 1.9.5
- 1.10
- 1.10.1
- 1.10.2
- 1.10.3
- 1.10.4
- 1.10.5
Most people know the Internet through its applications: the World WideWeb, email, online social networking, streaming audio and video, instantmessaging, file-sharing, to name just a few examples. That is to say, weinteract with the Internet as users of the network. Internet usersrepresent the largest class of people who interact with the Internet insome way, but there are several other important constituencies.
There is the group of people who create the applicationsa groupthat has greatly expanded in recent years as powerful programmingplatforms and new devices such as smartphones have created newopportunities to develop applications quickly and to bring them to alarge market.
Then there are those who operate or manage networksmostly abehind-the-scenes job, but a critical one and often a very complex one.With the prevalence of home networks, more and more people are alsobecoming, if only in a small way, network operators.
Finally, there are those who design and build the devices andprotocols that collectively make up the Internet. That finalconstituency is the traditional target of networking textbooks such asthis one and will continue to be our main focus. However, throughoutthis book we will also consider the perspectives of applicationdevelopers and network operators.
Considering these perspectives will enable us to better understand thediverse requirements that a network must meet. Application developerswill also be able to make applications that work better if theyunderstand how the underlying technology works and interacts with theapplications. So, before we start figuring out how to build a network,let's look more closely at the types of applications that today'snetworks support.
The World Wide Web is the Internet application that catapulted theInternet from a somewhat obscure tool used mostly by scientists andengineers to the mainstream phenomenon that it is today. The Web itselfhas become such a powerful platform that many people confuse it with theInternet (as in "the Interwebs"), and it's a bit of a stretch to saythat the Web is a single application.
In its basic form, the Web presents an intuitively simple interface.Users view pages full of textual and graphical objects and click onobjects that they want to learn more about, and a corresponding new pageappears. Most people are also aware that just under the covers eachselectable object on a page is bound to an identifier for the next pageor object to be viewed. This identifier, called a Uniform ResourceLocator (URL), provides a way of identifying all the possible objectsthat can be viewed from your web browser. For example,
http://www.cs.princeton.edu/llp/index.htmlis the URL for a page providing information about one of this book'sauthors: the string http indicates that the Hypertext TransferProtocol (HTTP) should be used to download the page,www.cs.princeton.edu is the name of the machine that serves thepage, and /llp/index.html uniquely identifies Larry's home page atthis site.
What most web users are not aware of, however, is that by clicking onjust one such URL over a dozen messages may be exchanged over theInternet, and many more than that if the web page is complicated withlots of embedded objects. This message exchange includes up to sixmessages to translate the server name (www.cs.princeton.edu)into its Internet Protocol (IP) address (128.112.136.35),three messages to set up a Transmission Control Protocol(TCP) connection between your browser and this server, four messages foryour browser to send the HTTP "GET" request and the server to respondwith the requested page (and for each side to acknowledge receipt ofthat message), and four messages to tear down the TCP connection. Ofcourse, this does not include the millions of messages exchanged byInternet nodes throughout the day, just to let each other know that theyexist and are ready to serve web pages, translate names to addresses,and forward messages toward their ultimate destination.
Another widespread application class of the Internet is the delivery of"streaming" audio and video. Services such as video on demand andInternet radio use this technology. While we frequently start at awebsite to initiate a streaming session, the delivery of audio and videohas some important differences from fetching a simple web page of textand images. For example, you often don't want to download an entirevideo filea process that might take minutes to hoursbeforewatching the first scene. Streaming audio and video implies a moretimely transfer of messages from sender to receiver, and the receiverdisplays the video or plays the audio pretty much as it arrives.
Note that the difference between streaming applications and the moretraditional delivery of a page of text or still images is that humansconsume audio and video streams in a continuous manner, anddiscontinuityin the form of skipped sounds or stalled videois notacceptable. By contrast, a page of text can be delivered and read inbits and pieces. This difference affects how the network supports thesedifferent classes of applications.
A subtly different application class is real-time audio and video.These applications have considerably tighter timing constraints thanstreaming applications. When using a voice-over-IP application such asSkype or a videoconferencing application, the interactions among theparticipants must be timely. When a person at one end gestures, thenthat action must be displayed at the other end as quickly as possible.
Not quite "as soon as possible"... Human factors research indicates 300 ms is a reasonable upper bound for how much round-trip delaycan be tolerated in a telephone call before humans complain, and a 100-ms delay sounds very good.
When one person tries to interrupt another, the interrupted person needsto hear that as soon as possible and decide whether to allow theinterruption or to keep talking over the interrupter. Too much delay inthis sort of environment makes the system unusable. Contrast this withvideo on demand where, if it takes several seconds from the time theuser starts the video until the first image is displayed, the service isstill deemed satisfactory. Also, interactive applications usually entailaudio and/or video flows in both directions, while a streamingapplication is most likely sending video or audio in only onedirection.
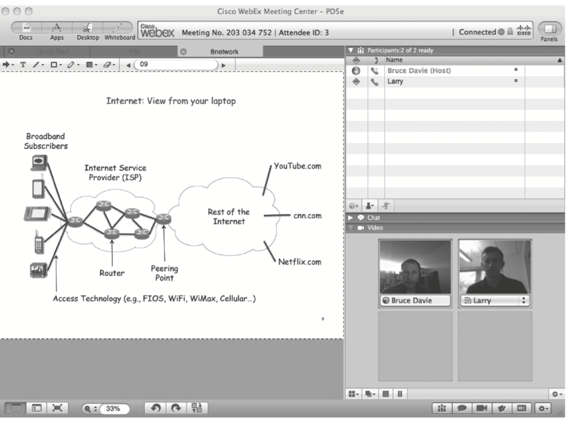 A multimedia application including videoconferencing.
A multimedia application including videoconferencing. Videoconferencing tools that run over the Internet have been around nowsince the early 1990s but have achieved much more widespread use in thelast couple of years, as higher network speeds and more powerfulcomputers have become commonplace. An example of one such system isshown in . Just as downloading a web pageinvolves a bit more than meets the eye, so too with video applications.Fitting the video content into a relatively low bandwidth network, forexample, or making sure that the video and audio remain in sync andarrive in time for a good user experience are all problems thatnetwork and protocol designers have to worry about. We'll look atthese and many other issues related to multimedia applications laterin the book.
Font size:
Interval:
Bookmark:
Similar books «computer_networks_a_systems_approach_5th_ed»
Look at similar books to computer_networks_a_systems_approach_5th_ed. We have selected literature similar in name and meaning in the hope of providing readers with more options to find new, interesting, not yet read works.
Discussion, reviews of the book computer_networks_a_systems_approach_5th_ed and just readers' own opinions. Leave your comments, write what you think about the work, its meaning or the main characters. Specify what exactly you liked and what you didn't like, and why you think so.